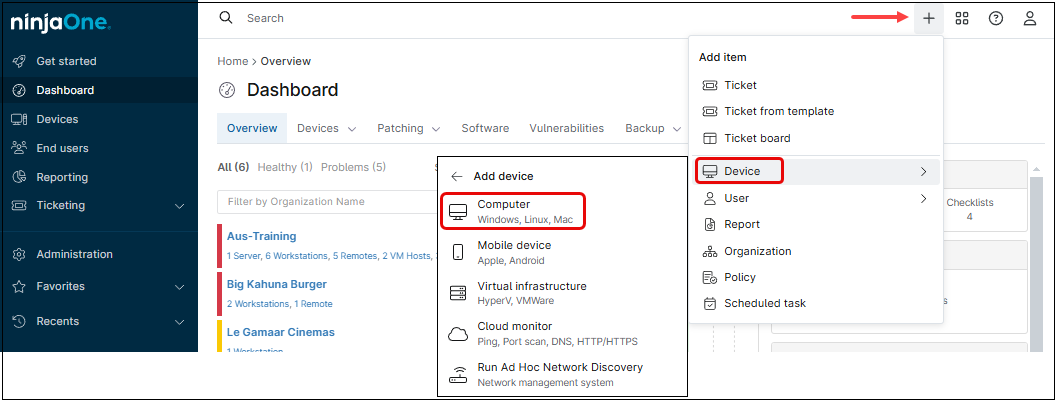
What is macOS MDM?
macOS MDM is a framework provided by Apple that allows IT administrators to remotely manage and configure macOS devices – Mac Desktops, laptops and servers. Compared to traditional RMM solutions, macOS MDM provides deeper control over macOS system settings, security policies, and app management.
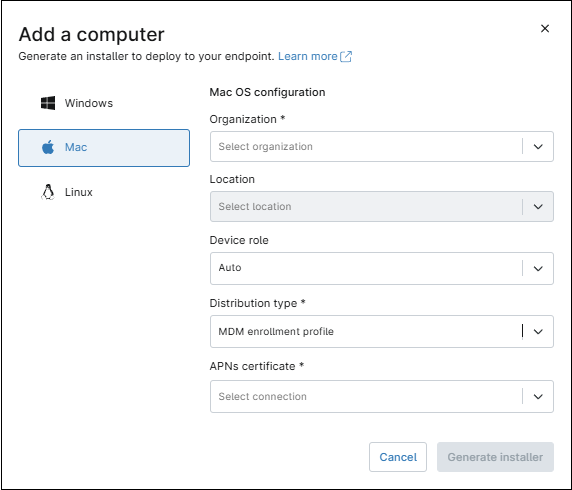
macOS MDM allows different enrollment methods for employee-owned and company-owned devices.
Employee-owned devices are enrolled manually by installing an enrollment profile. End users can remove the profile, which will also remove all managed settings and apps.
Company-owned devices are generally enrolled using Zero-Touch Enrollment (ZTE) through Automated Device Enrollment (ADE) via Apple Business Manager or Apple School Manager. In most cases, end users cannot remove the device from management
Unlike iOS on mobile phones, where some settings apply only to supervised devices and others to unsupervised devices, macOS applies all configured settings to the device regardless of the enrollment method used. Whether a Mac is enrolled manually with an enrollment profile or through ADE with ZTE, all assigned macOS MDM settings will take effect uniformly.
How does macOS MDM work in NinjaOne?
Using macOS MDM in NinjaOne is very simple. macOS agent policies include an additional ‘MDM’ tab, which contains multiple categories of configuration settings.
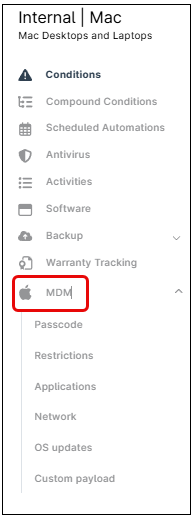
Within each category, administrators can enable or disable specific options, allowing for granular control over macOS devices. These settings help enforce security policies, manage system preferences, and configure restrictions as needed. See below for a brief explanation of these categories.
Passcode. This category controls passcode settings, like complexity, number of failed attempts, passcode length, history, etc.
Restrictions. This category controls a series of restrictions that can be applied to the device, these restrictions are divided into 6 subcategories:
- Functionality
- Application
- Security & Privacy
- Media
- iCloud
- Classroom
Applications. This category allows you to integrate with a content token from Apple Business Manager or Apple School Manager and deploy managed applications to devices.
Network. Here, IT administrators can set up Wi-Fi network and proxy settings without end user intervention.
OS updates. This category defines how end users can install software updates and defines enforced OS versions.
Privacy preferences. This category controls how applications can access system resources, such as the microphone, camera, screen recording, files, etc., without end user intervention.
System extensions. System extensions allow macOS apps to use advanced OS feature sets, such as creating device drivers, network extensions (DNS proxies, VPNs, or content filters), and endpoint security extensions to monitor and block system events.
Custom payload. This allows IT administrators to apply settings not natively available in NinjaOne. This is useful for advanced configurations or when Apple introduces new settings that NinjaOne hasn’t yet integrated.
What is the detailed list of settings that can be controlled with macOS MDM in NinjaOne?
In NinjaOne, macOS MDM policy is divided into multiple categories, which are explained in the following lines:
Passcode
When enabled, a passcode is enforced on the device, regardless of whether other unlock methods are set up. For example, if the end user configures fingerprint authentication, they can unlock the device using their fingerprint. However, once the grace period (defined by ‘Maximum grace period for device lock’) expires, the passcode will be required to unlock the device. This category also defines passcode settings like complexity, history, etc. See the table below to see the different settings controlled by this category.
