Every year, students and teachers manage back-to-school stress, but this year, anxieties are up a notch as the specter of a pandemic looms and schools struggle with simply meeting students’ needs. This year, many schools are taking a hybrid approach to school, combining elements of in-person and remote learning. But among the complexity of teaching remotely, one area that hasn’t been looked at closely enough is the device management practices of newly remote educators and students.
Educational institutions have historically been a target for cybercriminals, especially K-12 schools, which suffered more than 1,000 instances of ransomware since 2019. Over the summer, the FBI went as far as to issue a formal warning to schools that ransomware posed a significant threat for this school year. And in North Carolina, schools across the state saw a record number of ransomware incidents in 2020, including a recent attack that delayed the first day of school.
To better understand the degree to which educators and students are exposed to cybersecurity threats, NinjaOne surveyed 500 educators across various types of schools, including public and private K-12 schools and public and private universities. The survey was conducted on August 28, 2020, with PollFish.
Despite the heightened risks and threats schools and universities face due to remote learning, some form of remote learning will likely continue even after a vaccine is developed. Now is the time for school IT leaders and MSPs that service education clients to take stock of challenges and work hard to institutionalize changes so schools are ready for a digital world.
“As school districts, teachers, parents, and students have no doubt thought endlessly about how this school year will actually play-out, there is potentially one area that has not received enough consideration,” said NinjaOne Chief Security Officer Lewis Huynh. “The average consumer household, with arguably the weakest levels of cyber-security protection, has now collectively become the largest attack surface available to hackers. This makes it extremely critical that IT, Security, and Networking Teams work together on remote connectivity solutions that focus on a trifecta of usability, performance, and protection.”
A Mixed Approach To Device Management And Security
Devices Used Daily
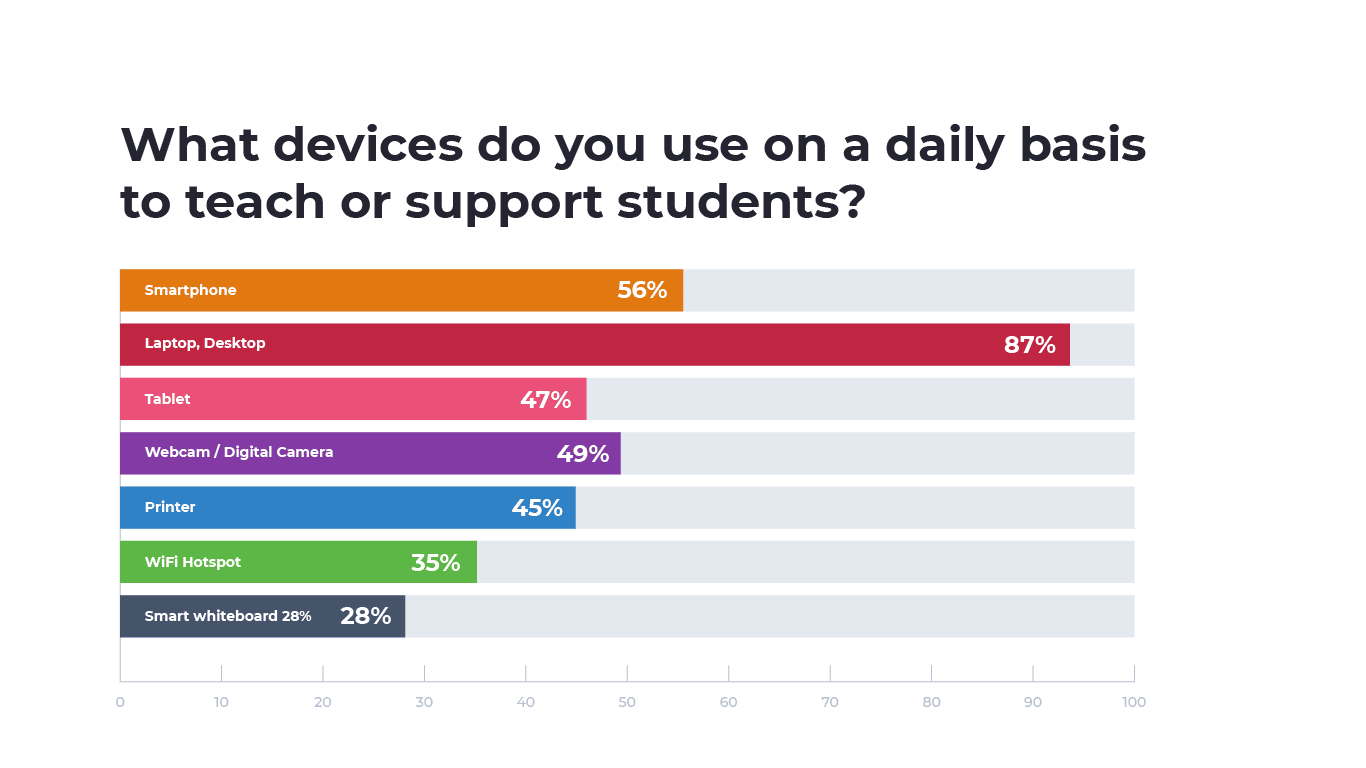
As expected in a remote learning world, mobile devices like laptops, smartphones and tablets were among the most used devices used by educators on a daily basis. 56% of educators used smartphones on a daily basis, while 47% used tablets. Perhaps unsurprisingly, 87% of educators were using a laptop or desktop. This finding mirrors recent trends in the increased use of smartphones and tablets in the classroom to enhance lessons and an abundance of apps geared towards educators.
Printers and webcams also ranked highly among remote devices used by educators. These innocuous-seeming devices contain their own risks, such as spyware to record private conversations or steal personally identifiable information from scanned and printed documents.
