Topic
This article discusses policy management for NinjaOne NMS.
Environment
- Network monitoring services
- NinjaOne policies
Description
Devices discovered by the NMS agent can be assigned a device role that dictates the policy through which they are managed. The NMS agent must be installed on the device for policy management to take effect. For instructions on setting up NMS, refer to NMS: Setup Installation and Configuration.
Index
- Prerequisites
- Create a Custom Role for a Policy
- Create New NMS Policies
- NMS Policy Settings and Configuration
- Other Notes about NMS Policy Conditions
- Assign Default NMS Policies for an Organization
Prerequisites
You must set up monitoring for configuration backup, SNMP traps, Syslog, and/or NetFlow locally on your devices. Configuration steps differ depending on your device's vendor and model, so we recommend referring to your manufacturer's documentation for assistance with setup.
- NinjaOne supports configuration backup monitoring on Hewlett-Packard and Cisco devices.
- NinjaOne supports NetFlow/jFlow/sFlow/IPFIX monitoring.
- SonicWall requires App Visualization licensing to utilize flow reporting.
Create a Custom Role for a Policy
You can create NMS policies from custom device roles. When you create the new policy, the configuration modal allows you to select the custom role. For more information, refer to custom device roles. To learn more about creating and managing device roles, refer to the Device Roles guide.
Add a new role
To add a new role from any of the NMS roles displayed on the page, place your cursor over the row and click Add.
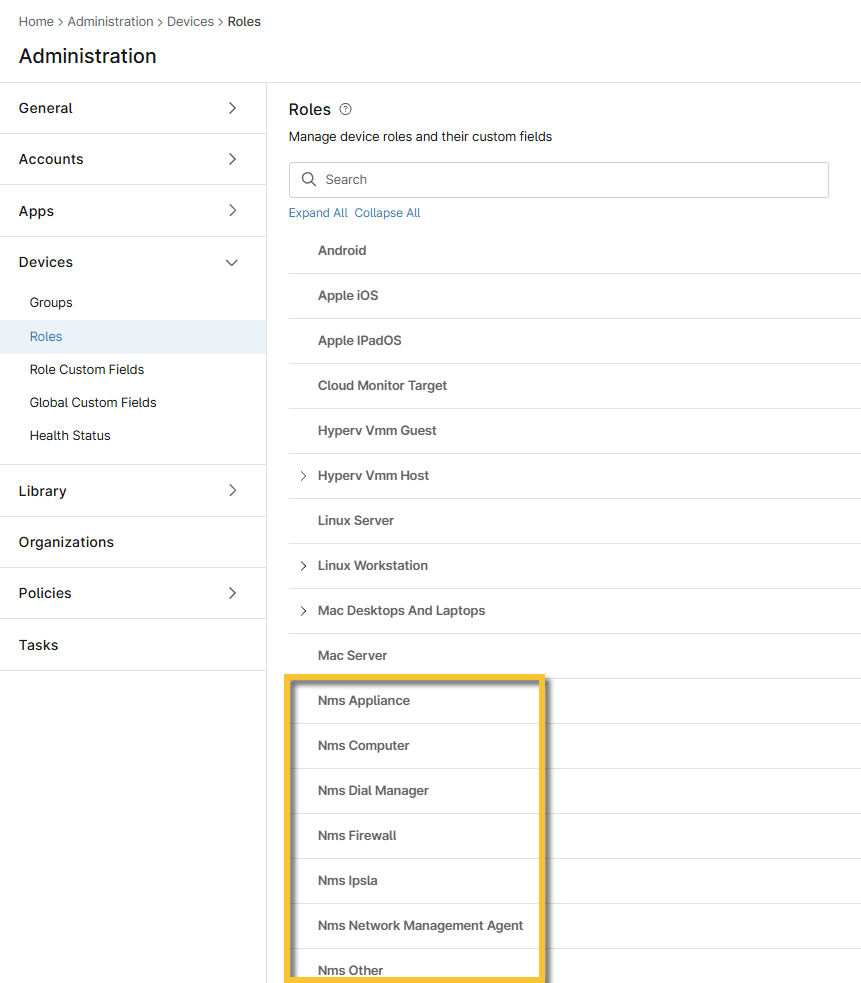
Figure 1: NMS options (click to enlarge)
Create New NMS Policies
- Navigate to Administration → Policies → NMS Policies, then click Create New Policy in the top right corner of the window.