| Setting | Definition |
| Require alphanumeric value | Switch that, when activated, enforces the use of both numbers (123) and alphabetical characters (Abc) in the passcode. The “Require alphanumeric value” and “Allow simple passcode” switches are mutually exclusive. |
| Allow simple passcode | Switch that, when activated, allows entry of a simple passcode. Simple passcodes may contain repeated characters or increasing or decreasing characters (123 or CBA).). The “Require alphanumeric value” and “Allow simple passcode” switches are mutually exclusive. |
| Maximum number of failed attempts | The number of allowed failed attempts when entering the passcode at the device’s lock screen. After six failed attempts, a time delay is imposed before a passcode can be entered again. The delay increases with each attempt. If a user’s failed attempts exceed the number set in the policy, then the device will be wiped. |
| Maximum passcode age (days) | The number of days for which the passcode can remain unchanged. After this number of days, the user is required to change the passcode before the device is unlocked. If set to zero (0), then the passcode will not expire. |
| Maximum grace period for device lock | The period to unlock the device without entering a passcode. When the grace period expires, the device is auto locked by the system and the user will be prompted to enter their passcode. |
| Minimum number of complex characters | A complex (or ‘special’) character is a character other than a number or a letter, such as & % $ #. |
| Minimum passcode length | Sets the minimum number of characters the password can have. This parameter is independent of the optional ‘Minimum number of complex characters’ setting. |
| Passcode history | The number set here determines how many previous passwords a user must avoid reusing when creating a new one. For example, if the number is set to 3, a user cannot reuse their last three passwords when setting a new one. |
| Maximum auto-lock (minutes) | The number of minutes for which the device can be idle before it gets locked by the system. When this limit is reached, the device is locked, and the passcode must be entered. The user can edit this setting on their device, but the value cannot exceed the policy setting. |
Restrictions
Through this category, there is a series of restrictions that can be applied, they are divided into Functionality, Application, Network, Security & Privacy, Media, iCloud and Classroom. Some restrictions apply to supervised, others to unsupervised. All restrictions are displayed under their appropriate category and can be filtered using the Category dropdown at the top of the page; they can be enabled or disabled by checking/unchecking the box next to the restriction name. The policy configuration will be sent to all devices managed by the policy. Refer to the sections below for an explanation of each restriction.
Functionality restrictions
The table below explains the functionality restrictions
| Setting | Category | Description |
| Allow modifying account settings | Functionality | If unchecked, the system disables modification of accounts such as Apple Accounts and Internet-based accounts such as Mail, Contacts, and Calendar. |
| Allow Handoff | Functionality | If unchecked, the system disables activity continuation. Available in macOS 10.15 and later. |
| Allow AirDrop | Functionality | If unchecked, the system disables AirDrop. Available in macOS 10.13 and later. |
| Allow AirPlay | Functionality | If unchecked, the system disables incoming AirPlay requests. Available in macOS 12.3 and later. |
| Allow Apple personalized advertising | Functionality | If unchecked, the system limits Apple personalized advertising. Available in macOS 12 and later. |
| Allow modifying Bluetooth settings | Functionality | If unchecked, the system prevents modification of Bluetooth settings. Available in macOS 13.0 and later. |
| Allow Camera | Functionality | If unchecked, the systems disables the camera and removes its icon from the Home screen, and users are unable to take photographs. Available in macOS 10.11 and later. |
| Allow Content Catching | Functionality | If unchecked, the system disables content caching. Available in macOS 10.13 and later |
| Allow Definition Lookup | Functionality | If unchecked, the system disables definition lookup. Available macOS 10.11 and later. |
| Allow modifying device name | Functionality | If unchecked, the system prevents the user from changing the device name. Available in macOS 14 and later. |
| Allow submitting diagnostic and usage data to Apple | Functionality | If unchecked, the system prevents the device from automatically submitting diagnostic reports to Apple. Available in macOS 10.13 and later. |
| Allow dictation | Functionality | If unchecked, the system disallows dictation input. Available in macOS 10.13 and later. |
| Allow Erase All Content and Settings | Functionality | If unchecked, the system disables the Erase All Content and Settings option in the Reset UI. Available in macOS 12 and later. |
| Allow Find My Device | Functionality | If unchecked, the system disables Find My Device in the Find My app. Available in macOS 10.15 and later. |
| Allow Find My Friends | Functionality | If unchecked, the system disables Find My Friends in the Find My app. Available in macOS 10.15 and later. |
| Allow iTunes file sharing | Functionality | If unchecked, the system disables iTunes file sharing services. Available in macOS 10.13 and later. |
| Allow screenshots and screen recording | Functionality | If unchecked, the system disables saving a screenshot of the display and capturing a screen recording. It also disables the Classroom app from observing remote screens. Available in macOS 10.14.4 and later. |
| Allow Siri Suggestions | Functionality | If unchecked, the system disables Spotlight Internet search results in Siri Suggestions. Available in macOS 10.11 and later. |
| Allow user installation of configuration profiles | Functionality | If unchecked, the system prohibits the user from installing configuration profiles and certificates interactively. Available in macOS 13 and later. |
| Allow Universal Control | Functionality | If unchecked, the system disables Universal Control. Available in macOS 13 and later. |
| Allow USB accessories while device is locked | Functionality | If unchecked, the systems allows new USB and Thunderbolt accessories and SD cards to connect without authorization. If the system has Lockdown mode checked, it ignores this value. Available in macOS 13 and later.. |
| Allow modifying Wallpaper | Functionality | If unchecked, the system prevents changing the wallpaper. Available in macOS 10.13 and later. |
| Force on-device only dictation | Functionality | If checked, the system disables connections to Siri servers for the purposes of dictation. Available in macOS 14 and later. |
| Allow Genmoji | Functionality | If unchecked, prohibits creating new Genmoji. Available in macOS 15 and later. |
| Allow Image Playground | Functionality | If unchecked, prohibits the use of image generation. Available in macOS 15 and later. |
| Allow Writing Tools | Functionality | If unchecked, prevents the use of Apple Intelligence writing tools. Available in macOS 15 and later. |
| Allow iPhone mirroring | Functionality | If unchecked, prevents the system from mirroring any iPhone. Available in macOS 15 and later. |
| Allow mail summary | Functionality | If unchecked, prevents the ability to create summaries of email messages manually. This doesn’t affect automatic summary generation. Available in macOS 15.1 and later. |
| Allow Remote Management Sharing modification | Functionality | If unchecked, the system prevents modifying the Remote Management Sharing setting in System Settings. Available in macOS 14 and later. |
| Allow bluetooth sharing modification | Functionality | If unchecked, the system prevents modifying Bluetooth settings in System Settings. Available in macOS 14 and later. |
| Allow File Sharing modification | Functionality | If unchecked, the system prevents modifying File Sharing setting in System Settings. Available in macOS 14 and later. |
| Allow Internet Sharing modification | Functionality | If unchecked, the system prevents modifying the Internet Sharing setting in System Settings. Available in macOS 14 and later. |
| Allow local user creation | Functionality | If unchecked, the system prevents creating new users in System Settings. Available in macOS 14 and later. |
| Allow Printer Sharing modification | Functionality | If unchecked, the system prevents modifying Printer Sharing settings in System Settings. Available in macOS 14 and later. |
| Allow Remote Apple Events Sharing modification | Functionality | If unchecked, the system prevents modifying Remote Apple Events Sharing settings in System Settings. Available in macOS 14 and later. |
| Allow Startup Disk modification | Functionality | If unchecked, the system prevents modification of Startup Disk settings in System Settings. Available in macOS 14 and later. |
| Allow Time Machine backup | Functionality | If unchecked, the system prevents modification of Time Machine settings in System Settings. Available in macOS 14 and later. |
| Allow external intelligence integrations | Functionality | If unchecked, prevents the use of external, cloud-based intelligence services with Siri. Available in macOS 15.2 and later. |
| Allow external intelligence integrations sign-in | Functionality | If unchecked, forces external intelligence providers into anonymous mode. If a user is already signed in to an external intelligence provider, applying this restriction will cause them to be signed out when the next request is attempted. Available in macOS 15.2 and later. |
Application restrictions
The table below explains the application restrictions.
