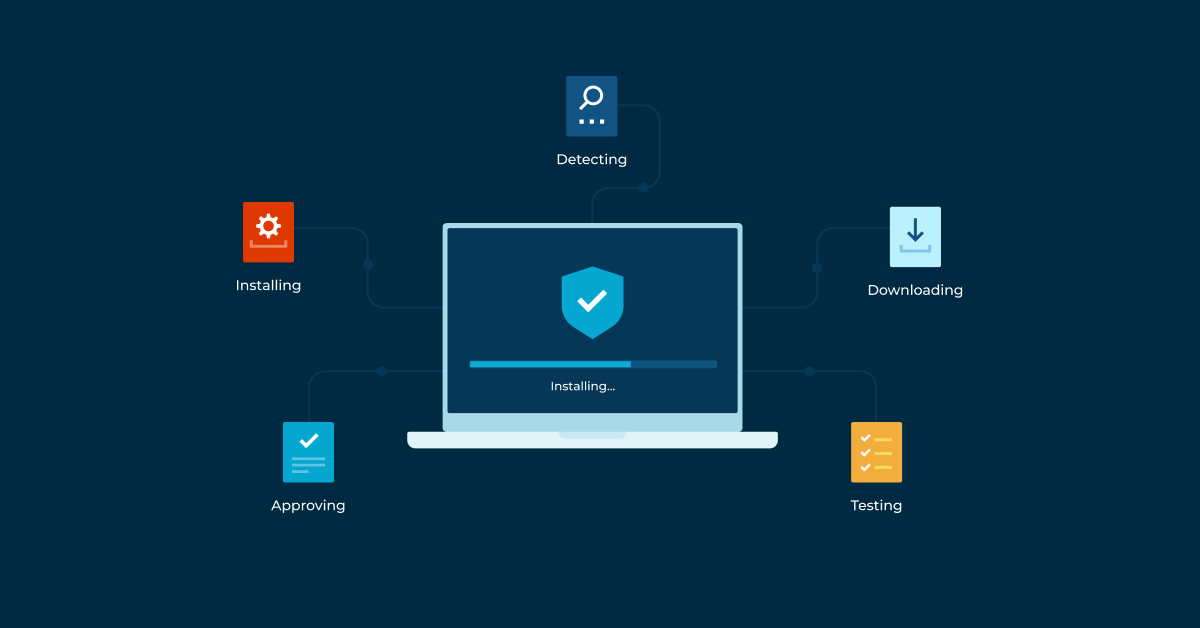
Key Points: Best Practices for Patch Management
- What is patch management: Patch management covers tasks related to ensuring endpoints and programs are updated and secured.
- Why is patch management important: Updated systems are more likely to prevent cyberattacks, especially those targeting known vulnerabilities. It’s also important for maintaining compliance and system compatibility.
- How often should SMBs patch their systems: Critical security patches must be deployed as soon as they become available or after testing. Other updates may follow a regular interval or a staggered rollout.
- Can patch management be automated: Yes. For instance, patch management with NinjaOne supports automated scanning, deployment, and reporting. Automation significantly reduces human error and saves crucial business resources.
Patching vulnerable software and systems is more important and challenging to keep up with than ever. Here’s how IT pros can make their patch management process more efficient, eliminate disruption, and keep their networks secure.
What is patch management?
Patch management covers tasks related to ensuring endpoints and programs are updated and secured. This generally involves the acquisition, testing, and deployment of software updates (patches) for operating systems, applications, and firmware across managed devices within the IT environment.
While Windows devices continue to dominate the market, Mac and Linux endpoints are becoming more prevalent. And so, modern patch management requires a tool to secure all three platforms effectively.
💡 Tip: To learn more, download our patch management guide for IT leaders.
Why is the patch management process important?
Patching keeps systems and applications running smoothly and is also one of the core activities involved in keeping today’s organizations secure.
According to an IBM report, the global average cost of a data breach in 2025 will reach a staggering $4.4 million. Compliance penalties and loss of trust among clients further compound these setbacks.
Leaving machines unpatched makes them vulnerable to cyber attacks, and the risk is anything but theoretical. In fact, according to the Ponemon Institute, the majority of data breaches (57%) can be directly attributed to attackers exploiting a known vulnerability that hadn’t been patched.
