For a time, the discussion on cybersecurity has centered around the story of a cyber attack chain in motion, leading to big-name victims, alleged state-sponsored threat actors, sophisticated tradecrafts, and threats to national security, not to mention potentially massive ramifications on U.S. cyber policy and regulations.
Plus, it keeps getting bigger!
But while our news feeds continue to be flooded with updates and organizations continue to ponder how they would deal with a similar attack, “bread-and-butter” cybercrime keeps quietly chugging right along. Every day, standard malspam campaigns snag hordes of new victims. Ransomware may be in the unfamiliar position of no longer being the “it” threat, but it continues to pad criminals’ wallets with fresh Bitcoin.
As former Director of the U.S. Cybersecurity and Infrastructure Security Agency Chris Krebs and Red Canary Director of Threat Intelligence Katie Nickels both point out, there’s a tendency to “fetish-ize” state-sponsored actors and overlook the “boring criminal” stuff.
That “boring criminal” stuff is the majority of threat activity that MSPs and their clients are going to face, and despite years of stack and awareness building, many attacks continue to find their way through defenses. Worse, they’re only becoming more damaging and more costly.
According to ransomware incident response provider Coveware, the average ransom payment jumped to $233,817 during Q3 last year, an increase of 31% from Q2. The average length of time victims grappled with downtime caused by ransomware incidents also increased to 19 days.
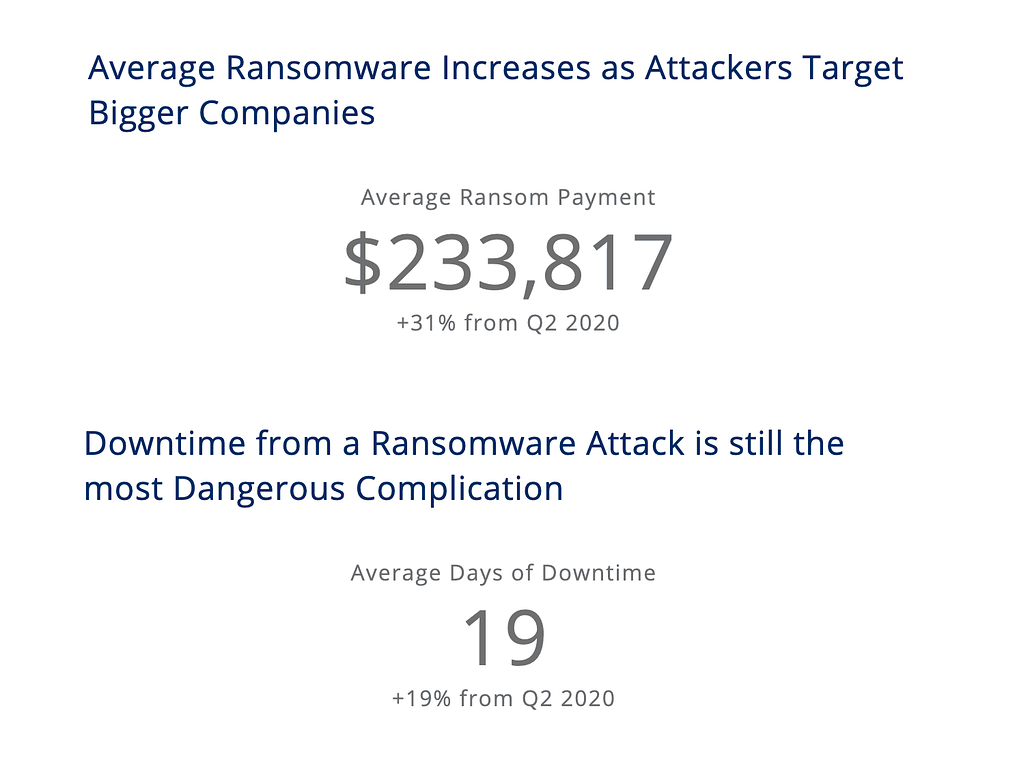
Source: Coveware Q3 Ransomware Report
In a slightly newer but also growing development, Coveware also reported that 50% of the ransomware incidents they dealt with in Q3 2020 included threats to publicly release exfiltrated data.
With the stakes continuing to climb, it’s important for MSPs to step back and consider their capabilities, not just in terms of blocking malicious executables, but for spotting, blocking, and reacting to malicious tip-offs earlier in the attack chain.
What is a cyber attack chain?
Before we can discuss more on how to deal with the cyber attack chain, we first need to understand how it functions.