| Setting | Category | Description |
| Allow Game Center | Application | If unchecked, the system disables Game Center, and the system removes its icon from the Home screen. Available in macOS 10.13 and later.. |
| Allow adding Game Center friends. Requires “Allow Game Center” to be enabled. | Application | if unchecked, the system prohibits adding friends to Game Center. Available in macOS 10.13 and later.. |
| Allow multiplayer gaming. Requires “Allow Game Center” to be enabled. | Application | If unchecked, the system prohibits multiplayer gaming. Available in macOS 10.13 and later. |
| Allow Siri | Application | If unchecked, the system disables Siri. Available in macOS 12 and later. |
| Enable Siri profanity filter assistant. Requires “Allow Siri” to be enabled. | Application | If checked, the system forces the use of the profanity filter for Siri and dictation. Available in macOS 10.13 and later. |
| Allow iBooks Store | Application | If unchecked, the system removes the Book Store tab from the Books app. Available in macOS 15 and later. |
| Allow Apple Music | Application | If unchecked, the system disables the Music service, and the Music app reverts to classic mode. Available in macOS 10.12 and later. |
| Enable Autofill on Safari. | Application | If unchecked, the system disables Safari AutoFill for passwords, contact info, and credit cards and also prevents using the Keychain for AutoFill. The system still allows third-party password managers, and apps can use AutoFill. Available in macOS 10.13 and later. |
Security & privacy restrictions
The table below explains the Security & Privacy restrictions.
| Setting | Category | Description |
| Allow auto unlock | Security & Privacy | If unchecked, the system disallows auto unlock. Available in macOS 10.12 and later. |
| Allow Touch ID / Face ID to unlock device | Security & Privacy | If unchecked, the system prevents Touch ID or Face ID from unlocking a device. Available in macOS 10.12.4 and later. |
| Allow modifying passcode | Security & Privacy | If unchecked, the system prevents adding, changing, or removing the passcode. Available in macOS 10.13 and later. |
| Allow modifying Touch ID / Face ID. Requires “Allow modifying passcode” to be enabled. | Security & Privacy | If unchecked, the system prevents the user from modifying Touch ID or Face ID. Available in macOS 14 and later. |
| Allow password autofill | Security & Privacy | If unchecked, the system disables the AutoFill Passwords feature in iOS, with Keychain and third-party password managers, prompting the user to use a saved password in Safari or in apps, automatic strong passwords, and suggesting strong passwords to users. However, the system doesn’t prevent AutoFill for contact info and credit cards in Safari. Available in macOS 10.14 and later. |
| Allow proximity based password sharing requests | Security & Privacy | If unchecked, the system disables requesting passwords from nearby devices. Available in macOS 10.14 and later. |
| Allow password sharing | Security & Privacy | If unchecked, the system disables sharing passwords with the Airdrop Passwords feature. Available in macOS 10.14 and later. |
| Enforced Fingerprint Timeout (seconds) | Security & Privacy | The value, in seconds, after which the fingerprint unlock requires a password to authenticate. The default value is 48 hours. Available in macOS 12 and later. |
| Bypass user notification when using screen capture | If checked, then the system bypasses the presentation of a screen capture alert. Available in macOS 15.1 and later. |
Media restrictions
The table below explains the Media restrictions.
| Setting | Category | Enrollment | Description |
| Allow explicit sexual content in Apple Books | Media | Unsupervised | If unchecked, the system prevents the user from downloading Apple Books media that’s tagged as erotica. Available in macOS 15 and later. |
| Allow playback of explicit music, podcast & iTunes U media | Media | Supervised | If unchecked, the system hides explicit music or video content purchased from the iTunes Store. The system marks explicit content as such by content providers, such as record labels, when sold through the iTunes Store. Explicit content in the News and Podcast apps is also hidden. Available in macOS 15 and later. |
| Allowed content ratings – Apps | Media | Unsupervised | The maximum level of app content allowed on the device. Options are:
|
| Allowed content ratings – Movies | Media | Unsupervised | The maximum level of movie content allowed on the device. Options are:
|
| Allowed content ratings – TV Shows | Media | Unsupervised | The maximum level of TV content allowed on the device. Options are:
|
| Allow Media Sharing modification | Media | Unsupervised | If unchecked, prevents modification of Media Sharing settings. Available in macOS 15.1 and later. |
iCloud restrictions
The table below explains the iCloud restrictions for macOS policies.
| Setting | Category | Description |
| Allow iCloud bookmark | iCloud | If unchecked, the system disables iCloud Bookmark sync. Available in macOS 10.12 and later. |
| Allow iCloud Calendar | iCloud | If unchecked, the system disables iCloud Bookmark sync. Available in macOS 10.12 and later. |
| Allow iCloud Desktop and Document | iCloud | If unchecked, the system disables iCloud Calendar services. Available in macOS 10.12 and later. |
| Allow iCloud Keychain sync | iCloud | If unchecked, the system disables iCloud keychain synchronization for personal Apple Accounts. Available in macOS 10.12 and later. |
| Allow iCloud Mail | If unchecked, the system disables iCloud Mail services. Available in macOS 10.12 and later. | |
| Allow iCloud Notes | If unchecked, the system disables iCloud Notes services. Available in macOS 10.12 and later. | |
| Allow iCloud Photo Library | iCloud | If unchecked, the system disables iCloud Photo Library for personal Apple Accounts. The system removes any photos from local storage that aren’t fully downloaded from iCloud Photo Library to the device. Available in macOS 10.12 and later. |
| Allow iCloud Private Relay | iCloud | If unchecked, the system disables iCloud Private Relay for personal Apple Accounts. Available in macOS 12 and later. |
| Allow iCloud Reminder | iCloud | If unchecked, the system disables iCloud Reminder services. Available in macOS 10.12 and later. |
| Allow cloud document sync | iCloud | If unchecked, the system disables document and key-value syncing to iCloud for personal Apple Accounts. Available in macOS 10.11 and later. |
| Allow iCloud Freeform | iCloud | If unchecked, the system disallows iCloud Freeform services. Available in macOS 14 and later. |
Classroom restrictions
The table below explains the classroom restrictions.
