Today, people and businesses use endpoints to accomplish everything from day-to-day tasks to large projects. Endpoints include the physical devices that connect to and communicate with a central network. They are used to manipulate data or exchange information.
The number of endpoint devices that average businesses and enterprises manage is 135,000, and that number continues to grow. Endpoint monitoring and management involve keeping track of those many devices and ensuring they are in optimal condition. Learn more about endpoint monitoring and why your organization’s IT environment needs it.
Why you should care about endpoint security
Endpoints are the devices used for productivity and to contribute to modern organizations. Since endpoints are closely connected to a business network and have a lot of capabilities, they are a tool that can be used for either productivity by end users or disruptions by threat actors. Endpoint security is important because you need to ensure that your network is secure from all access points to prevent possible cyberattacks.
Securing endpoints through endpoint monitoring and management also helps to drive business efficiency. It makes tasks and processes like patch management, endpoint maintenance, and new device onboarding a lot easier and much more effective for securing your devices.
Examples of endpoint security threats
Below are a few examples of common endpoint security threats that businesses face:
Phishing
Approximately 6 billion phishing attacks were expected to occur in 2022. Phishing scams, which are different from email spoofing, are sent through emails or text messages that appear to be trustworthy but are used to steal user data such as login credentials, account numbers, financial information, or even Social Security numbers.
Malware
In the first half of 2022, over 270,000 new variants of malware were detected. Malware refers to any software, program, or file used for the purpose of stealing data or causing damage to a device or system.
Ransomware
Ransomware is a certain type of malware that threatens to publicly release or permanently block access to data until a “ransom” has been paid. Demands for ransom have reached as much as $70 million to unlock computers after an attack.
What is endpoint monitoring?
Endpoint monitoring is keeping track of and auditing the health, status, risks, and activity of endpoint devices. It is an ongoing process that systematically manages endpoints to keep them safe, secure, and performing optimally.
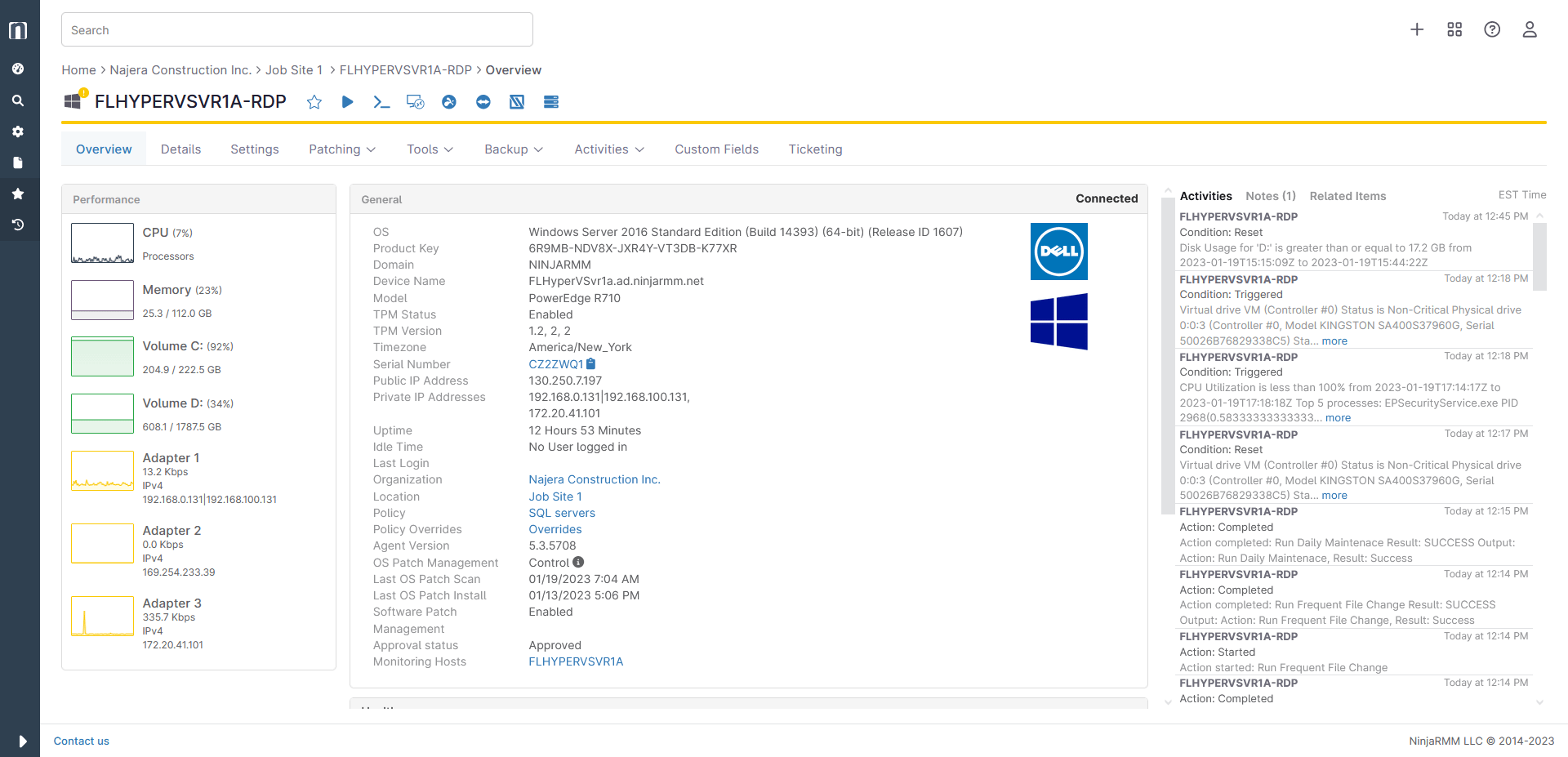
Endpoint Monitoring Example
Below is a screenshot of endpoint monitoring software, taken directly from NinjaOne’s endpoint monitoring software. It contains the endpoint’s performance metrics in the left column, activities of the endpoint in the right column, and general endpoint information in the middle section.