Security Disparities Between Educators Using Own Devices
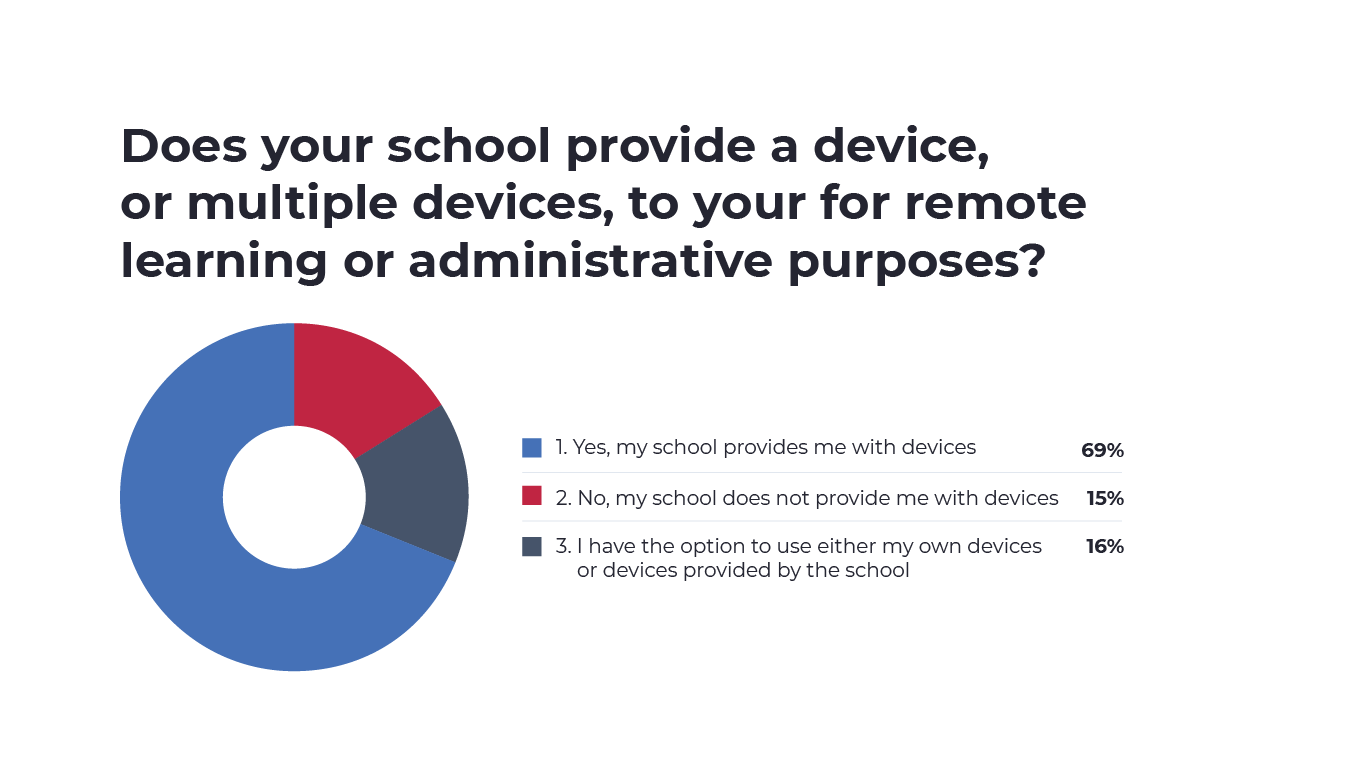
Adding more complexity to the issue, many educators use their own devices to teach. In our survey, we found that 15% of educators’ schools don’t provide them with devices while 16% are allowed to use either their own devices or those provided by the school. However, 69% of educators surveyed reported their school did provide them with devices. A BYOD approach introduces additional complexity by raising the risk of a cyberattack or breach, most commonly through phishing attempts.
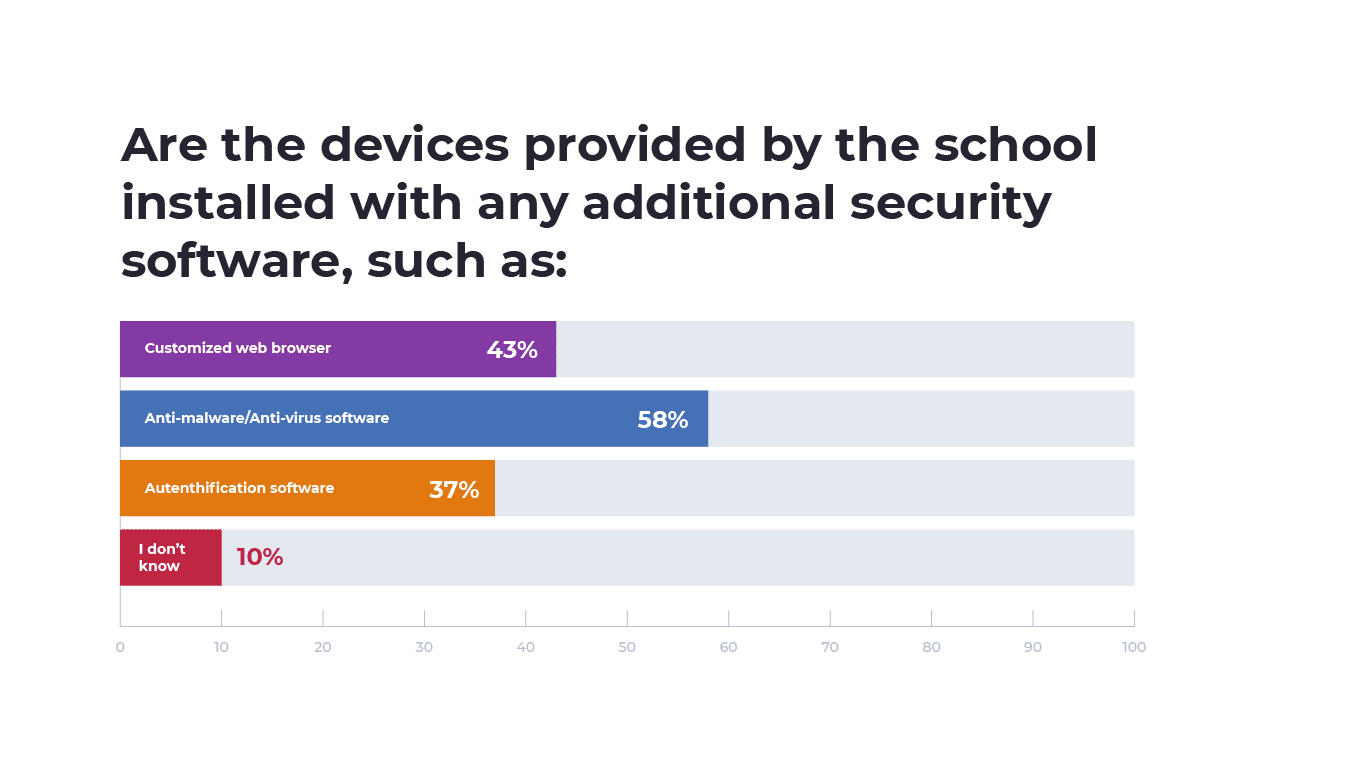
