Security of data is essential in a business and technology environment where consumers are increasingly seeking cost-effective, secure, and scalable data storage solutions. Although you may think your security practices are effective, guidelines like SOC 2 can help you determine how well you’re really doing without the risk of any legal consequences or fines.
SOC 2 compliance is designed to detect any data security issues and give you some direction for fixing those issues since it demonstrates what and where you could improve. If your policies and procedures are efficient and perform well in the SOC 2 audit, you can receive a certification that bolsters your reputation and potentially your customer count. Although becoming SOC 2 compliant may seem challenging, it’s well worth the effort when you consider the high numbers of data breaches and security incidents.
What is SOC 2 compliance?
Originally developed as a data privacy and security standard for accountants, SOC 2 is a way to assess whether your organization is appropriately handling customer data. Customers should be able to trust that you will have their data available, secure it to ensure privacy and data integrity, and restrict sharing.
As an IT professional, SOC 2 compliance should be a priority for keeping your client data as secure as possible. Since your clients trust you with access to their systems and data, you must protect that trust. Although the SOC 2 framework shares some similarities with other guidelines, such as NIST (National Institute of Standards and Technology), it focuses specifically on data that your organization stores in the cloud.
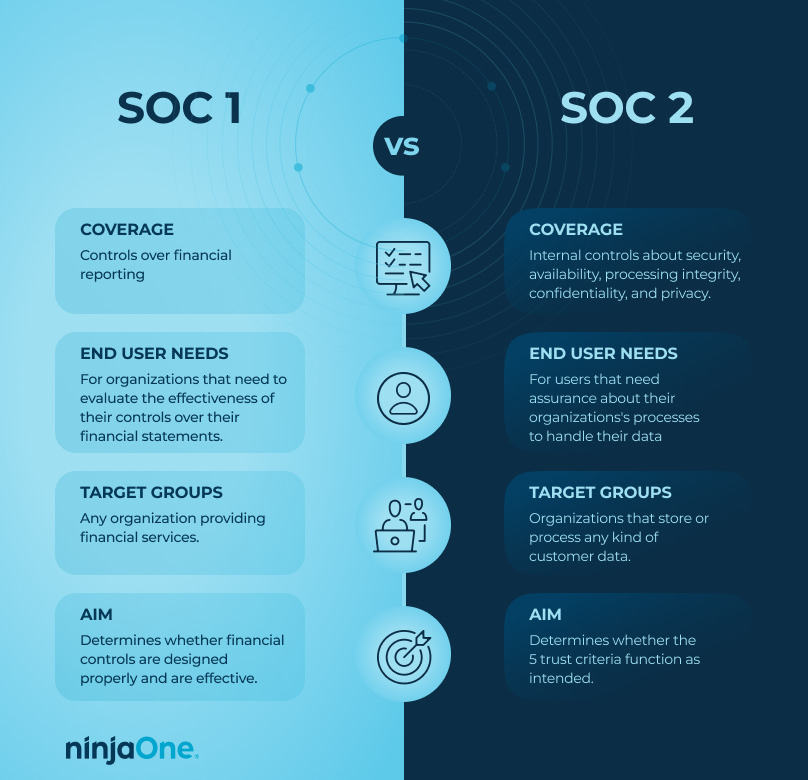
SOC 1 vs. SOC 2: Which one should you choose?
To recap:
- SOC 1 examines your organization’s control over financial reporting.
- SOC 2 focuses on the operations and compliance aspects of your data gathering and management protocols.
While both SOCs may overlap, SOC 2 assures customers that their data is adequately protected. Alternatively, SOC 1 reports analyze an organization’s control over its financial operations.
If you’re a service-based organization looking to become SOC compliant, you may wonder which report type you need. It is best to ask your CPA for specific information for your organization, but essentially, choosing the right type depends on what you want audited.
Keep in mind that both SOC reports have two types: Type 1 and Type 2. Thus, you can have SOC 1 Type 1, SOC 1 Type 2, SOC 2 Type 1, and SOC 2 Type 2.
Type 1 SOC reports
Type 1 SOC reports usually explore the functionality of the organization’s control at a single point in time, such as “Audit report for June 3, 2024.”
Type 2 SOC reports
Type 2 SOC reports, on the other hand, test your organization’s controls over a range of time, such as “Audit report for the period of June 3, 2023 to June 3, 2024.” These ranges are usually six to 12 consecutive calendar months.
Thus, an organization with SOC 2 Type 2 certification, such as NinjaOne, maintains consistent effectiveness over the tested controls.
Why is SOC 2 compliance important?
SOC compliance is essential for any organization to maintain its competitive advantage and assure its clients that it has the best tools and strategies to serve them. Specifically for SOC 2, compliance plays a unique role in your client relationships, guaranteeing that your IT enterprise can address common cloud computing risks while also demonstrating a commitment to data security, privacy, and overall protection of customer information.
Understanding SOC compliance for your MSP builds trust with customers and stakeholders and strengthens your security posture against potential breaches.
Who needs SOC 2 compliance?
Typically, SOC 2 compliance is needed by service organizations, such as, but not limited to:
- Software as a Service (SaaS) companies that offer various programs, apps, solutions, and websites.