Patch management challenges for SMBs
If some of the largest, most well-funded organizations in the world are having difficulties with patch management, what chance do small and medium-sized businesses with limited IT support have? Here are some common challenges for moderately sized IT stacks:
- SMBs may lack funds for enterprise-grade patch management solutions.
- SMBs frequently have a mix of new and old devices, plus different operating systems (Windows, macOS, Linux) and applications.
- Small IT teams without time or manpower to constantly monitor and deploy patches.
- Lack of testing environments.
- Manual patching is a time-consuming process and often gets deprioritized.
Some of the biggest patch management challenges involve the process being time-consuming, complicated, and disruptive to end users. As a result, it’s easy to put patching off or simply have important updates get lost in the shuffle.
Unfortunately, the risk that unpatched systems pose is increasing. Once a vulnerability has been disclosed and a patch has been released, it’s a race for organizations to apply the patch before attackers begin actively exploiting it.
A real-world use case for solving patch management issues
For many small businesses, the solution to staying on top of patching cycles is to outsource the burden to managed services providers (MSPs). The MSPs, on the other hand, are pushing the envelope using advanced and specialized solutions, like an RMM.
“We use Ninja to automate patching across our end-user devices and servers. We save a ton of time on patching now as we no longer have any manual steps in our patching workflow.”
Martin Wells, CEO of Syscomm Group
👉 Read: Learn how the Syscomm Group was able to leverage NinjaOne to get the most out of their security monitoring.
An RMM is an excellent IT management solution for streamlining and automating the hardest parts of IT. But the strategy around it must also be resilient and scalable. To give you a better idea, continue with our recommendations below on how MSPs and IT leaders can build a cost-efficient and enduring patch management framework.
10 key steps in a patch management process
Below is a 10-step patch management process template highlighting the fundamental considerations that need to go into any patch management plan. Before diving into this workflow you’ll want to make sure you’ve established clear roles and responsibilities for each step, and that all key stakeholders are fully on board.
⚠️ To avoid common pitfalls along the way, be sure to watch our video on Patch Management Mistakes and How to Avoid Them.
Step 1: Discovery
First, you need to ensure you have a comprehensive network inventory. This includes understanding the types of devices, operating systems, OS versions, and even third-party applications at the most basic level.
Many security breaches occur because IT neglects or forgets certain endpoints. MSPs should be proactive and utilize network inventory tools to scan their clients’ environments on schedule and attain clear visibility over the managed network.
Step 2: Categorization
Segment-managed systems and/or users according to risk and priority.
For instance, you may filter via machine type (server, laptop, etc.), operating system, OS version, user role, etc. This will allow you to create more granular patching policies instead of taking a one-policy-fits-all approach.
Step 3: Patch management policy creation
Create patching criteria by establishing what will be patched and when, under what conditions.
For example, determine which endpoints need to be automatically updated and how frequently they should be patched. The patching schedule for laptop end users may be weekly, while patching for servers may be less frequent and done manually.
You may also consider having flexible workflows for different patches, with some having a quicker or more extensive rollout process (think browser updates vs. OS updates; critical vs. non-critical updates, for example).
Finally, you’ll want to identify maintenance windows to avoid disruption (take into account time zones for “follow the sun” patching, etc.) and create exceptions.
Step 4: Monitor for new patches and vulnerabilities
Understand vendor patch release schedules and models. Then, look to identify reliable sources for timely vulnerability disclosures. Create a process for evaluating emergency patches.
Step 5: Patch testing
Create a testing environment or an isolated segment to avoid being blindsided by unintended issues. This initiative should include creating backups for a reliable and convenient rollback protocol.
Also, validate successful deployment and monitor for incompatibility or performance issues.
Step 6: Configuration management
Document any changes about to be made via patching. This will come in handy should you run into any issues with patch deployment beyond the initial test segment or environment.
Step 7: Patch rollout
Follow the established patch management policies you created in step 3. For greater efficiency, identify which systems, applications, or devices require updates and prioritize based on risk level (e.g., security patches vs. feature updates).
Step 8: Patch auditing
Conduct a patch management audit to identify any failed or pending patches.
At the same time, continue monitoring for any incompatibility or performance issues. Tapping specific end users who can help by being additional eyes and ears is also a good idea.