Among those using devices provided by their school, 58% indicated their devices are installed with anti-malware or anti-virus software. Additionally, 43% had a customized web browser installed on their device and 37% indicated they had authentication software installed on their devices. Only 10% didn’t know whether the devices provided by their school contained additional security software.
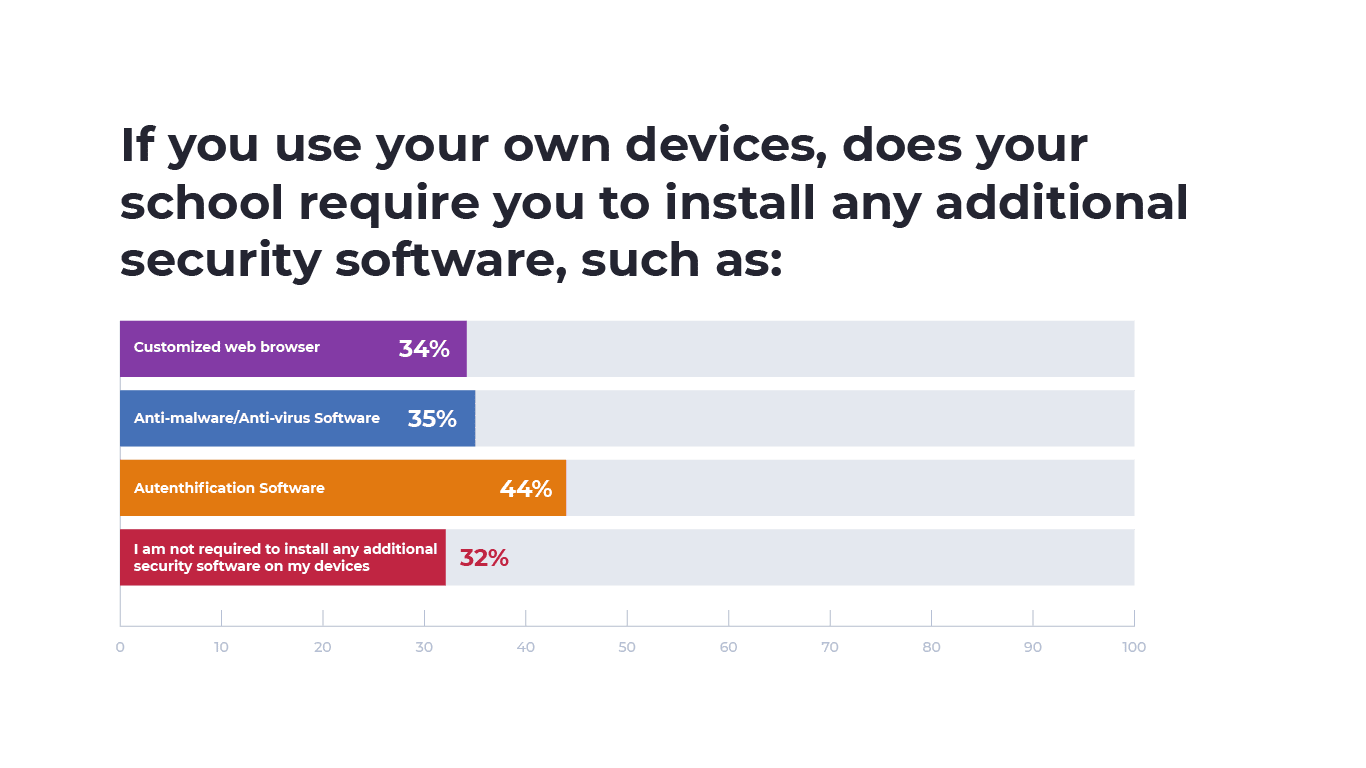
The numbers told a different story for educators using their own devices. 32% of educators that used their own devices were not required to install any additional security software. Of the 65% of respondents that were required to install additional security software, 44% installed authentication software, 34% installed a customized web browser and 35% installed anti-virus or anti-malware software.