Developed by Lockheed and Martin, the cyber kill chain is a systematic framework that outlines the steps cybercriminals take when they carry out cyberattacks on organizations. Understanding the Cyber Kill Chain framework helps organizations develop robust security measures at every stage of an attack.
Improving defenses by mapping tools to cyber attack chains
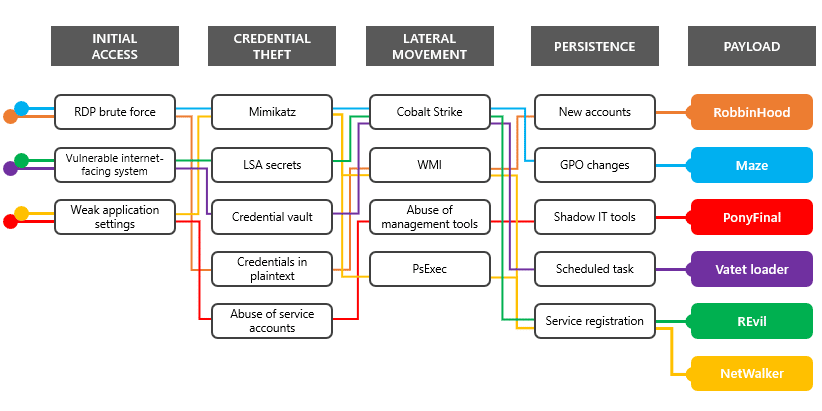
Let’s look at a diagram that the Microsoft 365 Defender Intelligence Team put together in late April 2020. This graphic does a good job of providing a high level overview of what researchers consider to be hallmark post-compromise activities — credential theft, lateral movement, and persistence — bookended by the parts many non-security experts focus on most — initial access and payload execution.
Source: Microsoft 365 Defender Intelligence Team
This diagram also does a nice job of showing just how similar these overall attack patterns are. Attackers first establish a foothold, then often turn their focus to extending their reach deeper into an organization, disabling backups and defenses, and properly setting the stage to ensure that when they (or another actor they sell access to) deploy the ransomware payload it has the maximum impact and leaves victims with as few options as possible.
Breaking down attack chains in this way may make some readers think of the MITRE ATT&CK framework, which is far more in-depth and covers a much larger range of attack tactics and techniques.
How to utilize cyber attack chain tools to bolster your cybersecurity
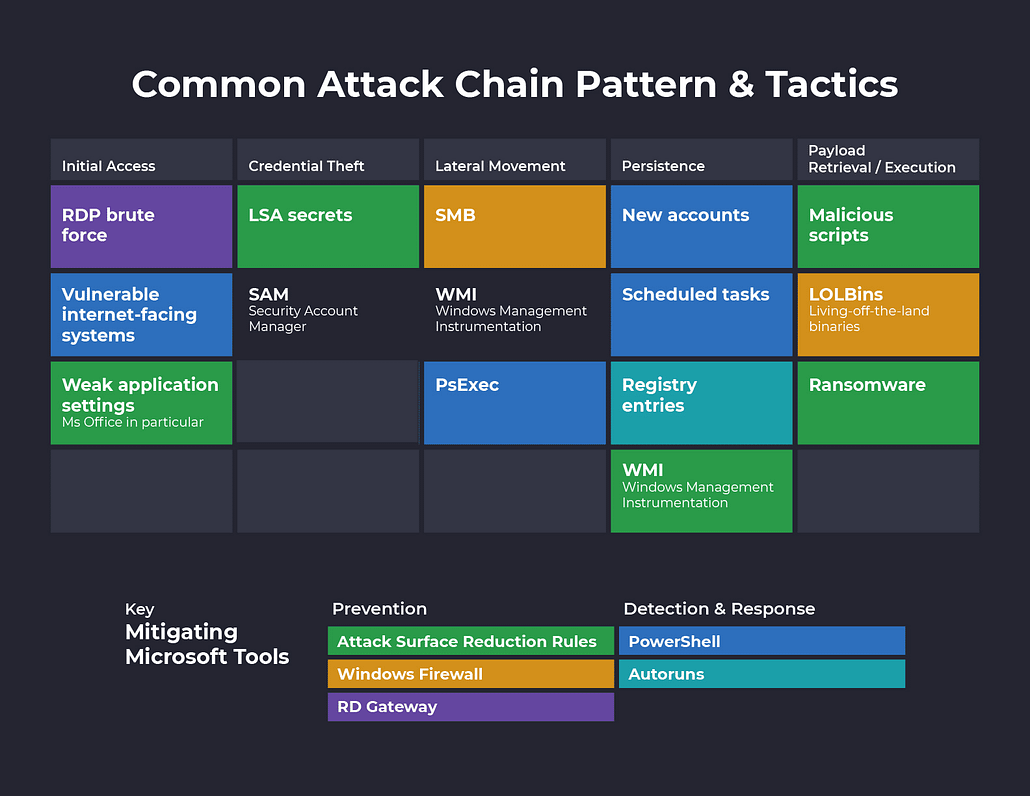
I actually like this simplified approach as the ATT&CK matrix has gotten fairly byzantine, and I thought I’d take my own whack at creating an approachable attack chain diagram. Only I decided to take it in a slightly different direction and illustrate how, by using five Microsoft tools you already have access to, you can actually block or at least monitor for a large share of the most common ransomware attack tactics. Those five tools are:
- Attack Surface Reduction (ASR) Rules
- Autoruns
- PowerShell
- RD Gateway
- Windows Firewall
In addition to avoiding third-party security costs with these tools, there’s the added benefit that the majority of the mitigations we’ll cover below can be centrally deployed and/or configured via your RMM or Intune.