3 benefits of endpoint monitoring
Monitor live data
Active endpoint monitoring provides you with real-time data from your endpoints. At any given moment, you’re able to see all tracked metrics and whether a device is functioning correctly. Knowledge is power, and that’s especially true when it comes to managing endpoints.
Proactively identify issues
The 24/7 monitoring of key metrics allows you to gain insight into the health of your devices. When a metric goes beyond the preset parameters, this lets you know that something is off, and you can quickly investigate to determine the problem. Otherwise, you’re left to deal with the outcome of issues and have to search for the root issue.
Increase security
Endpoint monitoring helps you to drastically increase your endpoint security. Because of the high visibility you gain through this process, you are able to see your entire network of endpoints and know the health status from a central location. Increased visibility also helps you determine when a threat actor has entered or whether a cyberattack is occurring.
What does good endpoint monitoring look like?
Download your free Endpoint Monitoring and Alerting Playbook 📕
3 challenges of endpoint monitoring
1. Endpoint monitoring tools
One of the biggest upfront challenges to endpoint monitoring is determining the right tools for your environment. Organizations have varying wants and needs with different types of endpoints, IT environments, and even business structures. We’ll discuss how to find an endpoint monitoring solution later in the article, but just know that this is a common challenge for companies across all industries.
2. Implementation of the monitoring process
If there’s not already some sort of monitoring process in place, it can be a struggle to implement one in your organization. However, endpoint monitoring is increasingly necessary to ensure a safe, secure, and functional network. Consult IT experts and create a plan in advance for how to apply endpoint monitoring software in your IT environment and execute the endpoint monitoring process.
3. Ensuring all endpoints are monitored
Endpoint monitoring only works well if all endpoints in the IT environment are connected to the endpoint monitoring software. Otherwise, you may have rogue devices that connect to your organization’s network, which could potentially compromise critical data or risk the safety of the organization. Create a system where every new endpoint is added to the monitoring software, or find a software solution that can possibly identify or detect new endpoints that connect to organizational resources.
How to find an endpoint monitoring solution
With a solid understanding of what endpoint monitoring is, as well as the benefits and challenges of it, what should you look for when considering endpoint monitoring solutions? A few key endpoint monitoring capabilities that increase the effectiveness of the overall process include:
Remote monitoring
As the remote and distributed workforce continues to grow in size, on-prem monitoring of devices is no longer sufficient. Remote monitoring allows you to track all devices wherever they are, enabling you to optimize the health and security of endpoints no matter their location.
Live telemetry data
Automatic transmission of endpoint metrics takes out the manual process of gathering endpoint data. Endpoint monitoring software can also notify you when certain metrics reach beyond set parameters, and create detailed reports of endpoint health overall.
Ability to monitor and manage
Endpoint monitoring is powerful in its ability to track a variety of endpoint metrics, but it doesn’t do you much good unless you can act on the information that is gathered. When data shows that an endpoint is experiencing an issue, the ability to take action and make changes to resolve the issue enhances the health and increases the security of your endpoint devices.
Start monitoring your endpoints with NinjaOne
Endpoint monitoring is a powerful process that can upgrade your IT environment and enhance the performance of your endpoints. It’s also an invaluable tool when it comes to creating a safe network and increasing the security of your endpoints.
NinjaOne’s Unified Endpoint Management software gives you the ability to monitor and manage your organizational endpoints from a central location. You can support any endpoint, no matter its location, automate redundant monitoring and management of IT tasks and increase your efficiency. Sign up for a free trial today to gain these endpoint monitoring and management benefits.