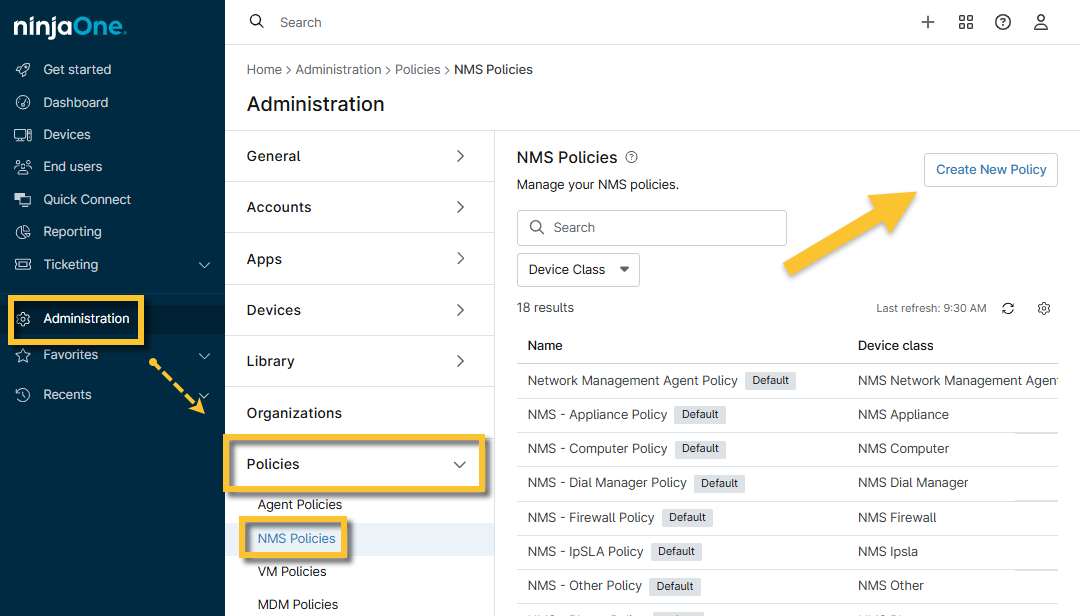
Figure 2: Create New Policy (click to enlarge)
- Assign the new policy a name and an optional description, then click the Role drop-down menu and select NMS. A new drop-down labeled NMS Role will appear. Here, you can select the device role.
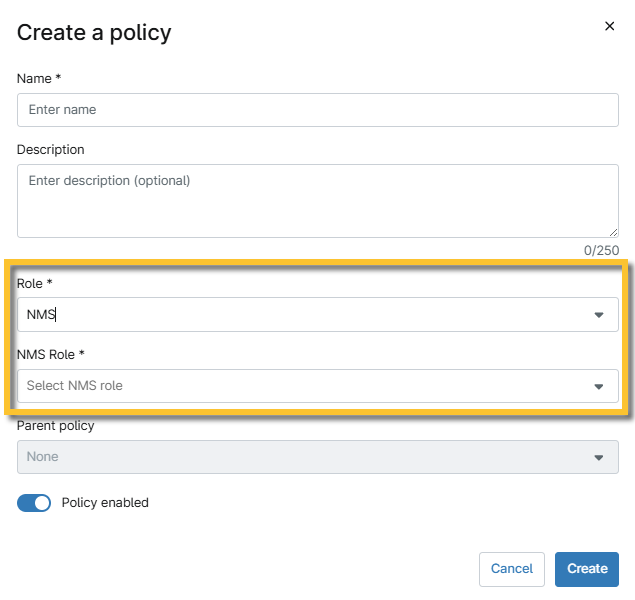
Figure 3: "Create a policy" modal for NMS role (click to enlarge)
- Click Save to complete the new policy creation and assign policy settings.
Copy an Existing Policy
- To make a copy of an existing policy, place your cursor over the policy you wish to copy and click the ellipsis button on the right side. Select Copy.
- Name the policy and click Save, then make any changes to the configured settings that you require.
NMS Policy Settings and Configuration
This section goes over each tab in the NMS policy and the settings that are available for configuration.
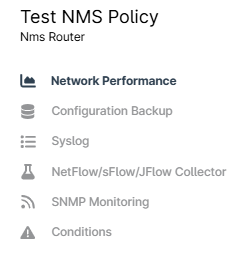
Figure 4: Policy configuration page sections (click to enlarge)
Select a section below to learn more:
Network Performance
These settings allow you to monitor network performance using any of the following methods:
| Tab Name | Description |
|---|---|
| DNS | Monitors the Domain Name System (DNS) at a specified interval and timeout (in milliseconds) as well as DNS NetBIOS Name, LMHost, Host, or Forward DNS resolution. These policy settings are hard-coded in the NMS delegate and cannot be changed. |
| Ping | Monitors ping at a specified interval and timeout (in seconds). You can also monitor the packet TTL, pings per node, and the delay between pings (in milliseconds). |
| Port | Monitors selected ports at a specified interval and timeout (in milliseconds). |
| HTTP | Monitors HTTP (Hypertext Transfer Protocol) or HTTPS (secure) for selected port at a specified interval and timeout (in seconds). |
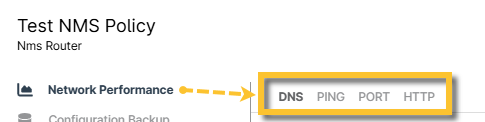
Figure 5: Network Performance Tabs (click to enlarge)
Configuration Backup
These settings let you manage the configuration backup for HP or Cisco devices. You can perform the configuration backup at a specified interval and timeout (in seconds), specify a file transfer timeout to monitor for (in seconds), and choose whether to monitor the running config or the startup config.