“The lack of authentication protocols on school devices is a liability that multiplies with every additional device connected to the network,” said Coveware CEO Bill Seigel. “Re-used or weak passwords are an ‘oldie, but goodie’ for cybercriminals looking to gain access to a network, and authentication layers, like multi-factor, are the antidote. This will end badly for schools it is just a question of who gets hit, and when.”
Most Network Connections Meeting Industry Standards
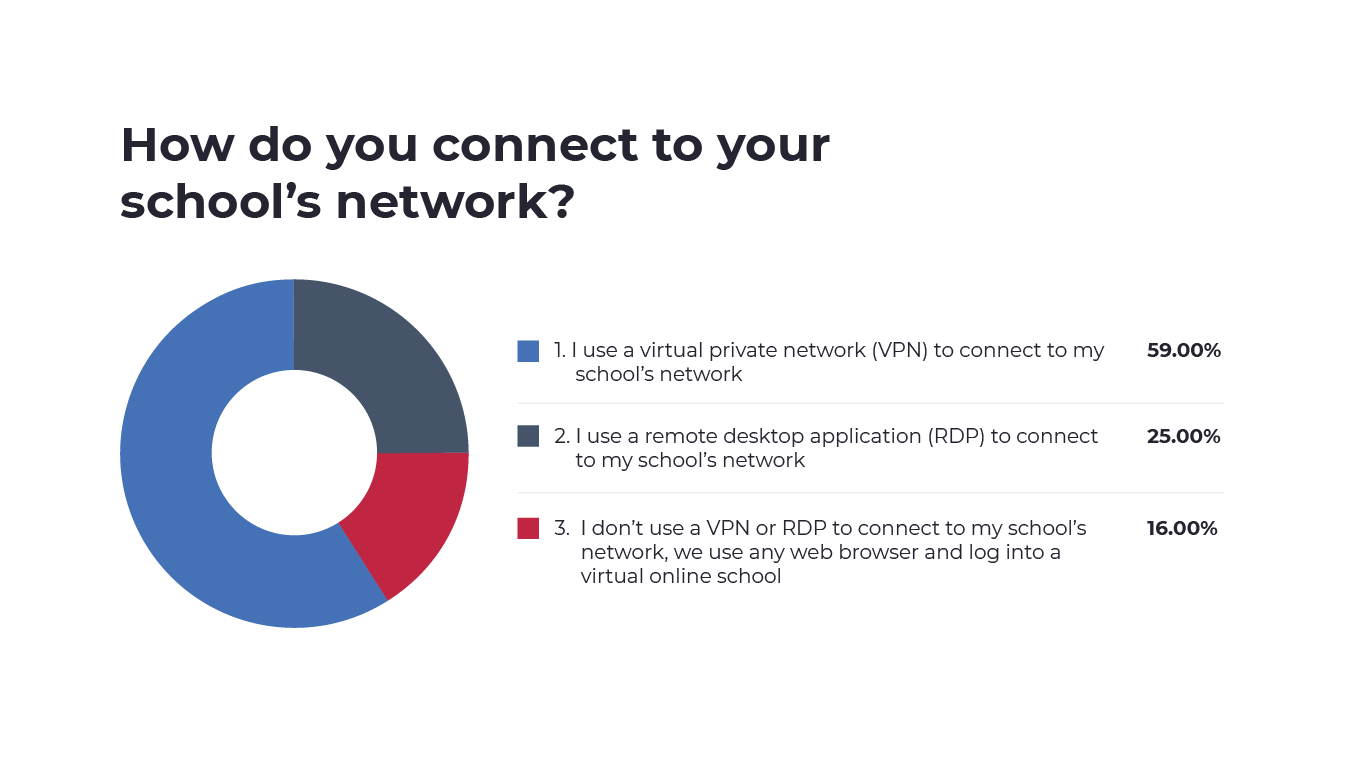
When asked how they connect to their school’s network, 59% of educators reported using a VPN. 25% of respondents used an RDP connection and 16% used neither a VPN or RDP but rather signed into a virtual school through any browser.
For educators that may be accessing private student data, it is concerning that some aren’t using a secure connection. This poses a significant security gap that should be at the top of any list of security priorities. Ultimately, the security of connections via VPN or RDP are dependent on the vendors offering the service. For this reason, IT leaders should perform a careful analysis of the security standards of every vendor they partner with.