Obvious disclaimer: This list is not meant to be considered comprehensive by any stretch of the imagination. It’s really meant to present some basic information in a slightly new way that gets MSPs thinking. Hopefully, it can help you identify additional, relatively easy wins for improving your and your clients’ security postures by making life for attackers a little more difficult.
Let’s dive deeper into this diagram and explain how each tool can provide you with opportunities to either identify suspicious behavior or break the attack chain altogether.
Tool #1: RD Gateway
Tactic mitigated:
- Initial access: RDP brute force
Everyone rolls their eyes and says of course they know they shouldn’t have Remote Desktop Protocol (RDP) exposed to the Internet. Yet more than half of the ransomware victims Coveware worked with in Q3 2020 were initially compromised thanks to improperly secured RDP.
You can apply knowledge of cyber attack chains and compromise by configuring a RD Gateway and by following additional steps, including enabling MFA, outlined here.
If you’re absolutely 100% sure you don’t have a server out there somewhere with RDP exposed, well, you can check again with one of the following PowerShell scripts from Cyberdrain author Kelvin Tegelaar. This one helps you conduct port scans, and this one helps you conduct Shodan scans (though it does require you to sign up for a paid Shodan account).
Tool #2: Attack Surface Reduction (ASR) rules
Tactics mitigated:
- Initial access: Weak application settings (Microsoft Office, Adobe, email client)
- Credential theft: Stealing credentials from lsass.exe
- Lateral movement: WMI and PsExec abuse
- Persistence: WMI event subscription abuse
- Payload retrieval / execution: Malicious scripts, ransomware
I won’t lie. I’m fairly obsessed with Microsoft’s Attack Surface Reduction (ASR) rules. As you can see from this list, they provide a nice amount of cover, addressing tactics across multiple attack stages. Microsoft acknowledges they created ASR rules to mitigate some of the most commonly attacked areas they see, and provide protection for organizations that rely on powerful — but also highly abused — features and programs like Office macros, WMI, PsExec, and more.
Requirements for ASR rules include:
- Windows 10, versions 1709 and later
- Microsoft Defender must be active (not in passive mode)
- Some rules require cloud-delivered protection to be enabled
The catch with ASR rules is Microsoft has gated full ASR features behind enterprise licenses (E5 if you want the full complement of Defender for Endpoint integration plus enhanced monitoring, alerting, and reporting visibility). That said, the company has documented that you CAN utilize ASR rules with a Microsoft 365 Business license — it’s just not officially supported. So where there’s a will, there’s a way.
The other concern I’ve heard discussed regarding ASR rules is the potential for false positives and noisy alerts. The internal security team at Palantir has put together an extremely helpful post detailing their experiences with each of the 15 available ASR rules, including recommendations for which rules can be safely configured in Block Mode and which are best left in Audit Mode or disabled altogether depending on your environments.
ASR rules for blocking Microsoft Office abuse:
- Block Office applications from creating executable content (Block Mode recommended*)
- Note: May interfere with Microsoft Office Smart Lookup feature.
- Block Win32 API calls from Office macros (Audit Mode suggested first*)
- Block Office applications from injecting code into other processes (Audit Mode suggested first*)
- Block all Office applications from creating child processes (Audit Mode suggested first*)
ASR rules for blocking additional malware and application abuse:
- Block Adobe Reader from creating child processes (Block Mode recommended*)
- Note: Will interfere with Adobe update process unless that is managed by a central software patching service.
