Key points
- A Virtual Private Network (VPN) is an essential part of IT management that allows users within an organization to securely connect to servers and networks from virtually anywhere.
- The IT security team can set up a VPN on Windows Server 2022 to leverage its robust security features and enhancements, enforcing more secure remote access.
- For prerequisites, IT administrators must ensure the server meets system, network, and access requirements before installation.
- The process begins by installing the Remote Access role and enabling the DirectAccess and VPN (RAS) services through Server Manager.
- After installation, administrators configure the VPN using the Routing and Remote Access (RRAS) setup wizard, selecting appropriate VPN protocols, authentication methods, and encryption settings.
- Post-setup configuration focuses on enabling secure remote access, defining user permissions, setting up routing, and configuring NAT for connected devices while ongoing monitoring, logging, and auditing are essential to maintain VPN performance, detect anomalies, and prevent unauthorized access.
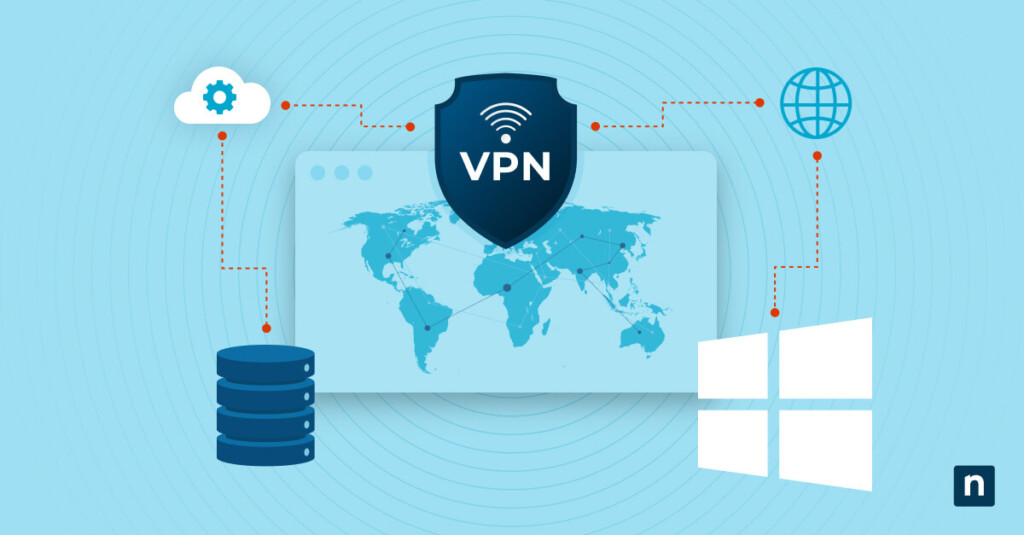
A VPN, or Virtual Private Network, enables secure communications over an untrusted network. It enables users to connect to servers and networks from virtually anywhere, creating a secure tunnel between the user and a remote network or server. VPNs ensure data privacy and prevent unauthorized access, ensuring the data transmitted remains confidential and protected from external threats.
Windows Server 2022 is the latest iteration of Microsoft’s server operating system, known for its robust security features and enhancements over previous versions. Setting up a VPN on Windows Server 2022 allows organizations to leverage those advancements in server technology to secure their remote access.
Keep remote Windows devices secure with NinjaOne’s comprehensive endpoint management tool.
Learn more about NinjaOne Endpoint Management.
In this guide, we will walk you through the process of installing and setting up a VPN on Windows Server 2022, equipping you with the knowledge required to establish a secure remote access solution.
Prerequisites for installing a VPN on Windows Server 2022
Before looking at the installation and setup process, there are several prerequisites you need to consider:
System requirements
- A dedicated Windows Server 2022 machine, preferably with a static IP address.
- Sufficient CPU and RAM resources to handle VPN traffic.
- Adequate storage space for system and log files.
Networking requirements
- A stable internet connection with a public IP address.
- An understanding of your network’s topology and addressing scheme.
- Knowledge of DNS and DHCP configurations.
Administrator-level access
You must have administrator access to the Windows Server 2022 machine to install and configure the VPN server role.
