Threats & Patches
System Health Policy
Vulnerability Management
Patch Management
Patch Settings
Patch Deployment
Asset Management
Inventory
Application Management and Control
Prohibited Software
- NinjaOne
- Last updated
Security Configuration Management
What is Security Configuration Management?
Security Configuration Management (SCM) is the process that involves adjusting the default settings of an information system to enhance security and mitigate risk.
Here are some examples of misconfigurations that cybercriminals often exploit.
- Weak Passwords: Employees using weak, or default passwords provide easy access points for cybercriminals. SCM involves enforcing password policies, such as requiring strong passwords and regular password changes, to reduce this risk.
- Unpatched Systems: Failure to apply security patches leaves systems vulnerable to known exploits. SCM includes regular patch management to ensure that systems are up-to-date and protected against the latest threats.
- Misconfigured Firewall Rules: Incorrectly configured firewall rules may inadvertently allow unauthorized access to sensitive systems or data. SCM involves reviewing and optimizing firewall configurations to block malicious traffic effectively.
- Lack of Access Controls: Inadequate access controls can result in unauthorized users gaining privileged access to critical systems or data. SCM encompasses role-based access controls and least privilege principles to limit access only to authorized personnel.
- Unsecured Network Protocols: Using insecure network protocols exposes data to interception and eavesdropping by cybercriminals. SCM involves disabling or encrypting vulnerable protocols to protect data in transit.
SCM safeguards systems by ensuring they are properly configured (hardened) in accordance with internal and/or regulatory security and compliance standards.
What are the steps for SCM?
- Inventory: Find all devices connected to the network. Use different discovery methods to find all connected hardware, software, and assets that might be hidden from the IT department, such as remote users and shadow IT.
- Classify: Group devices by type, Identifying devices with common configurations, for example, Windows laptops and desktops, Mac laptops and desktops, Windows servers, Linux servers, Android mobile devices, network switches, network routers, etc.
- Define configurations: Find acceptable secure configurations as a basis for each type of managed device. Follow security policy guidelines from an accredited authority, such as the Center for Internet Security (CIS) or NIST.
- Assess and remediate vulnerabilities: If any deviations are found, evaluate, and remediate the configuration differences to mitigate or resolve the vulnerability. Flag any devices where any deviations couldn´t be fixed and treat them separately.
Can NinjaOne help in SCM?
NinjaOne offers several features and functionalities that can assist with SCM and contribute to a more secure IT environment.
- Patch Management:
- Automated patch deployment: NinjaOne automates the process of identifying, downloading, and deploying security patches to various endpoints, ensuring systems are kept up-to-date and vulnerabilities are addressed promptly.
- Patch reporting: It provides detailed reports on patch status, highlighting any devices that are missing critical updates, allowing IT teams to prioritize and ensure complete patching coverage.
- Configuration Management:
- Policies and automation: NinjaOne allows you to create and enforce policies that define specific configuration settings for different device groups. You can also utilize scripting capabilities to automate and centrally manage various configurations across multiple devices, ensuring consistency and adherence to security best practices.
- Pre-configured templates: The platform offers pre-built configuration templates for various security software and settings, saving time and ensuring consistency in hardening configurations.
- Remote Management and Monitoring:
- Remote access and control: NinjaOne provides secure remote access to devices, allowing IT personnel to troubleshoot configuration issues, deploy updates, and enforce security policies remotely, improving efficiency and response times.
- Real-time monitoring: The platform offers real-time monitoring of system health, security events, and configuration changes, enabling IT teams to identify potential security risks and non-compliant configurations quickly.
- Reporting and Compliance:
- Compliance reports: NinjaOne generates comprehensive reports that showcase the configuration state of devices and compliance with internal security policies or external regulations. This helps organizations demonstrate adherence to security standards and identify any areas requiring improvement.
- Integration with Third-Party Tools:
- NinjaOne integrates with various security solutions, allowing you to manage and enforce security policies from a centralized platform, streamlining workflows and improving overall security posture.
What are the advantages of using NinjaOne in the SCM process?
By leveraging NinjaOne you can help your organization:
- Reduce the risk of security vulnerabilities by ensuring systems are consistently configured according to security best practices.
- Improve efficiency and reduce manual work associated with managing security configurations across numerous devices.
- Demonstrate compliance with internal security policies and external regulations.
- Enhance overall IT security posture by providing centralized visibility and control over security configurations.
It’s important to note that NinjaOne is a tool that can facilitate Security Configuration Management, but it doesn’t replace the need for well-defined security policies, knowledgeable IT personnel, and ongoing security awareness training. And stay vigilant, Zero-Day Vulnerabilities are found every day and being vigilant is crucial in this process.
Strategy: Configure automated OS patching using policies in NinjaOne
Patching is crucial for SCM, and it´s easy to manage using NinjaOne policies.
To configure automated patching in a policy:
- Go to Administration, then policies, then Agent policies.
- Select a policy you want to use for your devices, for example, Mac (if you don´t want to modify your default policy, you can also create a new policy inherited from the original one and modify this new one).
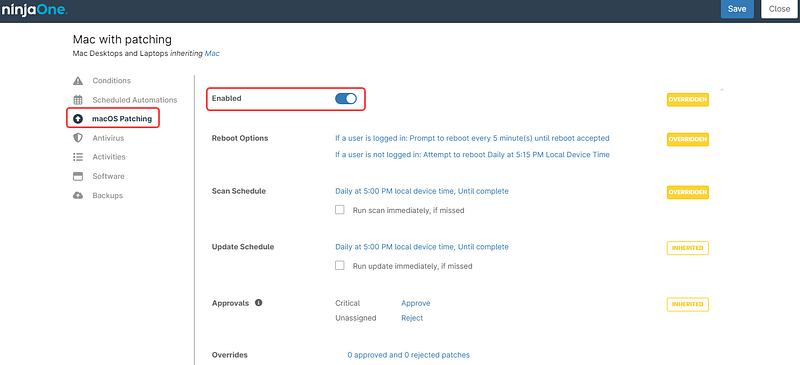
- Go to Patching, for this example, it´s macOS patching.
- Switch the button at the top of the screen to Enabled.
- Configure the rest of the fields, according to your preferences.
- Save and close (you may be asked to enter your MFA method response).
7. Within the Organization dashboard, verify that the newly enabled patching policy has been assigned to your devices.

Next Steps
Security Configuration Management FAQs
What is security configuration management (SCM)?
Security Configuration Management (SCM or SecCM) is a process that involves adjusting the default settings of an information system to enhance security and mitigate risk.
What is an example of a secure configuration?
All home routers of the same model come from the factory with the same administrator username and password, and some of them have external access enabled by default; Default credentials are available to anyone on the provider’s site. An example of a secure configuration is to change the administrator password to a strong one and make sure external access is disabled.
Why is security configuration important?
Security configuration is of paramount importance because it directly impacts the safety and integrity of an organization’s digital assets.
Ready to become an IT Ninja?