| Setting | Category | Description |
| Allow AirPlay screen view | Classroom | If unchecked, the system disables remote screen observation by the Classroom app. Nest this key beneath ‘allowScreenShot’ as a subrestriction. If ‘allowScreenShot’ is unchecked, the Classroom app doesn’t observe remote screens. Available in macOS 10.14.4 and later. |
| Allow Classroom screen view without prompting. Requires “Allow AirPlay screen view” to be enabled. | Classroom | If checked, a student enrolled in a managed course through the Classroom app automatically gives permission to that course teacher’s requests to observe the student’s screen without prompting the student. Available in macOS 10.14.4 and later. |
| Automatically join Classroom classes without prompting | Classroom | If checked, the system automatically gives permission to the teacher’s requests without prompting the student. Requires a supervised device. Available in macOS 10.14.4 and later. |
| Require teacher permission to leave Classroom app unmanaged classes | Classroom | If checked, a student enrolled in an unmanaged course through Classroom needs to request permission from the teacher to leave the course. Available in macOS 10.14.4 and later. |
| Allow Classroom to lock apps or the device without prompting | Classroom | If checked, the system allows the teacher to lock apps or the device without prompting the student. Available in macOS 10.14.4 and later. |
Applications
This category controls which applications will be force-installed on Mac devices. Note that only apps distributed through Apple Apps and Books and synced from ABM via a content token will be available. As such, this category does not replace other software installation methods that use installation packages or the software option in the policy; rather, it complements them.
Follow the steps below to add apps.
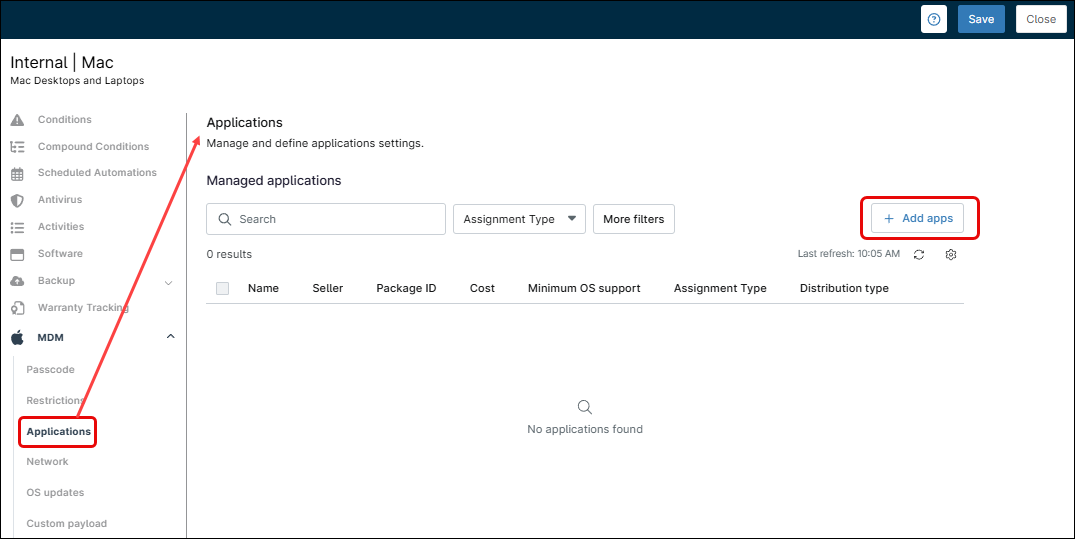
1. Click + Add apps.
2. Click the desired application from the list. A dialog box will appear.
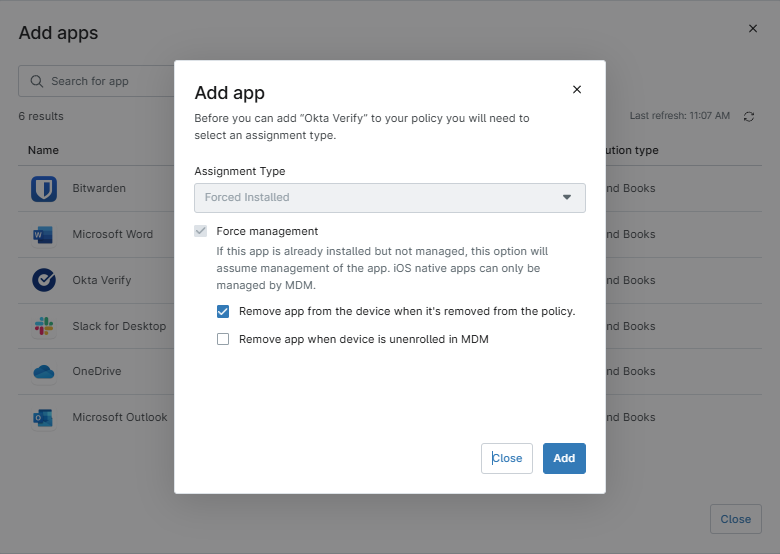
3. Select whether “Remove app from the device when it’s removed from the policy.”
Note: If you opt to remove the app when a device is removed from a policy, this function also applies when you switch a device’s policy under the Settings tab on the device dashboard if the new policy does not also have the app included.
4. Select whether “Remove app when device is unenrolled in MDM.”
5. Click Add. You can continue adding applications, once you´re done,
6. Click Save on the upper right side of the screen. Enter your MFA response method and close.
The app(s) will now appear under Managed Applications, displaying its details, assignment type and distribution type, which will always be “Apps and Books”.
Network
In this category, device´s network settings can be configured, like Proxy and Wi-Fi networks. Multiple Wi-Fi networks can be added, but only one proxy.