Step-by-step guide to installing a VPN server on Windows Server 2022
Before proceeding, make sure your Windows Server 2022 is up-to-date with the latest updates and patches. Ensure that your server’s firewall and security settings are configured to allow VPN traffic. The steps below are all that is required to install and configure VPN services on Windows Server 2022.
Installing VPN role services
Before we can configure a Windows 2022 Server VPN, we need to install the role using the steps below:
- Launch the Server Manager on your Windows Server 2022.
- Click on “Add roles and features” and proceed through the wizard.
- Select “Remote Access” as the role you want to install.
- In the Role Services section, choose “DirectAccess and VPN (RAS).”
- Complete the wizard to install the selected role services.
Running the Windows VPN server setup wizard
Once the VPN role has been installed, we need to setup the VPN server:
- After installing the role services, open the “Remote Access Management Console” from the Server Manager.
- In the console, click on “DirectAccess and VPN.”
- Right-click on your server and select “Configure and Enable Routing and Remote Access.”
- Follow the setup wizard, which will guide you through the configuration process. This will require knowledge of your network topology and the configuration items listed in the prerequisites section.
Additional configuration settings for remote server access
During the setup, consider the following additional configuration settings:
- VPN protocol: Determine which VPN protocol to use. Common options include PPTP, L2TP, and SSTP. Each has its advantages and disadvantages, so choose the one that aligns with your security and performance requirements.
- IP address assignment: Decide how IP addresses will be assigned to VPN clients. Options include using a DHCP server, assigning static addresses, or using the built-in Windows Server DHCP service.
- Authentication methods: Select the authentication methods to verify the identity of VPN users. Common methods include MS-CHAP, EAP-TLS, and others.
- Security and encryption: Configure the security settings for your VPN, specifying encryption algorithms and security protocols.
How to set up a VPN for remote access
To enable remote access for your VPN, a few essential configuration settings are required post-setup:
- User access: Define which users or groups are allowed to access the VPN. You can integrate with Active Directory for user authentication.
- Routing: Decide whether the VPN server will act as a router, directing traffic between the VPN clients and the internal network.
- Network address translation (NAT): If your VPN server needs to provide internet access to clients, configure NAT settings accordingly.
Understanding RAS VPN settings
Remote Access Service (RAS) settings are critical for inbound VPN functionality. These settings include:
- VPN dial-in settings: Define the maximum number of VPN sessions and idle timeouts.
- VPN ports: Specify the ports that the VPN server will use for incoming connections.
- VPN policies: Configure security policies to determine which users can access the VPN, what authentication methods they should use, and other security settings.
- Logging and auditing: Enable detailed logging and auditing to monitor VPN activity and troubleshoot issues.
Setting up access controls and permissions
Access controls and permissions are crucial for maintaining the security of your VPN, and for ensuring only permitted users and systems are able to achieve remote access:
- Firewall rules: Ensure that the server’s firewall allows incoming VPN traffic on the configured ports.
- User permissions: Review user access permissions and verify that only authorized users can connect to the VPN.
- Security policies: Establish and enforce security policies to protect VPN traffic from potential threats.
How to connect remote VPN server with other devices
Once your Windows Server 2022 VPN is set up, connecting to it from remote devices is achieved using the following steps:
- On the client device, open the VPN client software.
- Enter the server’s public IP address or hostname.
- Input your VPN username and password.
- Connect to the VPN.
Monitoring your VPN server
Regularly monitor your VPN server to ensure its security and performance:
- Review server logs for any anomalies or issues.
- Conduct security audits to identify vulnerabilities.
- Monitor VPN traffic for unusual patterns or unauthorized access.
Make managing your remote Windows devices fast and easy with NinjaOne.
Discover what NinjaOne Windows Endpoint Management has to offer.
Secure remote access to your network and server resources
As data security is paramount and remote working is well established, a well-configured VPN should be the cornerstone of your IT infrastructure. By following the steps outlined in this guide and adhering to best practices for VPN security, you can ensure that your Windows Server 2022 VPN is a robust and reliable solution for remote access.
A video tutorial on How to Install and Set up a VPN on Windows Server 2022 is available.