Cybersecurity Training Represents Opportunity For Improvement
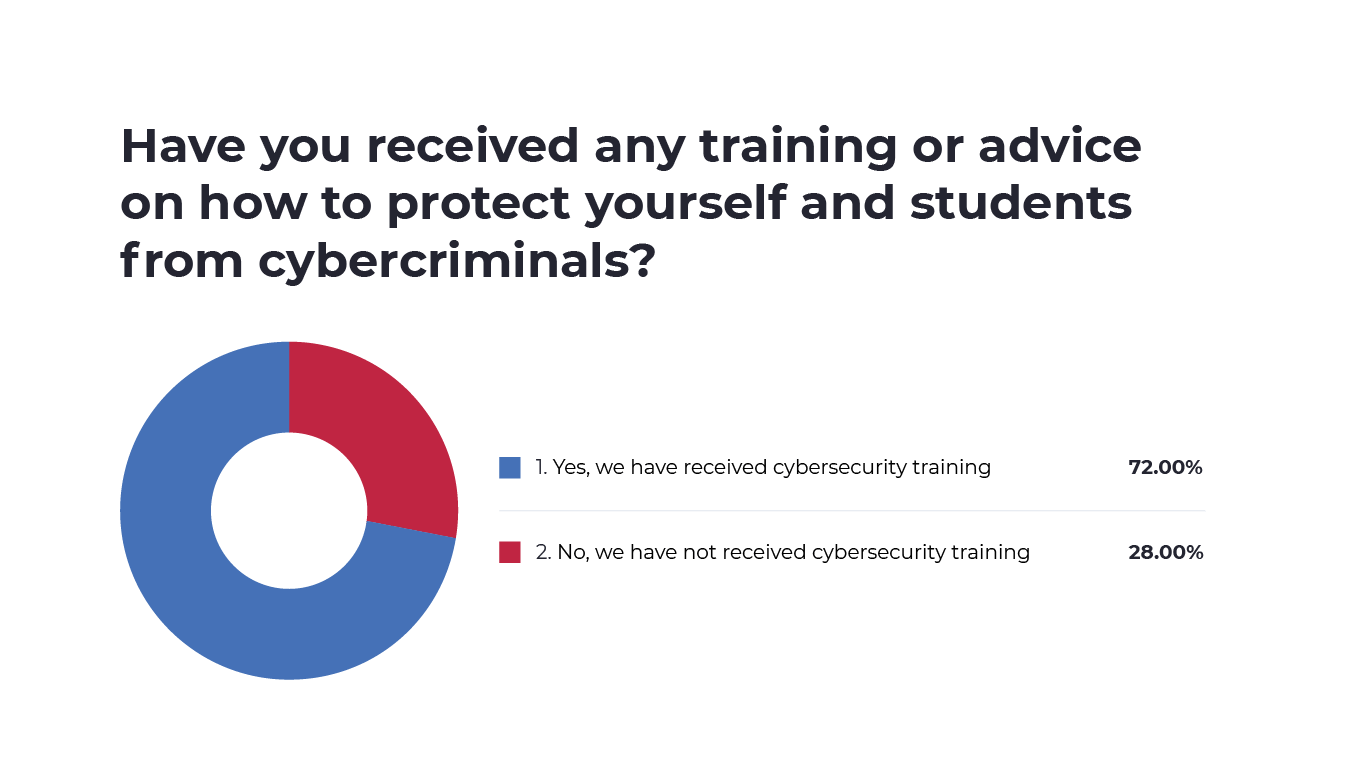
Almost three-quarters of educators surveyed reported having undergone some kind of cybersecurity training. However, 28% had not received cybersecurity training. Routine cybersecurity training is a highly recommended practice that allows leaders to communicate priorities, answer questions and proactively mitigate threats like phishing.
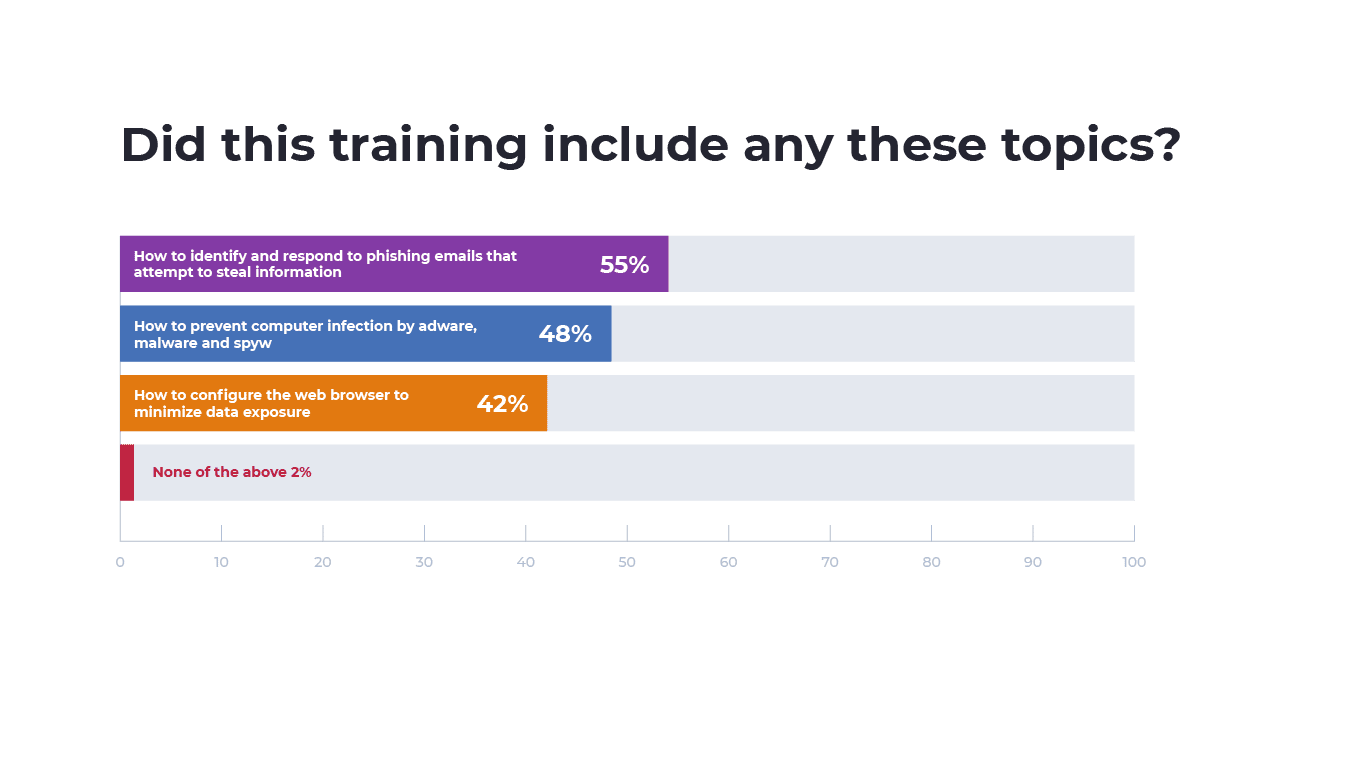
Among those that did receive cybersecurity training, 55% were taught how to identify and respond to suspected phishing attempts, 48% were taught how to prevent computer infection by adware, malware and spyware, and 41% were taught how to configure their web browser to minimize data exposure. Only 2% of respondents did not receive training in any of the scenarios.
