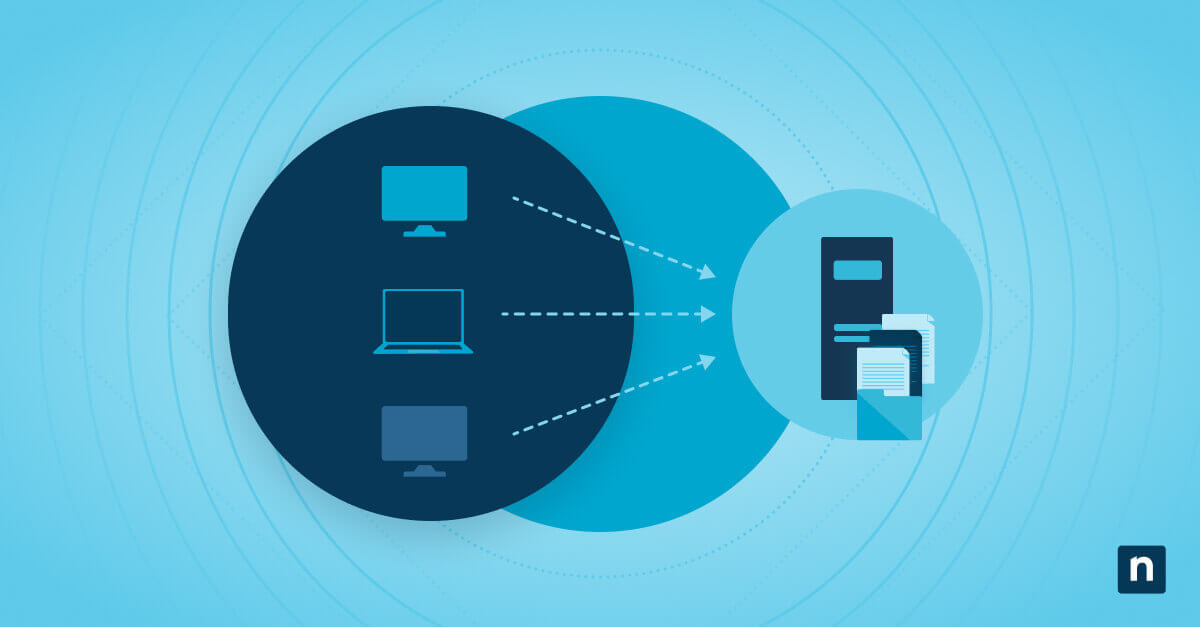
It’s challenging to manage laptops, computers, smartphones, tablets, and other IT endpoints all at once, especially when it comes to cybersecurity. Cybriant reveals that there are at least 5.8 billion enterprise endpoints in use, and that number will continue to surge as the remote workforce increases. To manage, monitor, and secure all these endpoints effectively, organizations rely on unified endpoint management (UEM).
Unified endpoint management (UEM) explained
Unified endpoint management (UEM) is a security and management solution that allows organizations to manage, monitor, and protect devices from a single pane of glass.
Before UEM, organizations relied on mobile device management (MDM) and enterprise mobility management to manage and protect mobile endpoints. To create unified endpoint management, organizations and IT leaders combined MDM, enterprise mobility management, and traditional IT management tools to create the ultimate endpoint management solution. With UEM, organizations are able to manage, update, secure, and control all their endpoints easily from one screen.
Download our eBook to learn how to choose the right UEM solution for your business needs.
The growing need for unified endpoint management (UEM)
During 2020, remote and hybrid work increased dramatically. To adapt to this change, organizations chose to distribute more devices to their employees. Even though 2020 is now in the past, the remote workforce continues to grow. Zippia’s remote workforce research shows that we can expect 36.2 million American employees to be working remotely by 2025. Additionally, many organizations are switching to a hybrid workforce, allowing their employees to participate in both remote and on-premise experiences. With all this remote and hybrid work, team members will be using even more endpoints to support their remote or hybrid lifestyle.
As remote and hybrid workforces continue to grow in popularity, organizations need an efficient way to monitor, manage, and secure all the endpoints that team members use. That’s where unified endpoint management comes into play. With a UEM solution, organizations can manage and protect their endpoints easily from a single console.
5 advantages of unified endpoint management (UEM)
1) Improves user experience
With a UEM solution in place, users are able to focus on their work instead of managing or protecting their devices. It ensures that users have a more flexible, secure, and hassle-free experience when using remote devices.
2) Protects endpoints & data
One of the main purposes of UEM is to protect endpoints and data from threats. From patching vulnerabilities to updating applications, unified endpoint management offers multiple ways to automate endpoint security, reducing the need for manual intervention.
3) Reduces compliance issues
As compliance standards change, UEM helps ensure that all your devices remain up-to-date and in compliance with regulations. This reduces any compliance issues that could negatively affect the IT team and the entire organization.
4) Supports bring your own device (BYOD)
Bring your own device (BYOD), is a policy that allows employees to use their own devices for work-related tasks. These devices can be tricky to manage and secure, but with UEM, organizations can support this policy and allow employees to use their own devices if necessary.
5) Provides valuable info
Unified endpoint management collects valuable data about endpoints that can be used for business decisions. Additionally, this information can be used to identify areas for improvement and set goals to improve the IT team and its performance.
What to look for in a UEM solution
Because every IT team faces different challenges, it’s tough to find a one-size-fits-all UEM solution for an organization. However, as you search for your UEM software, keep in mind that there are standard unified endpoint management criteria that every worthwhile solution will meet, such as:
-
Security
The unified endpoint management solution you choose should provide top-notch endpoint security to protect confidential information. Additionally, a UEM solution should safeguard endpoints and data even when employees choose to work remotely on various networks.
-
Access
Access management allows team members to control user and device access to ensure that information doesn’t fall into the wrong hands. There are many security policies and methods that UEM software uses to help you manage remote access, such as encryptions, password requirements, and multi-factor authentication systems.
-
Compatibility
Compatibility is an important factor to consider when adding a new UEM solution to your IT environment. You’ll want to ensure that the software you choose is compatible with your other systems and runs smoothly without creating any issues.
-
Ease of use
One of the main reasons why organizations adopt UEM is to reduce management complexity. A UEM system must be intuitive and easy for team members to access and use.
Centralize your endpoint management with NinjaOne
If you’re looking for a unified endpoint management solution that centralizes processes, offers multi-platform management, and is built for remote or hybrid workforces, look no further than NinjaOne. This efficient, all-in-one solution also offers network monitoring and management, OS and third-party application patch management, endpoint monitoring and alerting, and much more. Learn how to navigate the digital landscape with confidence and select the optimal UEM solution tailored to your needs.