Without a doubt, a data recovery solution is essential when it comes to maintaining security and business continuity. Backups give you important survival options when ransomware hits, a laptop is lost, or someone accidentally deletes a folder full of important files. Without those safe, secure, redundant copies of your most important data, you’d be left out in the cold.
In this article, we’re going to talk about endpoint backups — what they are, how they work, and why everyone should be using them.
What is endpoint backup?
The safety and security of endpoints is extremely important to businesses because they both serve as necessary workplace tools — think laptops, workstations, and tablets — and they can create vulnerabilities if they’re not properly managed.
What is an endpoint?
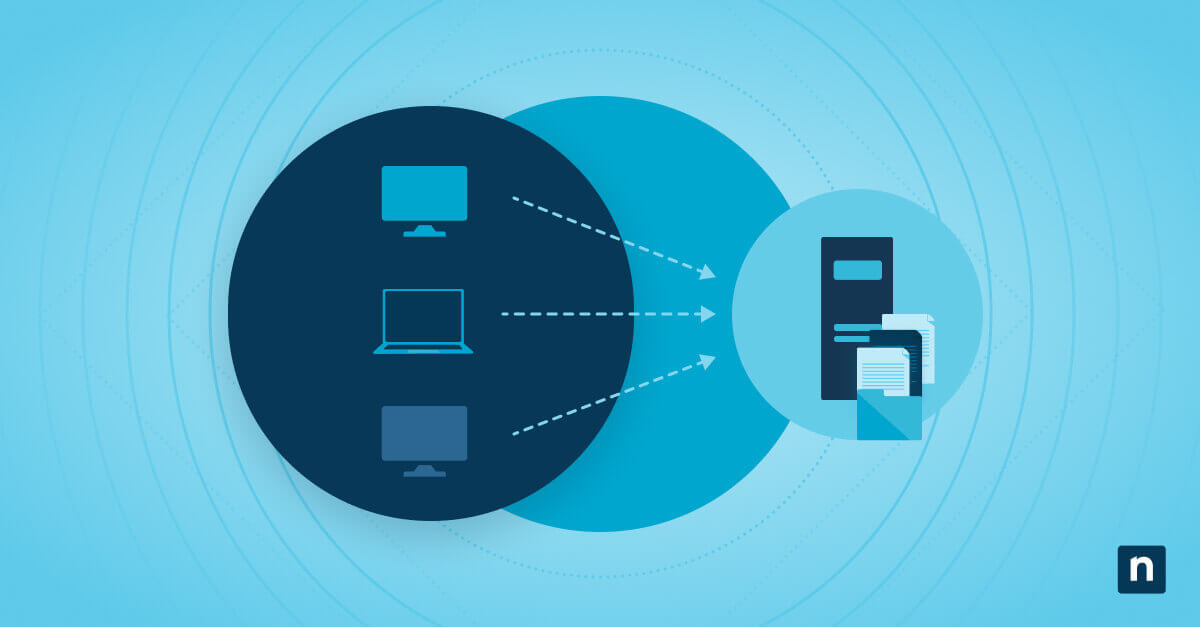
An endpoint is any device used for producing, sharing, accessing, and saving information and connected to a network. It can be a laptop, desktop, tablet, mobile phone, point-of-sale (POS) device, manufacturing machine, IoT device, etc. These are input devices at the end of any network.
One part of effective endpoint management is maintaining remote, secure backups of the files and other mission-critical data on those devices. Endpoint backup tools make this possible by sending copies of data to remote, secure file storage where it can be later recalled in the event of a disaster or deletion.
Such endpoint backup solutions usually run on a schedule; it might be every 24 hours, or it may provide continuous backup. The various timings are configured by the end users to suit their needs. They may run full backups or incremental backups depending on how much storage the end user wishes to allocate to backups and recovery.
Endpoint backup solutions have become very popular among SMBs and enterprises alike thanks to shrinking costs and easy deployment. Cloud-based backup solutions have certainly paved the way for more accessible and affordable endpoint backup solutions.
What endpoint backup protects
Endpoint backup solutions protect against a variety of potential data loss scenarios, including:
- Hardware failure: If a device’s hardware fails, an endpoint backup can be used to restore the data and configurations to a new device.
- Ransomware attacks: Endpoint backups can be used to restore data that has been encrypted by ransomware.
- Natural disasters: Backups can be stored in a remote location, ensuring that data can be restored in the event of a natural disaster that affects the primary location.
- Human error: Backups can be used to restore data that has been accidentally deleted or overwritten by an employee.
- Lost or stolen devices: Backups can be used to restore data to a new device in the event that a device is lost or stolen.