Based on these findings, security lapses among educators using their own devices could expose schools to new threats and raise the likelihood of data theft. School IT leaders and MSPs working with clients in this sector should focus on ensuring all educators are equipped with a unified security policy that covers foundational elements such as anti-virus and multi-factor authentication to access devices and applications used by educators.
Student Device Management Practices Similar To Educators
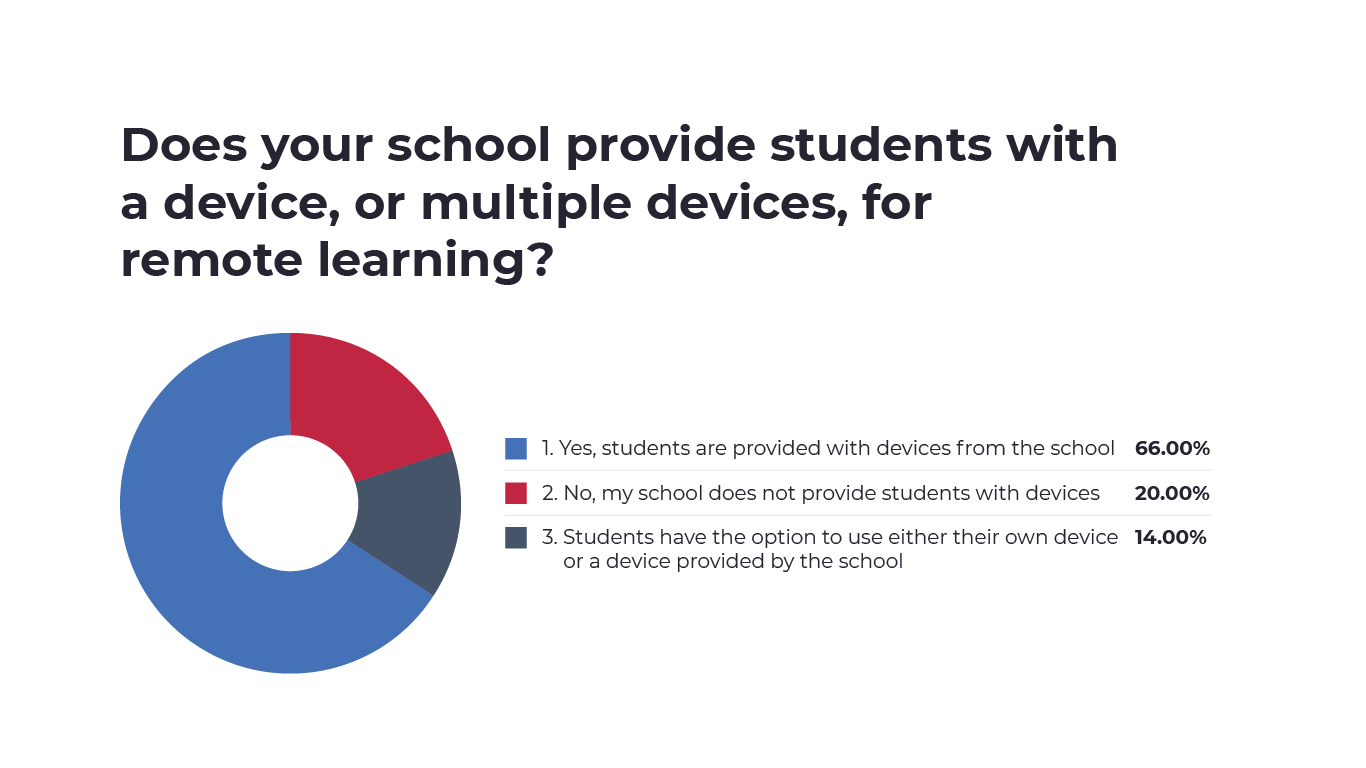
Looking at how schools manage devices among students, we found that 66% of students were supplied with devices by the school, but 20% of students were not provided with devices and 14% had the option to use either their own devices or devices provided by the school.
