The rapid evolution of technology has given rise to sophisticated cyber threats that can exploit vulnerabilities in web applications. Cybercriminals continually devise new methods to compromise data integrity, confidentiality, and availability. To counter these threats, organizations must adopt advanced security measures that go beyond traditional security protocols.
This article explores Web Application Firewalls (WAFs), what they are, how they work, their benefits, and the crucial role they play in fortifying web applications and networks against cyber threats.
What is a WAF?
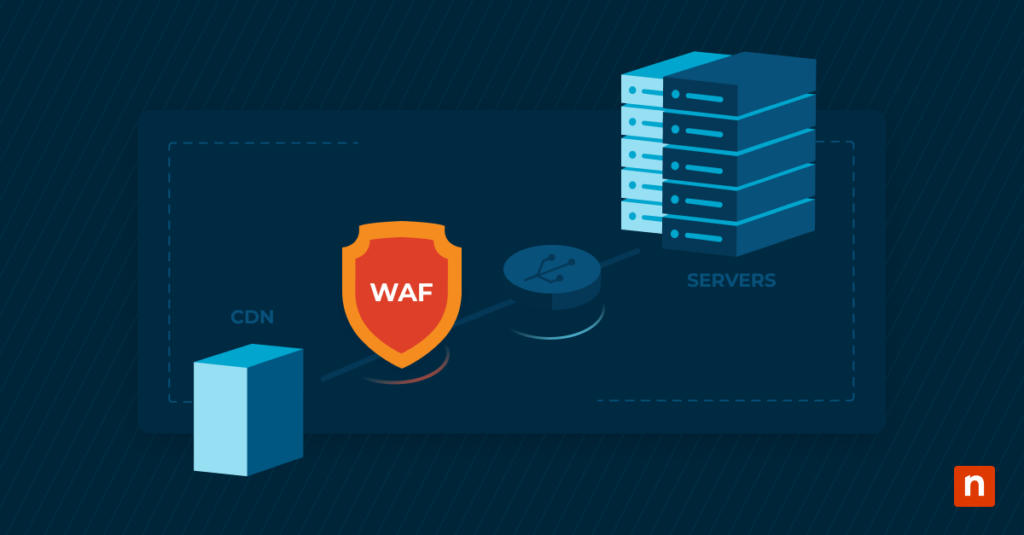
A firewall acts as a barrier between the web application and the internet, monitoring and controlling incoming and outgoing traffic based on a set of predetermined security rules. By doing so, WAFs mitigate the risk of various cyber threats, ensuring the integrity and availability of web applications.
WAFs come equipped with a range of features and capabilities that contribute to their effectiveness. These include real-time monitoring, access control, and the ability to enforce security policies.
Additionally, WAFs often include features such as SSL/TLS termination, bot mitigation, and content filtering, providing a comprehensive defense against a multitude of threats.
WAFs work by inspecting and filtering HTTP traffic between a web application and the internet. They analyze this traffic for suspicious patterns or malicious payloads, preventing potential threats from reaching the web application endpoint. WAFs use predefined rules to identify and block common attack vectors, making them an essential component of a robust cybersecurity strategy.
WAF rules define the criteria for identifying and mitigating potential threats and are tailored to specific types of attacks, such as SQL injection or cross-site scripting. Configuring and maintaining these rules is crucial for ensuring the WAF’s effectiveness in safeguarding web applications against a diverse range of cyber threats.
Types of WAF
Web Application Firewalls come in various forms, including cloud-based, hardware, and software solutions. Cloud-based WAFs offer the advantages of scalability and flexibility, making them suitable for organizations with dynamic web traffic patterns.
Hardware WAFs, on the other hand, are physical appliances that provide dedicated protection, while software WAFs are deployed as applications within the organization’s infrastructure.
Deploying a WAF in the cloud brings several benefits, such as automatic updates, scalability, and ease of management. Cloud-based WAFs provide a centralized solution for organizations with distributed web applications, simplifying deployment and ensuring consistent security across all assets.
However, considerations such as data sovereignty and compliance must be addressed when opting for a cloud-based WAF.
How to implement a WAF
Before implementing a WAF, organizations must assess their specific web application security needs. This involves identifying potential vulnerabilities, understanding traffic patterns, and prioritizing the types of threats the WAF should address. From there, WAF implementation is a three-phase process:
- Select the right WAF solution for your organization: Choosing the right WAF solution involves evaluating factors such as scalability, compatibility, and the level of customization required. Organizations should select a WAF solution that aligns with their infrastructure, budget, and security requirements.
- Configure the WAF: Once a WAF solution is selected, proper configuration is crucial. This includes defining security rules, specifying allowed and blocked traffic, and configuring settings such as SSL termination and logging.
- Test and fine-tune WAF rules: After initial configuration, thorough testing is necessary to ensure the WAF operates effectively. Fine-tuning rules based on real-world traffic and attack scenarios helps optimize the WAF’s performance and minimize false positives.
Successful integration of a WAF requires compatibility with existing infrastructure components such as web servers, content management systems, and APIs. Ensuring seamless communication between the WAF and these elements is crucial for maintaining operational efficiency:
- Ensure smooth data flow while maintaining security: Integration should not compromise the flow of data. Organizations must strike a balance between security and usability, ensuring that the WAF effectively protects web applications without causing disruptions to legitimate data flow.
- Monitor and manage the WAF: Continuous monitoring of the WAF is essential for detecting and responding to potential threats in real-time. The WAF should generate alerts for suspicious activities, enabling timely incident response to mitigate potential risks.
- Apply updates and security patches regularly: To stay ahead of emerging threats, organizations must regularly update and patch their WAF. This ensures that the WAF remains equipped to counter new attack vectors and vulnerabilities.
Stop web attacks before they reach your app. Watch What Is WAF (Web Application Firewall) to see how it protects you.
Web Application Firewalls: A crucial component of modern cybersecurity strategies
As organizations increasingly rely on web applications for their day-to-day operations, the importance of WAFs in securing these applications cannot be overstated. WAFs act as a frontline defense, safeguarding against common web threats and bolstering the overall security posture of an organization.
WAF management can be simplified with a strong layer of defense that helps to reduce the attack surface, monitor and patch operating systems and applications, and monitor both end user and endpoint activity. Implementing Web Application Firewalls enhances an organization’s ability to withstand cyber threats, protect sensitive data, and maintain the integrity of their web applications and networks.