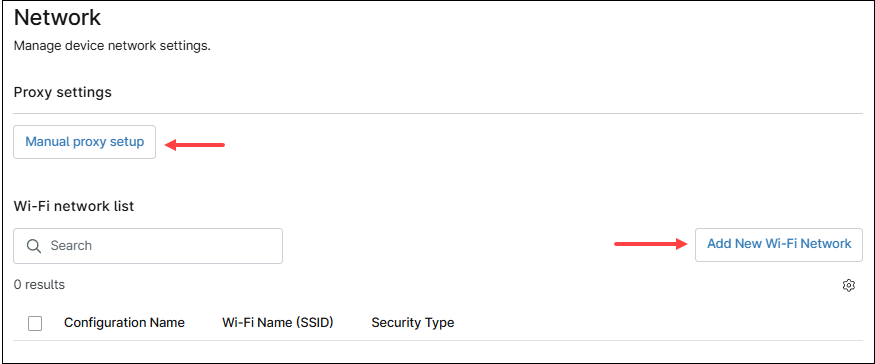
Proxy
Use the Manual proxy setup button to configure proxy settings. This action will open the Manual Proxy Setup dialog box.
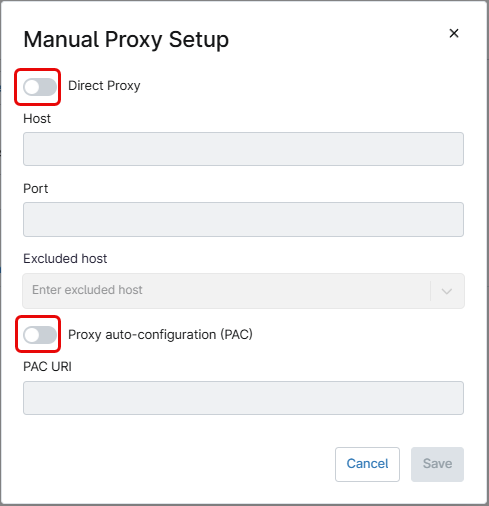
Turn on the Direct Proxy switch to manually enter the proxy configuration information – Host name and port.
Turn on the Proxy auto-configuration (PAC) switch to enter the URL for the PAC file.
Host names can be excluded from the proxy by writing the name under the Excluded host field and pressing enter.
After entering the information, click the blue Save button. This will add the proxy settings used by the mobile device. Once added, the information can be edited or removed.
Wi-Fi Networks
Use the Add new Wi-Fi Network button to configure a new Wi-Fi network. This action will open the Wi-Fi Network Dialog Box, then follow the next steps to configure a new Wi-Fi network.
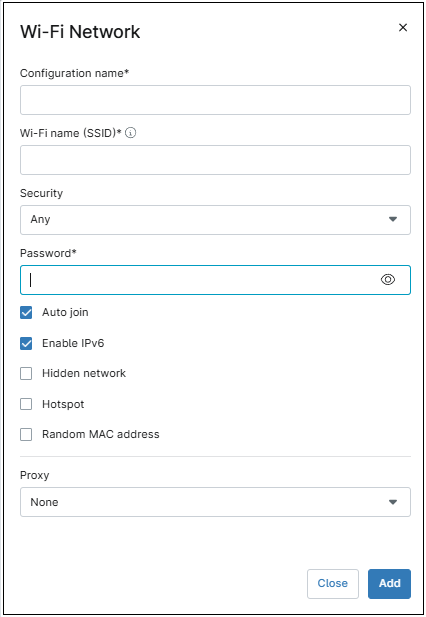
- Enter a configuration name (a friendly name of your choice to distinguish this Wi-Fi network).
- Enter the SSID.
- Under Security, select the encryption method, options are: ‘WEP-PSK‘, ‘WPA-PSK‘, ‘WPA2-PSK‘, ‘WPA3-PSK‘, Any or None.
- Enter the password.
- Select the additional options if required (Auto Join, Enable IPv6, Hidden Network, Hotspot or Random MAC Address).
- Select the proxy method (Auto, Manual or None).
- Click Save.
- The new Wi-Fi network configuration will appear on the list. This network can be edited or removed by selecting it using the check mark to the left of the name.
OS updates
This category defines how users can install software updates and defines enforced OS versions.
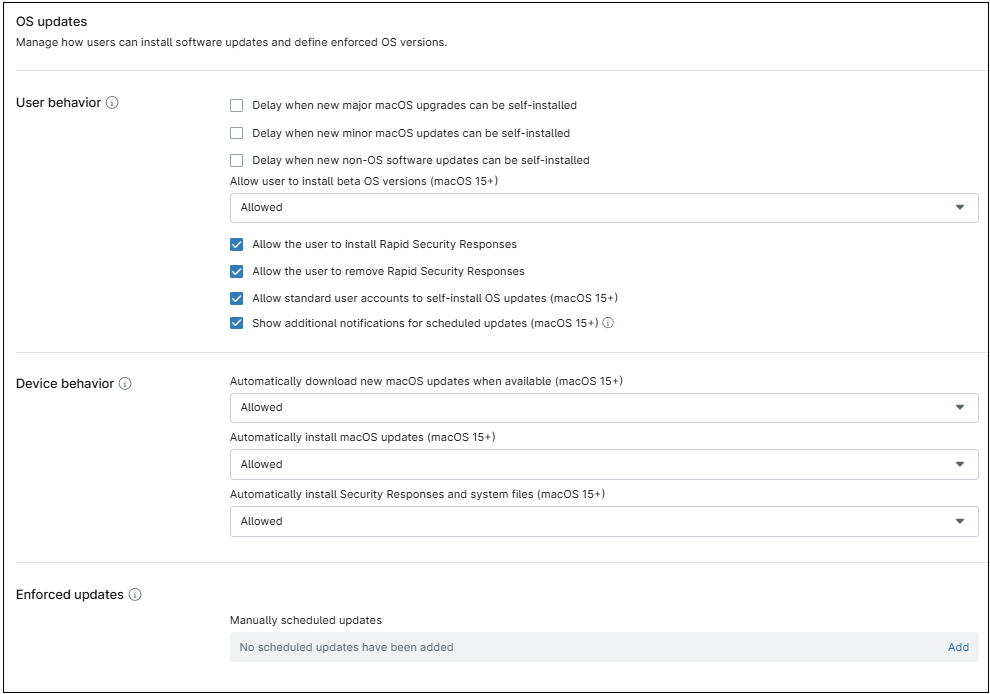
User behavior
Control when and how users can self-install macOS updates on their own devices. Requires a supervised device.
- Delay when new major macOS upgrades can be self-installed. Period to defer the availability of major macOS updates.
- Delay when new minor macOS updates can be self-installed. Period to defer the availability of minor macOS updates.
- Delay when new non-OS software updates can be self-installed.
- Allow user to install beta OS versions (macOS 15+). This option controls the installation of beta OS versions. The available settings are: Allowed, Always On, and Always Off.