- Cyber Attacks: Endpoint backups can be used to restore data that has been deleted or encrypted by a cyber-attack.
- Software updates and upgrades: Backups can be used to restore data and configurations that have been lost during software updates and upgrades.
- Power Outages or System crashes: Backups can be used to restore data and configurations that have been lost due to power outages or system crashes.
Endpoint backup vs. cloud syncing
Some might be asking why endpoint data backup is important when it sounds so much like the automated syncing that happens when using a cloud-based service. A good question, and the answer requires that you know the differences between file syncing and true backup.
Cloud-syncing services (otherwise known as cloud backup services) like OneDrive, Dropbox, or Google Drive can’t protect data from the wide range of potential threats that true backup solutions address. Data corruption, ransomware, and other types of malware will simply “sync” right from the infected device to the remote storage location. Even if a user accidentally deletes a file, it will usually sync that deletion right into the cloud and remove all copies of the file. While some cloud services offer ways to recover accidental deletions, they typically only archive such files for a few days and cannot replace a dedicated Endpoint cloud backup solution.
Endpoint backup solutions — indeed all forms of backup and recovery solutions — are purposefully built for the sole mission of keeping your files protected. They are not productivity tools per se, so they don’t make compromises when it comes to the safety and security of your data.
Endpoint vs. datacenter backup
You’ve no doubt heard of data backup in some form or another. If nothing else, the idea might conjure memories of external hard drives or even tape drives used to make backup copies. You might have also heard of data center backup solutions, or just cloud backup solutions.
So where does endpoint backup fit in among all of this, specifically? That depends.
Many data center backup solutions offer endpoint security coverage, but not all do. Likewise, some endpoint backup software can also provide comprehensive data center backup coverage. The overlap is not guaranteed with every solution on the market.
But if there is overlap, you might be wondering what the difference is in the first place.
Data center backup refers to solutions that are used as part of an organization’s disaster recovery and business continuity efforts. These are large-scale backup solutions that you might associate with making backups of a company’s entire operational database.
Endpoint backup refers specifically to the safe storage of backup copies made from “endpoints” like laptops, desktops, phones, and tablets. If data center backup is protecting the company’s brain, endpoint backup is protecting all of the other organs and limbs that make it a functioning organism.
Knowing that, you know that the biggest difference between endpoint and data center backup is that endpoint data is mobile. Endpoints are used and often physically transported by the organization’s end users.
This leads to an important consideration. Because endpoint protection and endpoint backup solutions work directly with the end users’ technology tools, it’s important that these measures don’t interfere with productivity or add too many variables to the security equation. For any solution to work, it must be used, configured, and fully integrated into the workflow — nothing is worse than losing data because an employee disabled their security software as a matter of convenience.
How does endpoint backup work?
Endpoint backup solutions can range greatly in functionality but will generally pull data from a local hard drive or device and send secured, most likely encrypted, copies of that data to a remote storage location. What data is copied and how often is configured through the software itself.
The most effective endpoint backup plan would involve protecting every file on every device. In most cases this is possible without too much demand on resources, although large files (think media production) could put a strain on network stability if backed up frequently and in full.
Most backup tools give users a centralized dashboard that shows them the statuses of device backups and allows them to restore a single file or an entire system including applications, configurations, preferences and personalization from one interface.
The integrity of backups is a key factor that shouldn’t be overlooked. Advanced endpoint protection tools will conduct automatic backup checks to ensure backups are verified for a reliable recovery, validating every backup and providing a notification to IT if there are any issues.
Features of endpoint backup solutions
There are many options out there when it comes to endpoint backup solutions. Your ideal fit will depend on a few factors, including budget, resource needs, and how much freedom you need in configuration. With that in mind, there are some important features to look for before choosing your organization’s next endpoint backup tool:
Self-service
Many users consider self-service an important part of a backup solution. Because the modern workforce operates from different locations, in multiple time zones, and with a variety of devices it can be difficult to offer responsive IT support around the clock. Even if the effort is made, larger organizations can remove a great deal of strain from their IT teams by incorporating self-service whenever possible. If end users are able to search files, restore backups, and get back to work without further intervention, everyone wins.
Flexibility
Everyone loves flexible technology. Effective protection often hinges on how well the software can be adapted to your unique needs, integrations, and technical specs.
Automation
Process automation is essential to productivity and operational maturity. The more automation can be fit into a solution, the more effective your IT environment will ultimately be — as long as that automation is used correctly and leveraged to its fullest.
Resource Optimization
Backups take storage space and bandwidth, regardless of what tool you use. Take notice of the options that offer bandwidth throttling, deduplication, network acceleration, compression, and other ways of minimizing bandwidth usage and storage.