Step 9: Monitoring and reporting
Produce a patch compliance report you can share with your clients to gain visibility into your work. Track which patches have been applied to maintain compliance with security standards. Additionally, set up a system that tracks patching status across systems, so that remediation can be done more quickly and timely.
Step 10: Review, improve, and repeat
Establish a cadence for repeating and optimizing steps 1-9.
The workflow should include phasing out or isolating any outdated or unsupported machines, reviewing your policies, and revisiting exceptions to verify whether they still apply or are necessary.
What are the best practices for Patch Management?
As the demand for effective patch management continues to become more integral, MSPs need to improve on their own process and offerings or risk falling behind. Here are three keys to MSPs providing smarter, more efficient, and more effective patch management services in 2022.
1) Automate patch updates
Patching is a game that’s extremely easy to fall behind in, especially if you’re still relying on identifying, evaluating, and deploying patches manually. Cloud-based, automated patch management software allows MSPs to schedule regular update scans, and ensure patches are applied under specific conditions or automatically.
How NinjaOne can help:
- Automate patching for Windows and third-party software from over 120 vendors.

- Easily configure patch scanning and update schedules for specific segments of devices or users. Get granular control or set it and forget it.
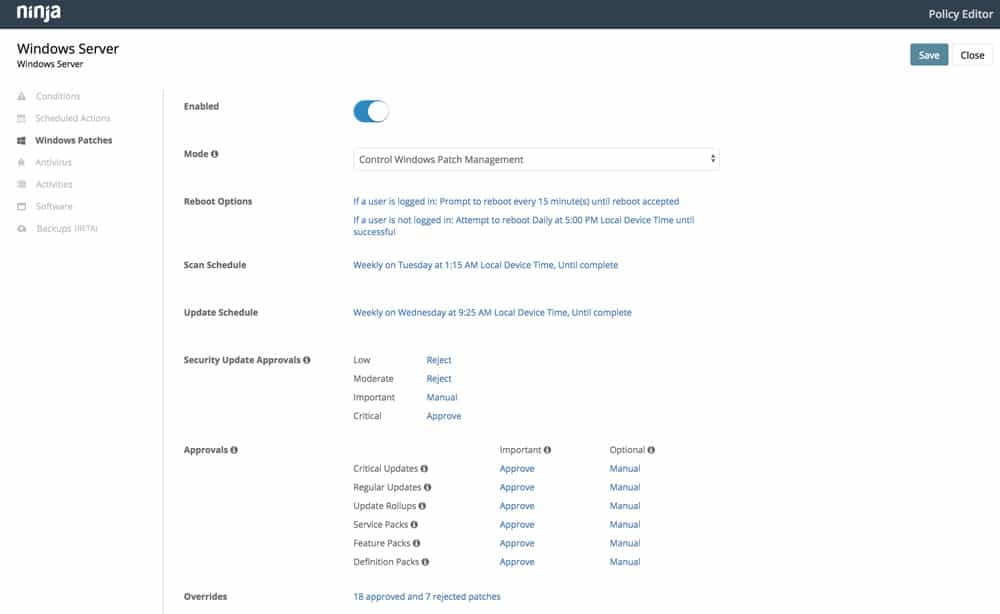
- Less time combining through new update releases and vulnerability disclosures, more time growing your business.
2) Mitigate patch deployment validation with audit reports
Despite patching automation becoming increasingly popular, MSPs unfortunately can’t always assume automated patching solutions are working as promised.
That means time-consuming, manual validation. Developing scripts or processes to ease that burden (or, better yet, utilizing solutions that don’t require double-checking) is a worthwhile investment.
How NinjaOne can help:
- Gain access to detailed patch audit reporting.
