Key Points
- EDR (Endpoint Detection and Response) is a cybersecurity essential that detects, analyzes, and responds to threats that bypass traditional defenses like antivirus and firewalls.
- Core capabilities include collecting endpoint telemetry, monitoring user behavior, alerting teams, and automatically remediating threats in real time.
- Business benefits of EDR include deeper visibility, proactive compliance, improved data privacy, automated response, and reduced costs from cyberattacks.
- Top features to evaluate are integration, scalability, usability, strong detection/remediation, and secure handling of endpoint data.
- EDR’s role in cybersecurity stacks is complementary to AV/NGAV, fitting downstream of prevention tools and delivering the most value when integrated with RMM and MDM platforms.
In a crowded and competitive cybersecurity industry, vendors face the challenge of standing out among the rest. One way they do so is to claim their solution can provide “all-in-one protection” and offer features such as EDR, short for endpoint detection and response. Let’s define what this is, what it means for your cybersecurity stack, and how you can find the right solution for your team.
📕 MSP’s Hype-Free Guide to EDR
What is EDR?
Endpoint detection and response (EDR) refers to endpoint security software designed to help organizations identify, stop, and react to threats that have bypassed other defenses.
Like other endpoint security software, EDR is deployed by installing agents on endpoints and is managed via a cloud-based SaaS portal. It plays a crucial role in enforcing cybersecurity within an infrastructure managed by an IT team or MSPs, providing a critical layer of defense against evolving cyber threats. For a walkthrough on setting it up, watch our video on EDR deployment.
Note: This blog post touches on EDR at a high level, but if you’re interested in getting more details and learning how to evaluate EDR products, see our new MSP’s Hype-Free Guide to EDR. This comprehensive guide, which you can download for FREE, distills extensive research into actionable insights.
How endpoint detection and response (EDR) works
Endpoint detection and response (EDR) solutions involve multiple tools/functions that work together. The list below shows how each function works within an EDR solution.
1. Telemetry Data Collection
EDR solutions, as described by CrowdStrike, gather and store endpoint behavior data, including program activity and file access, allowing for behavior analysis and anomaly detection.
2. Endpoint Activity Monitoring
EDR systems focus on analyzing user behavior and endpoint activity, differentiating themselves from traditional security solutions like antivirus, which primarily examine files.
3. Threat Alerts
Upon detecting suspicious activity, EDR tools notify cybersecurity teams, block malicious actions, and provide solutions, thus alleviating some workload from IT teams.
4. Automated Threat Resolution
EDR systems quickly act to resolve threats or breaches, helping to minimize damage from cyber-attacks and facilitating rapid incident response for IT security teams.
What are the benefits of EDR?
Now, let’s explore the key benefits that make an effective endpoint detection and response to cybersecurity:
Improved cybersecurity and protection
EDR solutions can offer advanced threat detection and active scanning capabilities that surpass traditional antivirus software, which can overlook threats not included in their signature databases.
Deeper visibility
Endpoint detection and response allows IT teams and MSPs to have a broader overview of their managed environment, giving them more confidence in responding to threats that attempt to infiltrate.
Rapid response
EDR enables automated incident response, effectively neutralizing threats and restoring compromised resources without manual intervention.
Proactive security
EDR can assist organizations in meeting industry compliance requirements for regulations like GDPR, HIPAA, PCI DSS, etc. by providing visibility into endpoint activities and the ability to detect and respond to threats promptly.
Improvement of data privacy
Utilizing EDR solutions helps guarantee data privacy and protection by preventing unauthorized access to an organization’s sensitive information.
Cost saving
Lastly, employing an endpoint detection and response tool helps save companies from destructive and costly data loss caused by cyberattacks by enabling faster incident response and minimizing downtime.
How do EDR tools empower organizations?
At a high level, EDR solutions gather data from endpoints, use it to identify potential cybersecurity threats and provide helpful ways of investigating and reacting to those potential risks.

Historically, these capabilities were largely confined to big enterprise companies that could afford teams of experienced security analysts operating outside a security operations center (SOC). Sorting through troves of data, identifying suspicious activity, and understanding how to quickly react to incidents took considerable time, effort, and expertise.
To make these capabilities more accessible, cybersecurity vendors have worked on introducing less complex EDR offerings that are centered more around streamlined workflows and automation. These “EDR Lite” solutions aim to lower the entry and bring EDR capabilities to a segment of the market that sorely needs them: SMBs.
Now that we’ve discussed EDR tools and why they’re crucial for modern security, let’s explore the essential features of an effective endpoint detection and response solution.
5 key features of an endpoint detection and response solution
When faced with so many providers in the market, you and your IT team can ease your search by remembering these five key features in an endpoint detection and response tool.