- Allow the user to install Rapid Security Responses. If enabled, critical security updates released by Apple will be installed. RSRs are released more quickly than traditional OS updates.
- Allow the user to remove Rapid Security Responses. If checked, critical security updates released by Apple can be removed.
- Allow standard user accounts to self-install OS updates (macOS 15+). If checked, users with standard user accounts can approve OS updates.
- Show additional notifications for scheduled updates (macOS 15+). If enabled, users will receive daily notifications for updates scheduled in the future. If disabled, users will only receive notifications beginning one hour before the scheduled deadline.
Device behavior
Controls device behavior defined under Settings > Software Update > Automatic Updates. Settings that are enabled or disabled cannot be overridden by the user.
- Automatically download new macOS updates when available (macOS 15+). Options are: Allowed, Always on and Always off.
- Automatically install macOS updates (macOS 15+). Options are: Allowed, Always on and Always off.
- Automatically install Security Responses and system files (macOS 15+). Options are: Allowed, Always on and Always off.
Enforced updates
Control when and how updates are enforced on devices. When a deadline is reached, device may be forced to restart.
- Manually scheduled updates. Here, specific updates can be manually entered, they can be approved, rejected or enforced.
If they are approved, devices will be periodically notified to update until the deadline is reached, at which point, they will be enforced.
If they are rejected, the updates will not be enforced.
If they are enforced, devices will be forced to update to the highest specified version once the deadline has passed.
Privacy preferences
This category allows IT admins to pre-approve or deny access for managed apps to system resources without user interaction, enabling a smoother and more secure end-user experience.
Follow the steps below to add an app preference.
- In the policy editor, under the MDM section, click Privacy preferences, on the left side panel.
- Click + Add preference. The Define app privacy preferences dialog box appears.
- Under the General tab, fill out the App privacy name, which is a name to identify this preference.
- Select the Identifier type – Bundle ID or path, this is how the managed app will be identified.
- Type the app identifier for which this preference will apply (Bundle ID or path).
- Type the Code requirement.
- Select whether to Statically validate the code requirement.
- Go to the Preferences tab (on the left side).
- Click +Add. The New preference dialog box appears.
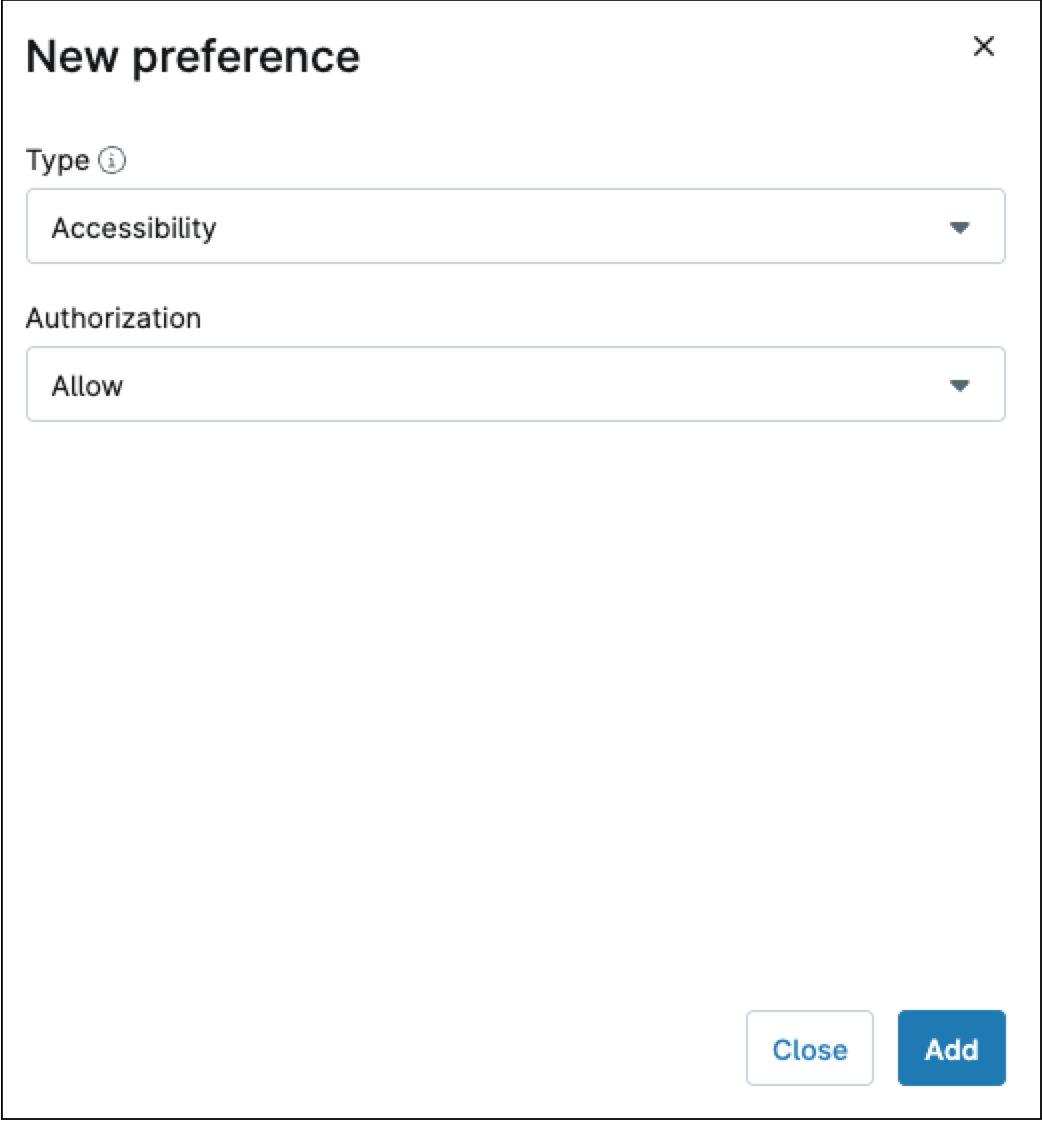
- From the drop-down, select the preference type (The type of permission that you will enforce).
- From the drop-down, select the Authorization (Allow or Deny).
- Click Add. You can add multiple preferences.
- After adding all required preferences, click Submit.
System extensions
With NinjaOne’s MDM solution, you can automatically manage and approve system extensions for managed apps. This allows for a more seamless application installation, a better user experience, and eliminating potential user errors.
Follow the instructions below to add system extensions.