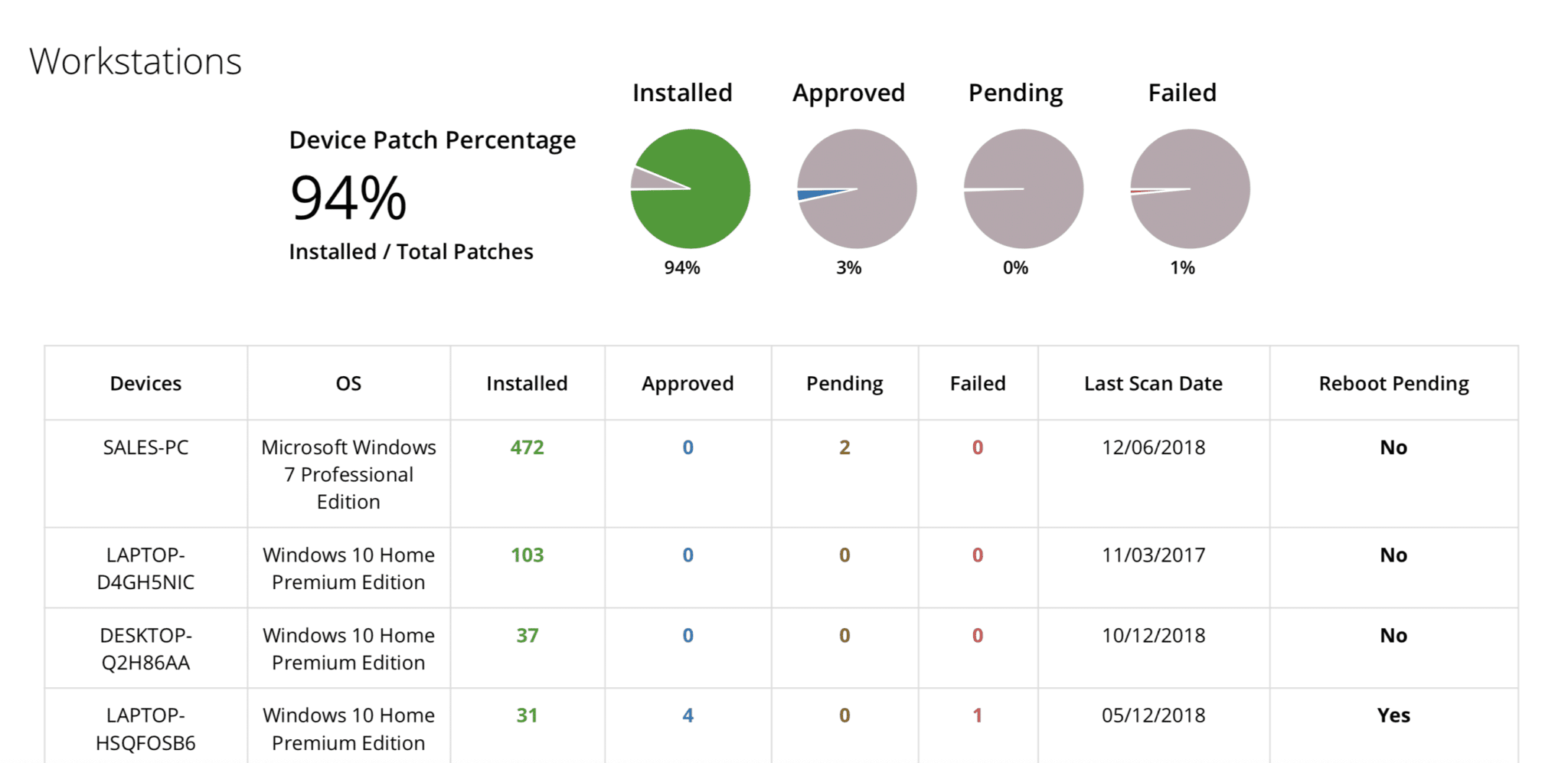
- Eliminate the guesswork by ensuring you have access to reliable real-time information.
3) Streamline reporting
Everything you do as an MSP should be communicated as value-add to your clients. Patch management should be no exception, but delivering patch management audit reports should be as automatic as possible. After all, the more time reporting takes, the less time you have for providing additional services and growing your business.
Implementing your patch management process
The ultimate goal of patch management is to ensure that all software solutions in the IT stack and managed network are updated and secure. On balance, the patch management workflow should include these steps.
- Determine baseline data
- Establish priorities based on risk and criticality
- Create a patch management policy
- Test patches, new integrations, and system compatibility
- Set up a resilient backup and recovery solution
- Monitor patch updates and fix issues
Additionally, regularly check individual endpoints for compliance with regulatory standards such as the GDPR and PCI DSS. A capable RMM can also automate endpoint security at scale.