1. Integration
An EDR should smoothly integrate with your IT team’s current system and other applications and tools. IT teams and MSPs should also consider utilizing a complete endpoint management tool that integrates with an efficient EDR solution for a holistic approach to endpoint protection.
2. Detection and remediation
An efficient EDR system should be able to remediate threats quickly and notify a security team ASAP. Choose an EDR solution with very strong threat detection and remediation abilities.
3. Usability
Select an EDR solution that is intuitive and easy for your team to use. Some solutions offer a centralized management console on a single pane of glass, which helps users gain even more visibility into their network security.
4. Scalability
As your organization and IT team grow, you’ll need a solution that grows with you and smoothly adapts to changes. Take a look at the scalability options of EDR solutions before making any final decisions.
5. Security
Since endpoint detection and response solutions collect and analyze data, you’ll want to check their security measures. This is to help ensure that your data remains safe and is handled responsibly.
NinjaOne endpoint detection and response integrations
NinjaOne provides remote monitoring and management (RMM) software that helps IT teams and MSPs manage their endpoints. Some popular endpoint detection and response tools that integrate with NinjaOne include:
Bitdefender
Bitdefender offers a cloud-based endpoint detection and response solution that uses real-time monitoring, data collection, threat detection, analysis tools, and automated response actions to provide organizations with advanced endpoint security and protection.
Malwarebytes
Malwarebytes endpoint detection and response is an effective EDR tool that offers attack isolation, auto-remediation, threat detection, ransomware rollback, and protection against advanced zero-day threats.
SentinelOne
SentinelOne provides an endpoint detection and response tool known for its ability to proactively hunt and detect threats, report endpoint telemetry data, remediate attacks, analyze data, and customize to a specific IT environment.
Crowdstrike
CrowdStrike is a leading cloud-based endpoint protection company that NinjaOne integrates with for endpoint detection and response. The platform is known for its rapid response and prevention capabilities. The company also offers additional security solutions such as threat intelligence, incident response, and IT hygiene to provide a comprehensive approach to cybersecurity.
Where does EDR fit in a modern cybersecurity stack?
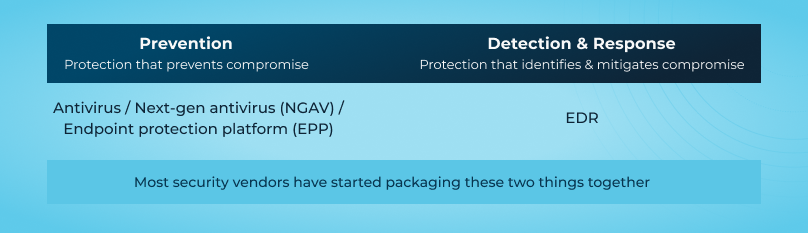
As a capability, EDR sits downstream from prevention-focused security solutions. Its primary purpose is to enable detection and response to threats once they have bypassed other defenses like firewalls and antivirus (AV).
That said, EDR functionality is rarely sold on its own anymore. Instead, it’s often packaged together with prevention-focused technologies like new-generation antivirus (NGAV) to provide more unified endpoint security. So while “EDR” refers to a clearly defined set of capabilities, the lines separating EDR tools and other endpoint security tools have gotten incredibly blurry.
As Gartner puts it in its Competitive Landscape: Endpoint Protection Platforms, Worldwide, 2019 report:
“On the marketing front, many of the providers in the [endpoint security] market now look drastically similar to each other, touting machine learning and behavior-based analysis concepts — making it harder for organizations to make informed product decisions. Gartner believes that this is causing some confusion in the market.”
📕 MSP’s Hype-Free Guide to EDR
The merging of AV/NGAV products with EDR tools has led to confusion, with many believing EDRs serve as superior AVs. However, EDRs are not primarily designed to prevent attacks; rather, they alert users to breaches and facilitate response efforts. Vendors often do not clarify this distinction, complicating the evaluation of EDR solutions.
To help we’ve put together a new guide that breaks everything down in clear, straightforward terms.
Additionally, the integration of EDR with remote monitoring and management (RMM) and mobile device management (MDM) tools enhances threat visibility and response, enabling IT teams to detect and manage threats across various endpoints efficiently.
This integration fosters a unified cybersecurity strategy that combines prevention, detection, and management.
Want more facts about EDR and tips for evaluating solutions?
Download your free 26-page MSP’s Hype-Free Guide to EDR. It addresses all your EDR questions, ensuring you’re prepared for inquiries from customers, bosses, or prospects.
Prefer a visual walkthrough of ‘What is EDR? A Cybersecurity Essential‘ Check out this quick video.