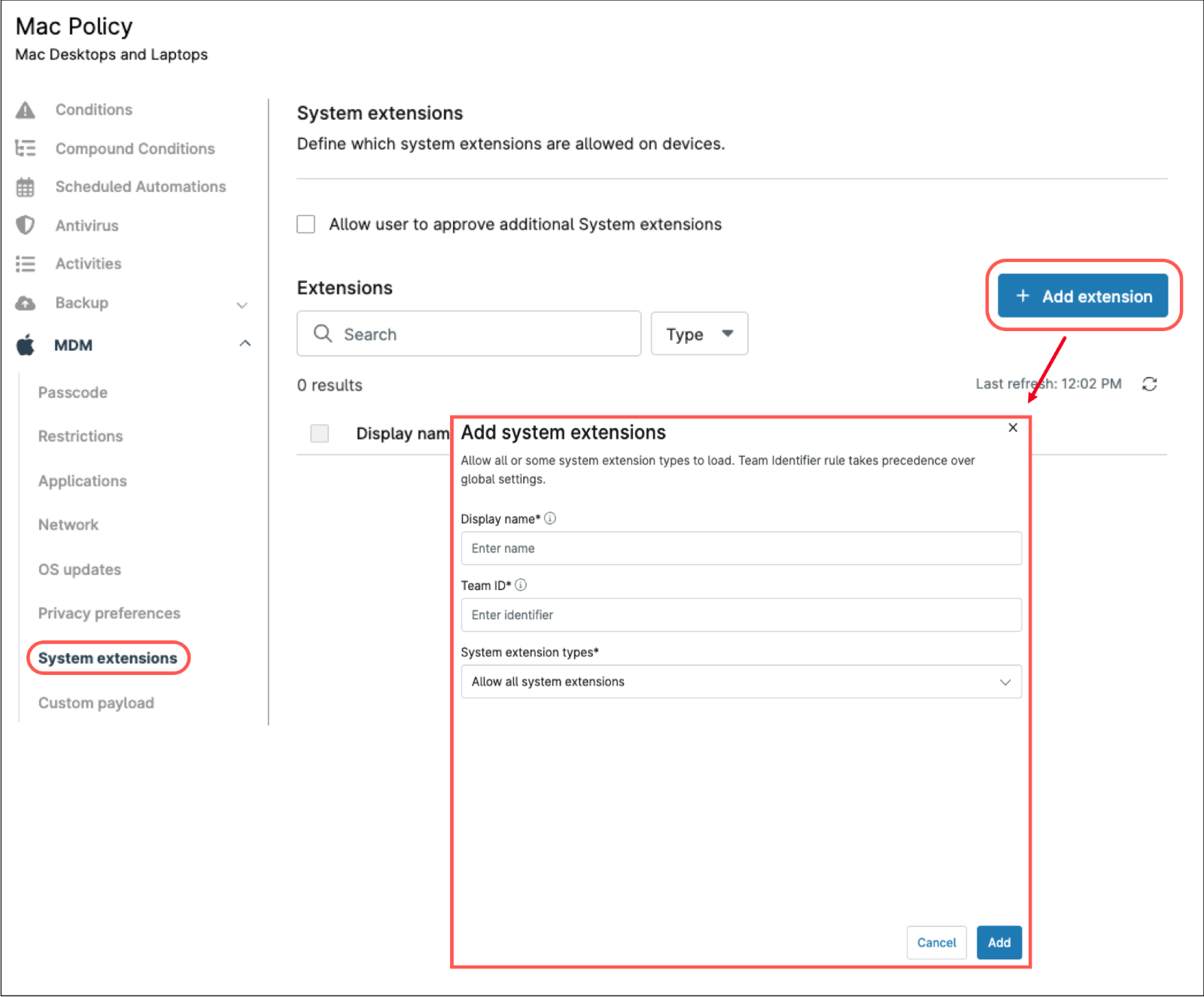
1. In the policy editor, under the MDM section, click System extensions, on the left side panel.
2. Click + Add extension. The Add system extension dialog box appears.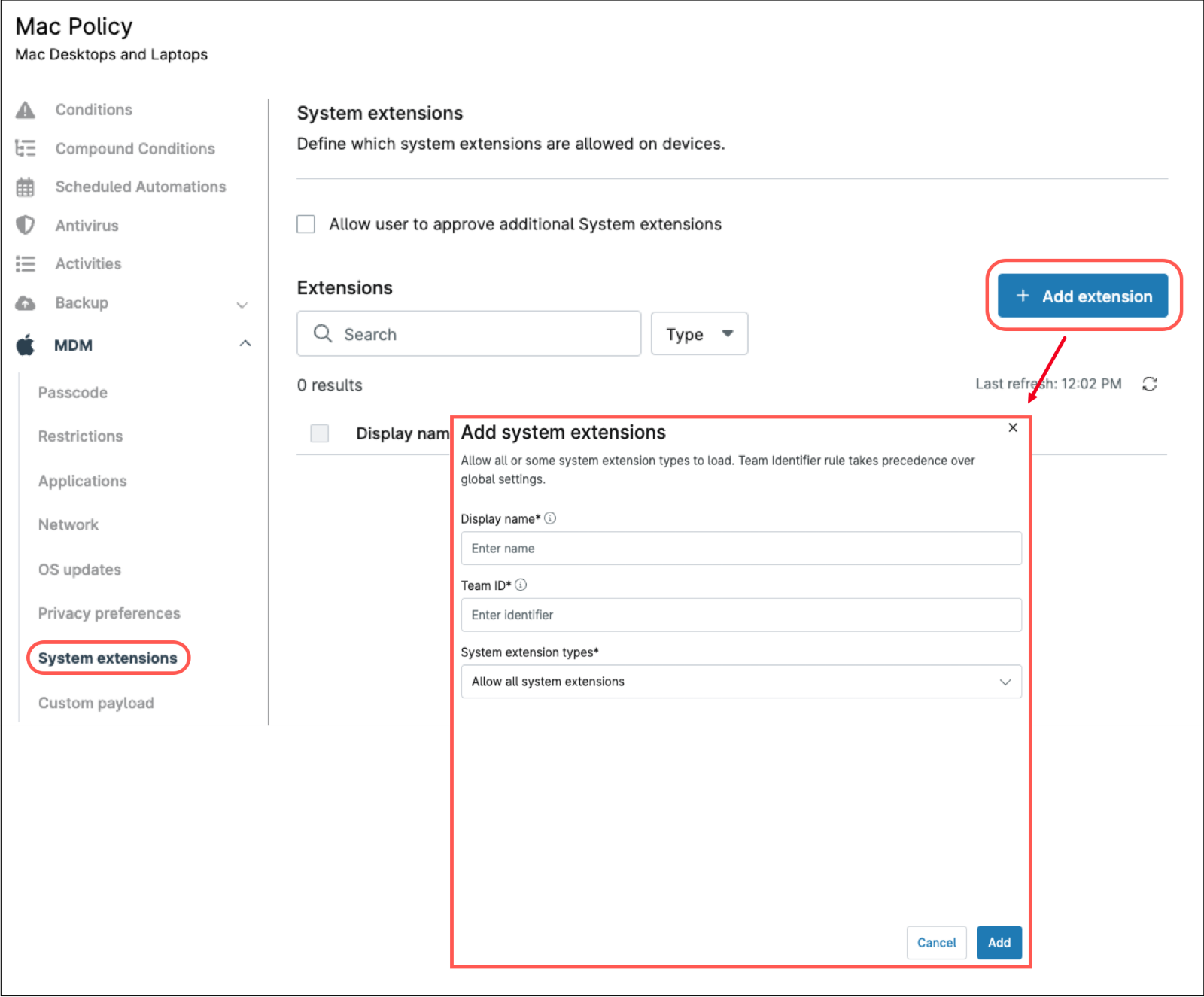
3. Fill out The Display name and Team ID.
4. From the dop-down, select the System extension types (“Allow all system extensions”, “Allow specified system extensions” or “Allow by type”).
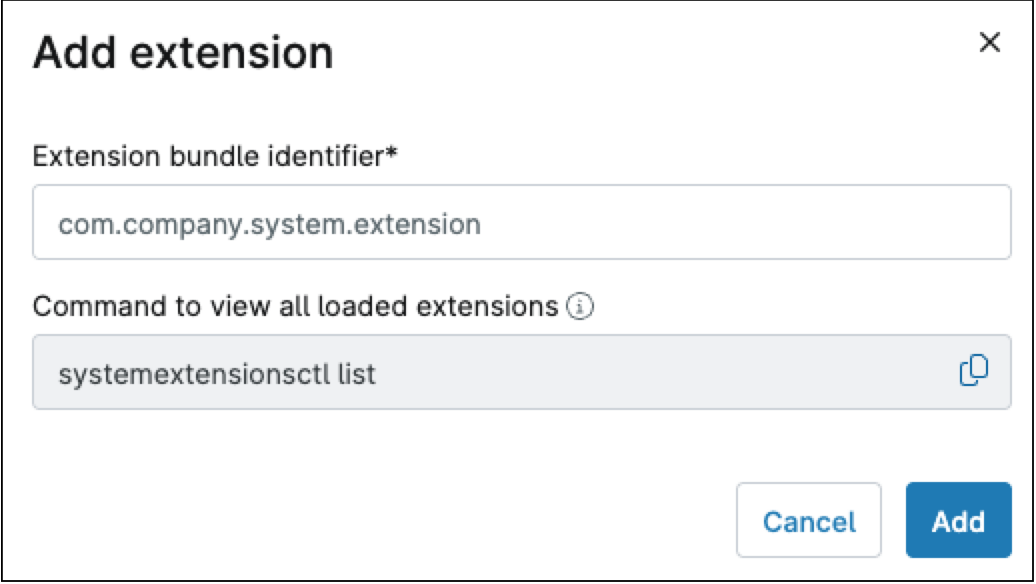
If “Allow specified system extensions” is selected, an additional dialog box will appear where you can add each desired