- Managed IT and security service providers
- Businesses that facilitate or manage sensitive or personal data, particularly financial or accounting data.
- Companies that provide business and intelligence services.
- Groups that offer customer management or other similar services.
Keep in mind that this is not an exhaustive list. The American Institute of CPAs (AICPA) also provides other regulatory guidelines inside their SOC framework for more nuanced businesses, such as those within the supply chain and logistics industries.
Benefits of SOC 2 compliance
Although SOC 2 compliance is generally a voluntary certification, there are several benefits to undergoing an audit and becoming certified:
- Data protection: The importance of protecting sensitive data and maintaining information security cannot be understated. You must protect both your customers’ and your organization’s private information to protect everyone’s interests and identities.
- Enhanced trust and credibility: Clients and stakeholders are more likely to trust that you’re handling their data properly if you’re actively pursuing SOC 2 compliance. Following a trusted framework is more likely to increase your credibility than flying by the seat of your security pants, so to speak.
- Competitive advantage: Customers seeking your services are often looking for assurances that you will handle their data securely. A SOC 2 certification provides this assurance and gives you an advantage in the marketplace.
- Legal and regulatory compliance: SOC 2 requirements typically go above and beyond legal requirements, so if you follow SOC 2 guidelines, you shouldn’t find yourself paying fines for lack of compliance.
SOC 2 audit and certification
To become SOC 2 certified, you need an external auditor, generally a certified public accountant (CPA), to audit your organization. Whether you have an audit that covers only a specific moment in time (Type I) or an audit that covers 6-12 months (Type 2), the process is roughly the same. Initially, you should determine what you want from the audit and what information will be most helpful in improving your security posture. Next, when you’re ready to hire an auditor, create a comprehensive list of your policies and procedures. The auditor will be able to use these to compare typical behavior with ideal behavior.
Once the audit begins, you’ll review the desired outcome with the auditor and work out a timeline for the process. The audit will consist of the auditor testing the policies and procedures you’ve already written to determine their effectiveness. Finally, you’ll receive a report with documented results.
For a successful SOC audit, complete an internal audit first. This practice run will help you identify potential problems and fix them before bringing in the external auditor. Implement data access controls and automated monitoring, or consider using a remote monitoring and management (RMM) solution that can alert you to potential vulnerabilities and help you remotely install patches or updates.
SOC 2 compliance implementation and key considerations
If you’re planning to become SOC certified, detailed documentation of your organization’s policies, procedures, and controls is essential. For the highest levels of security and business continuity, logging your activities can help keep other members of your team informed and minimize disruptions during times of change.
You are not the only person who can affect your environment. Whether internal or external, other users may have differing interpretations of your policies or fail to follow them correctly. Training is essential to ensure compliance. It’s also important to limit access to certain data for team members who don’t need it and implement automated monitoring solutions.
The AICPA has defined 5 trust services criteria for managing customer data:
These are security, availability, processing integrity, confidentiality, and privacy.
- Security: Generate reports frequently to confirm that your policies and procedures effectively secure data.
- Availability: Create disaster recovery plans that prepare you for the worst. Use backup solutions to ensure that customers can access their data if your organization is the target of ransomware or other cyberattacks.
- Processing integrity: Review your internal policies and procedures to ascertain whether anything is ineffective. Monitor your environment and employees for compliance. This also includes regularly reviewing your IT network for dirty data.
- Confidentiality: Utilize encryption and firewalls to minimize the risk of unauthorized access to your cloud storage.
- Privacy: Your organization must have sufficient verification and authentication protocols in place. Employees should be using multi-factor authentication, creating single-use passwords, and only accessing the data they need to do their jobs.
It’s worth noting that the AICPA only uses these trust criteria as guidelines for its SOC 2 compliance. Because every organization is unique, SOC 2 compliance can be customized for specific services, with organizations needing to state their security goals and intentions before any audit.
The SOC 2 auditors will then evaluate an organization by comparing its performance with their stated intentions. Auditors then align the stated plans with the 5 trust criteria.
Integration of SOC 2 compliance with IT infrastructure
Incorporating SOC 2 guidelines into your existing IT infrastructure and security and compliance frameworks may seem intimidating, but it’s essential for your continued success. Customers want to know that they can trust you with their data, and if you complete an audit and then create a roadmap for implementing the requirements, the time and resources used are worth the expense.
Your roadmap should include creating new policies and procedures that sufficiently protect data. Ensure that you’re using encryption and multi-factor authentication, as well as controlling access to data. To keep attackers out, implement automatic monitoring, alerts, and firewalls. Finally, create a disaster recovery plan to help you minimize downtime and recover quickly after any potential data disaster.
Data security practices are essential for modern organizations
To stay competitive and relevant, your organization needs to have robust data security practices, and becoming SOC 2-compliant can give you something to aim for while improving customer confidence. If you leverage technologies and tools that are already SOC 2 certified, like NinjaOne, becoming SOC 2 compliant within your organization will be faster and easier. SOC 2 compliance will strengthen your organization’s data posture, decrease your risk of security incidents, and improve the likelihood that potential customers will entrust you with their data.









