Effortless Automated Configuration Enforcement with NinjaOne
A Smarter Way to Stay Consistent and Compliant
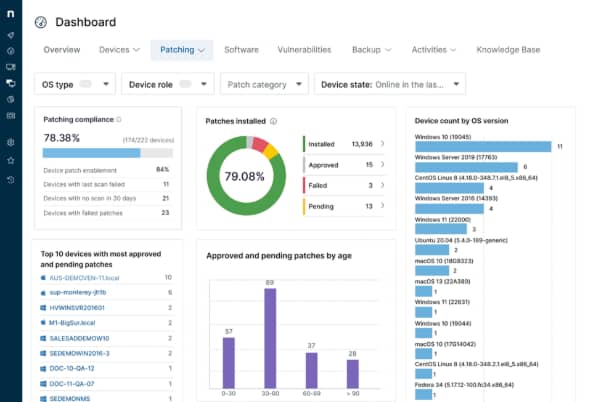
Continuous Configuration Compliance Monitoring
With real-time visibility into device configurations, IT teams can instantly detect deviations and automatically trigger corrective actions. This reduces downtime, enforces accountability, and supports IT governance efforts.
Streamlined Patch and Software Policy Enforcement
Unified Device Management Across Platforms
Reduced Human Error with Pre-Set Automation Logic
Improved Audit Readiness and Compliance Confidence
Powerful Features That Deliver Consistency at Scale
Customizable Configuration Policies by Device Role or OS
Automated Remediation of Non-Compliant Devices
Role-Based Access for Configuration Control
Centralized Management Dashboard for Full Visibility
Seamless Integration with Scripts and Alerts
Lightweight Agent for Silent Background Operations
Built for Real-World IT Configuration Challenges
Maintaining Policy Compliance Across Remote Workforces
Standardizing Server and Workstation Setups in Multi-Site Operations
Ensuring Continuous Compliance for Regulated Industries
Experience Effortless Policy Control with NinjaOne
Automated Configuration Enforcement FAQs
What is automated configuration enforcement?
Automated configuration enforcement is the process of using software tools to ensure devices consistently follow pre-defined system, security, or software settings without manual intervention. It helps IT teams maintain a standardized environment by automatically detecting deviations and applying corrective actions in real time. This approach is essential in reducing misconfigurations, increasing reliability, and supporting scalable IT operations.
Why is configuration enforcement important for IT compliance?
Configuration enforcement plays a vital role in meeting IT compliance standards by ensuring that devices continuously adhere to required security and operational policies. Without it, organizations risk falling out of compliance due to configuration drift, exposing them to audits, penalties, or security vulnerabilities. Automated configuration compliance supports regulatory frameworks by continuously validating that system settings remain in their approved state.
Can I create custom policies for automated configuration enforcement?
Yes, NinjaOne allows IT administrators to create highly customizable policies tailored to different operating systems, device roles, or user groups. Whether you need to enforce software installations, system configurations, or user permissions, these policies can be defined and applied automatically. This flexibility is a key aspect of effective automated configuration management, enabling IT teams to scale consistent setups across diverse environments.
Does automated configuration enforcement work across Windows and macOS?
Absolutely. NinjaOne supports cross-platform configuration enforcement, allowing you to apply and manage policies across both Windows and macOS devices. This ensures consistent behavior regardless of the operating system, making it easier for IT teams to maintain standardization and reduce configuration drift in mixed environments.
How does automated configuration enforcement improve endpoint security?
By continuously monitoring and enforcing security-related settings—such as antivirus status, encryption, and patch levels—automated configuration enforcement helps eliminate gaps that could be exploited by attackers. It ensures that endpoints always remain in a secure and compliant state, reducing the likelihood of human error and strengthening your organization’s overall security posture.
Does NinjaOne provide reporting on configuration enforcement?
Yes, NinjaOne includes detailed reporting features that give IT teams visibility into policy enforcement activity across all managed devices. These reports can highlight compliance status, show when and how changes were applied, and help with audits or internal reviews. With this data, organizations can demonstrate accountability and maintain confidence in their configuration enforcement processes.
Related Resources
Computer Configurations
Configuration Management
Discover how NinjaOne makes configuration management effortless and scalable.
Device Security