Endpoint backup and recovery solutions
There are many different endpoint backup and recovery solutions available, each with its own set of features and capabilities. Some solutions focus on file-level backups, allowing organizations to protect specific files and folders. Other solutions offer image-level backups, creating a complete copy of the device’s hard drive, including the operating system and all installed programs. Additionally, many solutions offer cloud-based storage options, as well as the ability to recover data to a new device in the event of a lost or stolen device.
Here are 8 examples of popular endpoint backup and recovery solutions:
- NinjaOne: A Cloud-based endpoint backup and disaster recovery solution that allows businesses to backup and protect their endpoints, servers, and applications.
- Carbonite: Offers cloud-based endpoint backup, recovery, and archiving solutions for both businesses and individuals.
- Veeam: Provides image-level backups, as well as the ability to restore data and entire systems to a previous point in time.
- CrashPlan: Offers both file-level and image-level backups and can store backups in the cloud or on a local server.
- Symantec Endpoint Protection: Provides image-level backups, as well as antivirus and firewall protection.
- Datto: Offers endpoint backup, disaster recovery, and business continuity solutions for SMBs.
- Asigra: Provides cloud-based endpoint backup and recovery solutions for businesses of all sizes.
- Acronis Backup: Provides file-level and image-level backups, as well as the ability to recover data to a new device in the event of a lost or stolen device.
When choosing an endpoint backup and recovery solution, it’s important to consider the specific needs of your organization, such as the types of devices being used, the amount of data to be protected, and the recovery options that are required.
By choosing a solution that meets your organization’s specific needs, you can ensure that your data is protected and that your systems can be quickly restored in the event of a disaster. NinjaOne endpoint backup enables users to recover data and entire systems to a previous point in time and has a feature of File and Folder level backup.
Do I need endpoint backup?
In a word, yes. This confident, earnest answer comes from the fact that endpoints have become a key point of concern for all matters of cybersecurity.
In a recent State of Endpoint Security Risk report by Ponemon, 68% of IT/security professionals said that the frequency of attacks against endpoints had increased over the past 12 months. In addition, 51% of respondents considered endpoint attacks to be successful because their endpoint security solutions don’t accurately detect threats. In many cases, damage from the successful attacks against these endpoints could have been mitigated with endpoint backups, even though the endpoint security solution itself didn’t catch the threat.
And these mishaps can occur because the nature of endpoint security itself has changed so much in the face of changing threats.
Endpoint protection once meant using signature-based antivirus at each endpoint — a simple solution that nearly everyone could do themselves. Unfortunately, today’s threat actors have developed numerous means for bypassing these traditional AV solutions, driving the need for more advanced endpoint security solutions.
Protecting your organization’s endpoints has itself become a layered affair. Along with endpoint backups, you should put other defensive measures into place, such as:
- A means of application whitelisting
- Multi-factor authentication wherever possible
- Network access control
- Patch management software to ensure all assets are updated quickly
- Advanced anti-malware software
Even with all of these solutions in place, endpoint management is not complete without an endpoint backup solution. Rest assured that an effective and easy-to-use backup and recovery solution will ensure business operations can be resumed with minimal disruption should the worst happen.
The importance of a data protection strategy
Data protection is an essential aspect of any organization’s overall security strategy. With the increasing amount of sensitive information being stored on individual devices, it’s important to have a robust data protection strategy in place to ensure that this information is secure and can be quickly restored in the event of a disaster.
One key component of a data protection strategy is having an effective backup strategy. By regularly backing up data on individual devices, organizations can minimize the risks associated with data loss and quickly restore their systems and data in the event of an incident. This is especially important as more and more employees are working remotely and accessing sensitive company information on their personal devices.
However, endpoint backup and recovery is only one aspect of a comprehensive data protection strategy. Other important components include data encryption, disaster recovery planning, and regular security assessments. By implementing a combination of these measures, organizations can better protect their sensitive information and ensure that they are prepared to respond to a variety of potential data loss scenarios.
Conclusion
How we work has changed forever, and it has become routine for organizations to have employees and collaborators all over the world. “Bring your own device” (BYOD) policies provide flexibility, but they are also a compounding security challenge in the rise of remote workforces.
As such, endpoints are now one of the weakest parts of an organization’s network with over 70% of breaches originating from endpoints. That’s why endpoint backup is a key component of any security stack, and choosing the best endpoint backup provider can make all the difference.
NinjaOne is a best-in-class endpoint backup and disaster recovery provider that allows businesses to back up and protect their endpoints, servers, and applications. Learn more about how NinjaOne can help make the difference when it comes to your data protection needs.