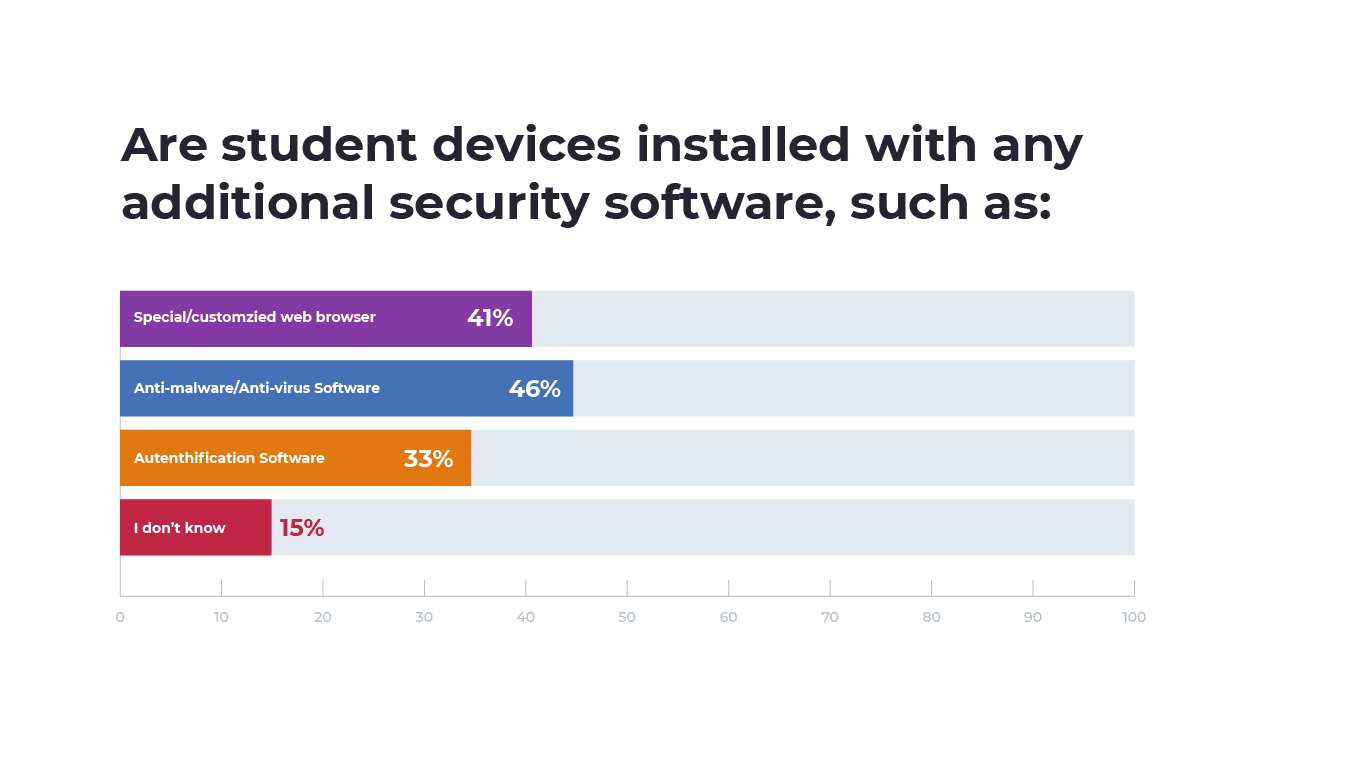
For students that were supplied with devices, 46% of respondents indicated student devices were installed with anti-malware or antivirus software, 41% of school supplied devices were installed with a customized browser to limit data leakage and 35% of school supplied devices were installed with authentication software.
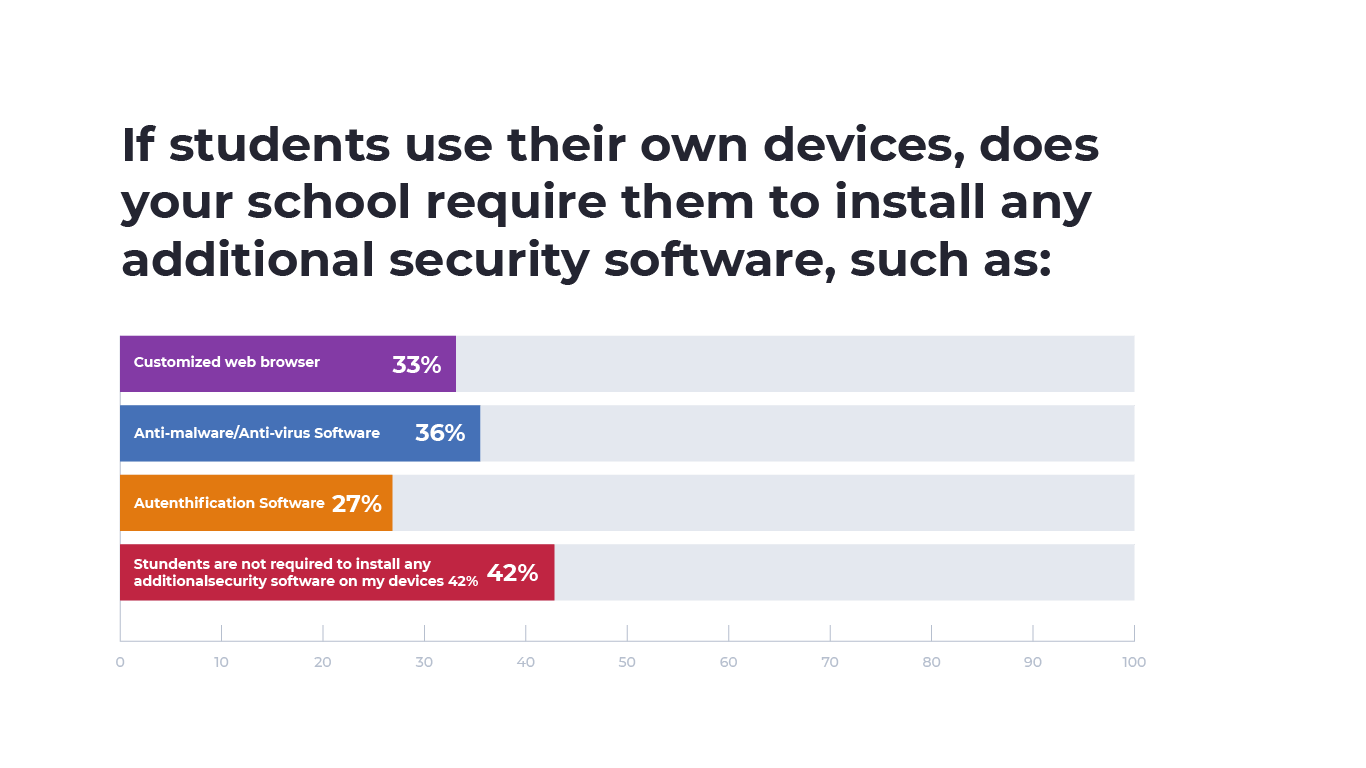
However, for students using their own devices, 42% of respondents indicated that students weren’t required to install any additional security software. Among students that were required to install additional security software on their devices, 36% of respondents indicated students’ personal devices had to be installed with anti-malware or antivirus software, 33% had to install a custom web browser and 27% had to install authentication software.