extension by extension bundle identifier and command to view all loaded extensions (you may need to consult the app documentation).
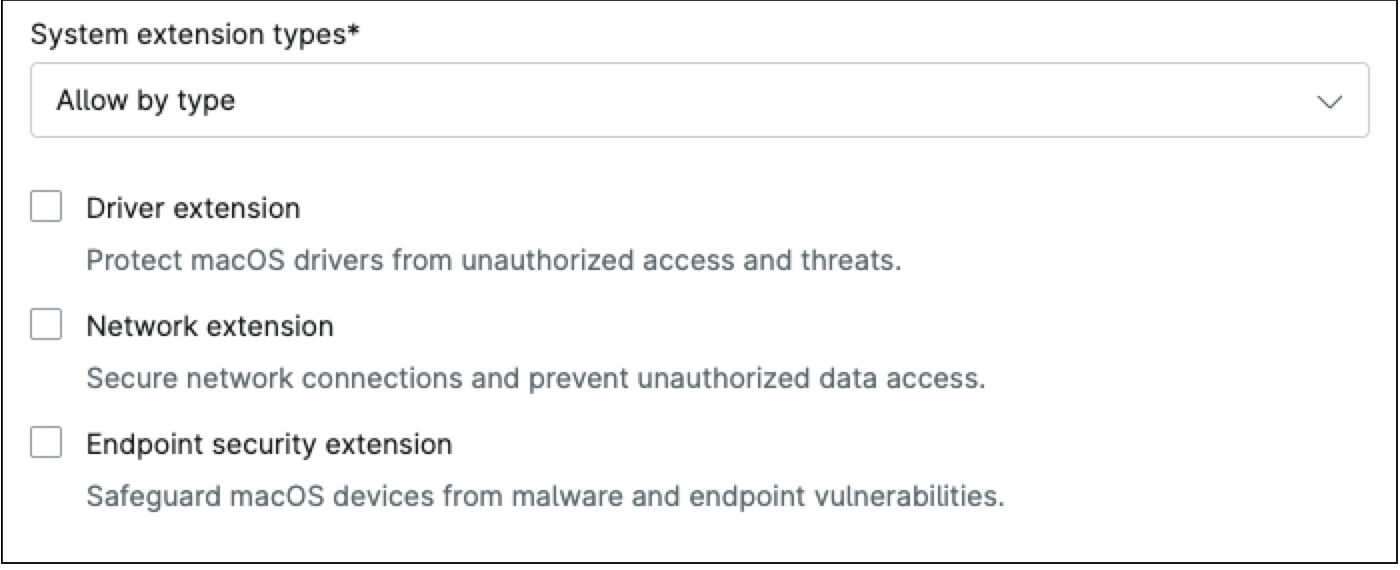
- If “Allow by type” is selected, you must select which extension type you want to allow: “Driver extension”, “Network extension” and/or “Endpoint security extension”.
5. Click Add.
Custom payload
Follow the instructions below to enter custom payloads to include in the policy.
- Click + Add payload. The Add payload dialog box appears.
- Enter a name for the payload.
- Enter the XML content, pasting is allowed.
- Click Add.