For configuration backup to work, you must ensure the Telnet/SSH credentials are set up properly. You can do this by going to any organization configuration page and adding or editing the data under Credentials. The Edit and Delete options only display when you move your cursor over the row.
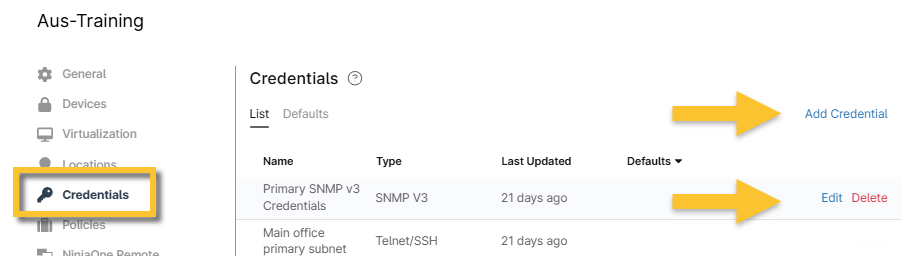
Figure 6: Add, edit, or delete credentials (click to enlarge)
Syslog
These settings allow you to choose different monitoring facilities and severities within the syslog on the device. The system will not take into account any facilities and severities you uncheck in the conditions.
NinjaOne discards the following syslog activities by default:
- Facility: User
- Severity: Debug, Info, Notice
To obtain messages or alerts for the above, you must configure the alert manually from the Conditions section of the NMS policy. Select the "Syslog" condition and then select which messages you want to receive from the Facilities and/or Severities fields.
NetFlow/sFlow/JFlow Collector:
These settings govern the type of NetFlow traffic you'd like to monitor, any IP (Internet Protocol) addresses from which you'd like to discard data, and the flow noise configuration.
NinjaOne supports several different traffic protocols:
- NetFlow (NetFlow 5, NetFlow 9)
- J-Flow
- sFlow (sFlow 2, sFlow 5)
- IPFIX (NetFlow 10)=
SNMP Monitoring
These settings allow you to monitor basic SNMP (Simple Network Management Protocol) data (like CPU, memory, Disk, or Network Adapter). When adding a monitor, NinjaOne presents the options pulled from the SNMP Library. Refer to NMS: Custom SNMP to learn more.
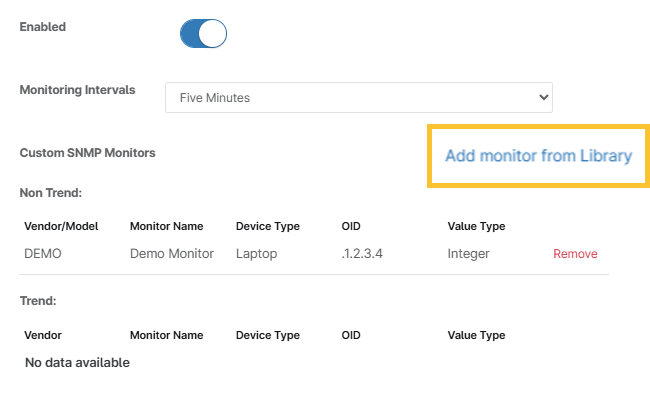
Figure 7: Add monitor from Library (click to enlarge)
Conditions
Choose from any of the following available conditions to monitor with this policy:
| Condition Name | Description |
|---|---|
| Processor | This triggers if the processor utilization is greater than, less than, or equal to a threshold percent defined in the condition dialog box. You can choose between hit count or duration for the type. |
| Memory | This triggers if the memory utilization is greater than, less than, or equal to a threshold percent defined in the condition dialog box. You can choose between hit count or duration for the type. |
| Disk Usage | (Firewall and VM Host policy only) This triggers if the processor utilization is greater than, less than, or equal to a threshold percent defined in the condition dialog box. |
| Network Adapter Traffic | Triggers if the ingoing or outgoing network adapter traffic is greater than, less than, or equal to a threshold, which you can specify in numerous units. You can choose between hit count or duration for the type. |
| Network Adapter Traffic Percent | Triggers if the ingoing or outgoing network adapter traffic is greater than, less than, or equal to a threshold percent. You can choose between hit count or duration for the type. |