Overall, student device management and security echoed that of educators. When devices were provided by the school, educators and students were more likely to have basic security software installed on their devices. But for both groups, those that used their own devices had much lower rates of additional security software installed on their devices and many weren’t required to install any additional security software whatsoever. With nearly a third of students potentially using their own devices to connect to their school’s network, school IT leaders must make remote endpoint security a priority to protect school networks and student data.
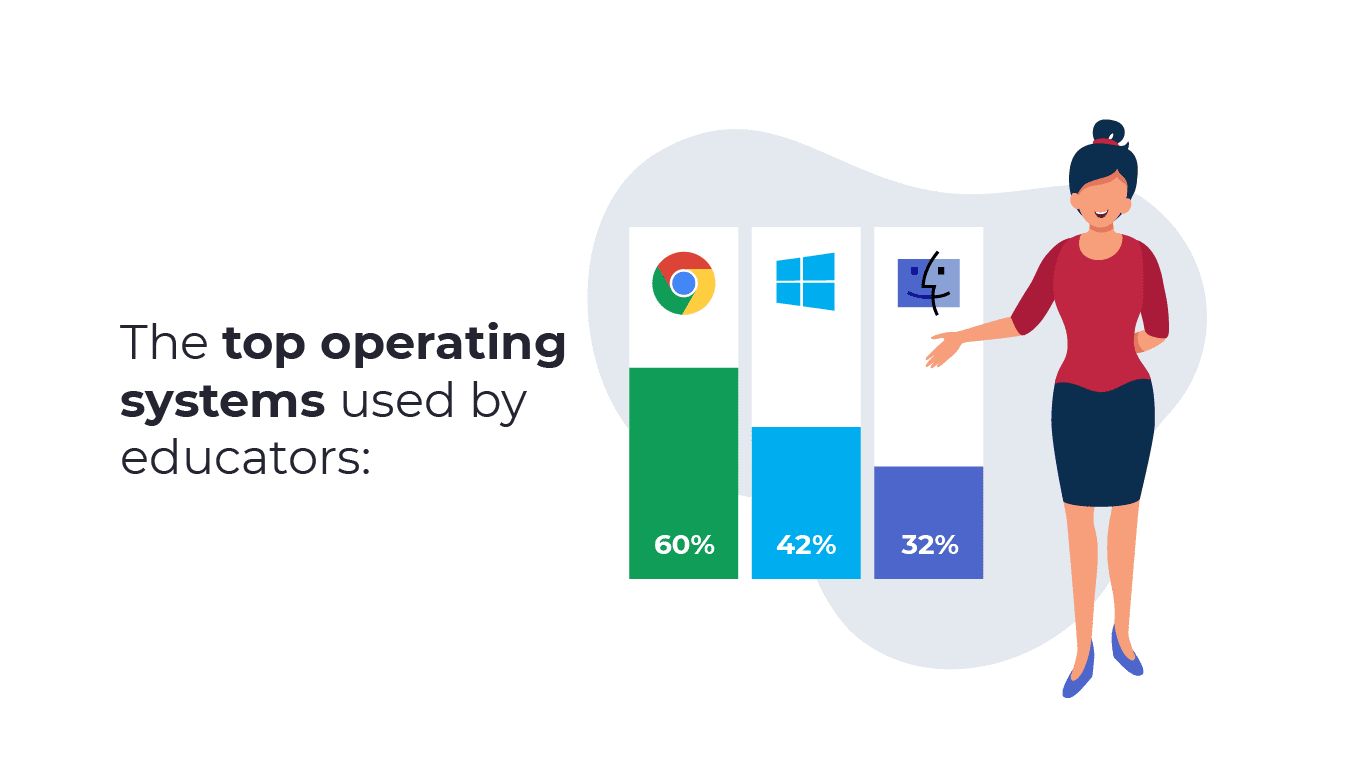
ChromeOS Tops List of Most Used Operating System On School Devices
Among respondents using devices provided by their school, 60% reported their devices use the ChromeOS operating system. 42% of respondents indicated their school supplied devices used the Microsoft Windows operating system and 32% of school devices used Apple’s iOS or MacOS operating system.
Google’s ChromeOS has surged in popularity among schools thanks to its high security standards and user friendly design. For school IT leaders, moving all students and educators to more secure devices should be a goal, but additional steps to properly monitor, manage and secure remote devices must not be forgotten.
Conclusion
Based on these results, many schools appear to lack a consistent device policy that would protect educators, students and school networks. In the first weeks of the school year, we’ve already seen how insecure school networks can be as multiple school districts around the country were forced to delay their school year due to cyberattacks. Ransomware, in particular, poses one of the most significant threats to schools and is a heightened risk school IT leaders must protect themselves against in an era of remote learning.
With schools facing uncertain budgets this year due to the coronavirus and deadlock in Congress, one area that school IT leaders and MSPs that service the education sector can make the most difference with the least amount of resources is educating students and staff on basic cybersecurity training and hygiene.
Now more than ever, the benefits of having a remote endpoint monitoring and management platform installed across every device are salient. From the increased agility and intelligence derived from a remote monitoring and management platform, school IT leaders can be more strategic in their actions while reducing costs and increasing the security and performance of remote end users.
Read more of NinjaOne’s original research and insights on our blog. There, readers can access free tools and resources to help you build a better MSP.
Read More: What Should You Be Monitoring with Your RMM? 28 Recommendations
Read More: The 2020 Guide to Managed Services Agreements for Managed IT Services Providers