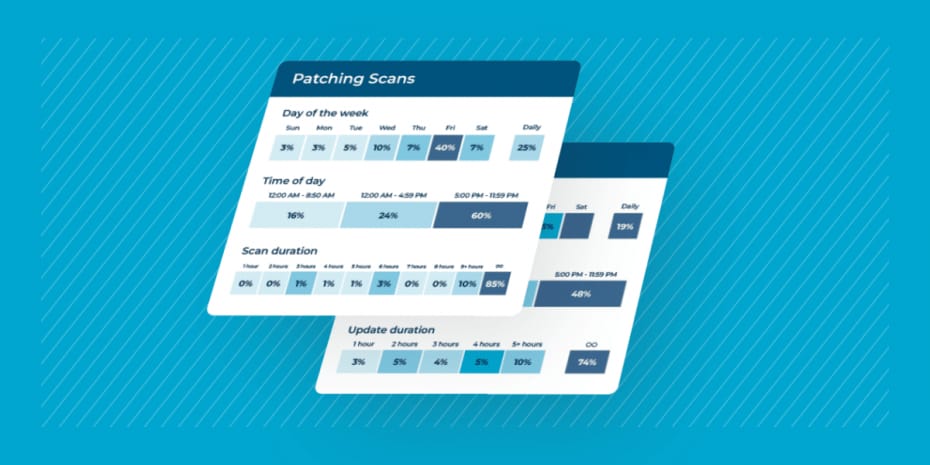
There’s no doubt that patching is tedious work. However, CNP technologies’ article on the importance of patching points out that “74% of companies say they simply can’t patch fast enough because the average time to patch is 102 days.” Understanding the patch management lifecycle is the first step that organizations take towards optimizing patching processes and creating a more secure IT environment.
Differences between vulnerability management and patch management
Vulnerability management and patch management are both similar processes, but they are not the same. TechTarget clarifies that there are plenty of core differences between patch management and vulnerability management even though the two terms are often used interchangeably.
Vulnerability management is the process of identifying, analyzing, reporting, and fixing cybersecurity threats, while patch management is the process of creating and applying patches to fix flaws or update a product or service with new features.
Why a patch management lifecycle matters
When an organization has a clear understanding of a patch management lifecycle, its IT team is able to improve each stage for optimal performance. In addition, following a step-by-step patch management lifecycle allows organizations to take advantage of the many benefits of effective patch management.
5 patch management challenges
A step-by-step patch management process can help solve pesky patch management challenges that hinder your IT department. Five common patch management challenges that affect businesses today:
1) Time
71% of IT and cybersecurity professionals believe that patching is too complex and time-consuming. To make patching a more efficient process, IT professionals aim to streamline and automate operations as much as possible.
2) IT inventory
Too often, IT teams do not have a complete IT inventory to reference for patching. That’s why it’s important to complete an IT asset inventory.
3) Unsolved risks
Since patching focuses on fixing the most troublesome vulnerabilities first and saving the others for later, the patching process often leaves vulnerabilities and other issues unsolved. This leaves systems vulnerable to attack, thus weakening security and increasing risks.
4) Patch failures
Updating software is risky, and patch failures can cause numerous problems for an organization. Heimdal Security’s patching statistics show that “72% of managers are afraid to apply security patches right away because they could ‘break stuff.’”
5) Vulnerability management
Even organizations with the best patching and vulnerability management processes run into vulnerabilities. Unfortunately, patching is a catch-up game, so as soon as an IT team patches one vulnerability, another could pop up at any time.
10 stages of the patch management lifecycle
A complete patch management lifecycle shows the entire patch management process. While this list shows all the steps separately, some organizations choose to combine certain stages together. A complete patch management lifecycle includes these 10 stages:
Stage 1: Identification
Before implementing a patch management process, an organization needs a network inventory, which identifies all IT assets on a network. To build a comprehensive network inventory, a team will need to conduct a thorough network inspection using network assessment software.
Stage 2: Prioritization
After conducting a network assessment and understanding the current IT environment, a team can then prioritize vulnerabilities and threats that were uncovered during the inspection. Categorize users and/or systems by risk and priority to create more targeted patching policies in the following steps.
Stage 3: Policies
With users and/or systems effectively categorized, an organization can now create patch management policies. Creating an effective and scalable patching policy is a simple and straightforward process that allows users to set up and manage patching requirements with ease. These patching requirements, or criteria, determine what needs to be patched when it needs to be patched, and under what conditions to patch.
Stage 4: Monitoring
In this stage, a team will be on the lookout for new patches and vulnerabilities from vendors. Usually, organizations will set up a system to receive notifications about upcoming patches and vulnerability updates from vendors instead of keeping track manually.
Stage 5: Testing
To test patches, an IT team usually uses a test environment that allows them to catch unexpected issues before the patches roll out. Before moving to the next stage in the patching lifecycle, an organization should ensure that patches roll out successfully to the test environment and that the patches operate as they are supposed to.
Stage 6: Modifications
Documentation is tedious, but it’s necessary to keep the entire IT team, and other members within an organization, on the same page. Note any changes about to be made with patches before deployment.
Stage 7: Deployment
Now, it’s time to deploy patches in accordance with the patch management policies established in stage three. This stage will determine whether patches are successful or if changes need to be made.
Stage 8: Audit
Pending or failed patches can sometimes arise after deployment. Monitor these problems closely for incompatibility or performance issues and advise end-users of the issues and upcoming solutions if necessary.
Step 9: Report
A patch compliance report allows execs and other departments to gain insight into your current IT infrastructure and how patching affects it. Ideally, a patch compliance report should be generated every month.
Step 10: Repeat
The final stage of the patch management lifecycle is to review, update, and repeat steps one through nine. This will keep information up-to-date and accurate, allowing an IT team to refine and optimize all patch management processes.
Overcome patching challenges with NinjaOne
One of the best ways to overcome patching challenges is to automate processes with NinjaOne’s patch management software. With NinjaOne’s patching solution, you can automate processes, remediate vulnerabilities, and gain insight into your entire IT portfolio from a single pane of glass. Sign up for your free trial to start optimizing every stage of your patch management process.