| Network Adapter Status | Monitors whether a network adapter is in a specified status. |
| Network Adapter Status Change | Monitors when a network adapter changes to or from a specified status. |
| Ping Latency | Triggers if the ping latency is greater than, less than, or equal to a certain threshold percent. You can choose between hit count or duration for the type. |
| Ping Packet Loss | Triggers if the ping packet loss is greater than, less than, or equal to a certain threshold percent for a specified duration of time. |
| Ping Response | Monitors if a ping receives a response after a specified number of attempts. |
| Http | Monitors for selected status codes, as well as the presence of specified content text. |
| Ports | Monitors the status of specified ports. |
| Syslog | Monitors the syslog for the specified logic type (and/or), message, facilities, and severities. Important Note: The last three options under Severities could result in a large number of alerts. |
| Device Down | Triggers if the device goes down for the duration of time specified in the condition dialog box. |
| Configuration File | Monitors for changes to the configuration file. Specify whether you'd like to monitor for content being added or removed, specific text to monitor for, or specific text to ignore. Important Note: Under the Configuration Backup tab of the NMS policy, you can specify the type of configuration you want to monitor. You can choose between Startup-config and Running-config. |
| SNMP Trap | Monitors if the system receives any trap, a trap containing a specific OID, or a trap value containing a specific target string. |
NMS Condition Interval Dependency
The following conditions depend on the SNMP Monitoring Interval:
- Custom SNMP condition
- Device Down condition
- Memory condition
- All network adapter conditions
- Processor condition
- System Uptime condition
Other Notes about NMS Policy Conditions
Reset interval
When creating conditions in your NMS policies, you can specify a reset interval that dictates the amount of time that will pass until the condition automatically resets (the alert will be cleared from the device).

Figure 8: NMS condition Reset Interval (click to enlarge)
Notify Technicians
You will also have the option to enable notifications to be sent when a condition is triggered.
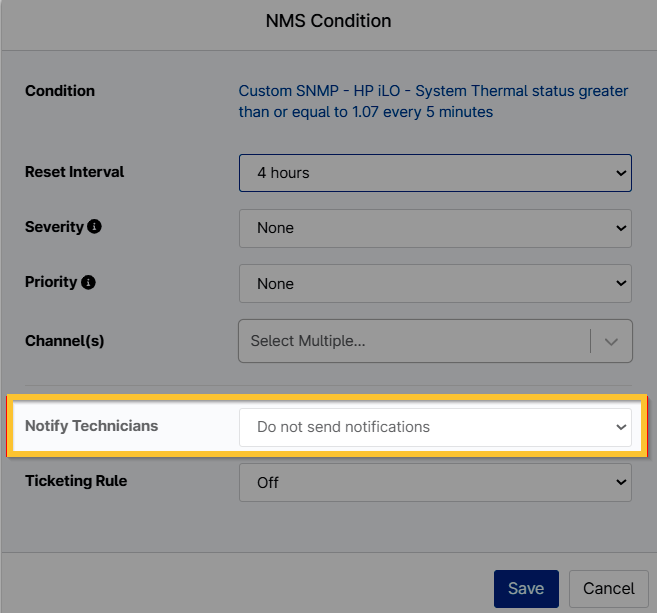
Figure 9: NMS condition → Notify Technicians (click to enlarge)
Assign Default NMS Policies for an Organization
- Navigate to the organization's editor (Administration → Organizations).
- Select Policies on the left side of the window, then open the NMS Policies tab at the top of the page.
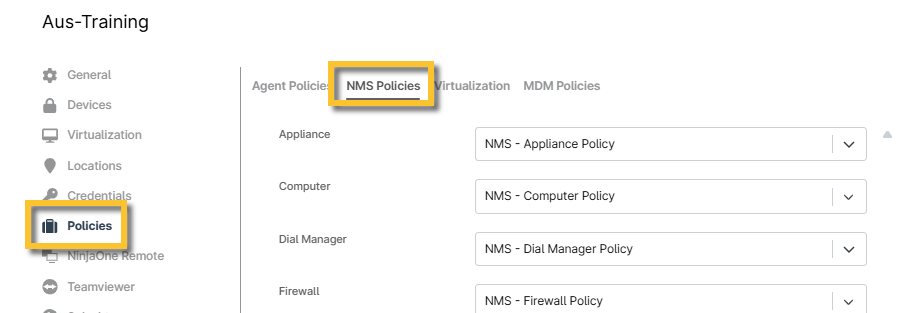
Figure 10: NinjaOne organization-level NMS Policies (click to enlarge)
- Select the desired default policies from the drop-down menus, then click Save in the top right corner.
Once saved, policies are automatically assigned to NMS devices under this organization according to the role they are assigned.