- Block executable content from email client and webmail (Block Mode recommended*)
- Block untrusted and unsigned processes that run from USB (Block Mode recommended*)
ASR rules for blocking malicious scripts:
- Block JavaScript or VBScript from launching downloaded executable content (Block Mode recommended*)
- Block execution of potentially obfuscated scripts (Block Mode recommended with the exception of developer machines*)
ASR rules for blocking post-exploitation activities:
- Block credential stealing from lsass.exe (Block Mode recommended*)
- Block process creations originating from PsExec and WMI commands (Not compatible if using SCCM*)
- Block persistence through WMI event subscription (Block Mode recommended*)
* Recommendations from the security firm Palantir based on their internal use and research.
Tool #3: Windows Firewall
Tactics mitigated:
- Lateral movement: SMB-based
- Payload retrieval / execution: LOLbins making outbound connections
Windows Firewall is an underutilized tool for dealing with cyber attack chains that can make a great addition to any organization’s defense-in-depth layers. As Palantir CISO Dan Stuckey explains, not only is it present by default, it’s “one of the easiest ways to limit remote access to many commonly abused services.”
One of the biggest opportunities it provides defenders is the capability to isolate compromises by restricting attacker’s ability to leverage SMB-based lateral movement. To understand why attackers love to use Windows Server Message Block (SMB) protocol for lateral movement, see this post. It provides a concise overview and highlights how it can be used to bypass MFA.
The post also explains in detail the controls that the Palantir security team has found effective in restricting SMB-based lateral movement, including implementing a simple tiered administration model and using a simple Windows Firewall rule distributed via GPO that denies all inbound communication on ports 139 and 445. They also recommend denying inbound WinRM and RDP to workstations and not allowing them to use LLMNR, Netbios, or mDNS outbound (see link above plus more details here).
Tool #4: PowerShell
Tactics monitored:
- Initial access: Exposed RDP and vulnerable Internet-facing systems
- Lateral movement: PsExec abuse
- Persistence: New accounts, scheduled tasks, WMI event subscription
The use cases we’ve discussed for the previous three cyber attack chain tools have centered around prevention — denying or restricting initial access and blocking malicious activities. With this and the next tool, we’re shifting the focus to detection and response.
Many MSPs are already actively using PowerShell to automate a host of remote management activities, but thanks to the work of scripting experts like Cyberdrain author Kelvin Tegelaar, more and more MSPs are utilizing PowerShell to build out their monitoring capabilities, as well.
You obviously want to know about signs of trouble on your client networks before ransomware gets deployed. The following scripts from Kelvin can help you identify gaps in security as well as a variety of suspicious activity to investigate:
PowerShell scripts for identifying exposed and at-risk systems:
- Conduct external port scans (100% you don’t have a server somewhere out there with RDP exposed? Check again.)
- Alert on Shodan results (does require paid Shodan account)
PowerShell scripts for identifying potential lateral movement, persistence, and ransomware activity:
- Create alerts based on PsExec usage (PsExec is another legitimate administrative tool that attackers use for remote command execution)
- Monitor new account creation (created domain and local users, users added to privileged groups, etc.)
- Monitor for scheduled task creation
- Create and monitor canary files
Kelvin regularly updates the Cyberdrain blog with new scripts, so be sure to check it out.
Tool #5: Autoruns
Tactics monitored:
- Persistence: Registry entries
One of the most common ways of achieving persistence is by planting malicious scripts in the Windows registry designed to run at reboot or when a shortcut or batch files are triggered.
Microsoft Autoruns is the go-to tool for showing you what programs are configured to run during bootup or login. This article walks through how to set it up and use it to inspect and identify suspicious registry keys. It even offers several examples of suspicious entries to look out for.
It’s all about adding layers to your security and giving yourself more at-bats to respond
These five tools won’t eliminate the risk of ransomware, but they will certainly help you plug gaps in your defenses and make things more difficult for attackers by taking away easy routines and low-hanging fruit.
You know what they say — it’s not not a matter of if you’re going to deal with an attack, but when. Well, it’s also a matter of when it happens, how much it’s going to hurt. Using these tools and other best practices to harden your systems and put more alerting opportunities in place can help you spot and disrupt inevitable attacks sooner, before they have the chance to trigger a real crisis.
→ Protect your organization from cyber attack chains by keeping software up-to-date with NinjaOne Patch Management.
Frequently Asked Questions (FAQs)
What are the 7 stages of the cyber kill chain?
1. Reconnaissance
This is the first phase of the Cyber Kill Chain and is sometimes known as the observation phase. The attackers begin by identifying a target and gathering information. This may involve researching the organization’s public websites, social media profiles, and other publicly available data to identify potential vulnerabilities. They might also engage in activities like network scanning and email harvesting.
2. Weaponization
Once the attackers have all the information on a target and their vulnerabilities, they begin the second stage of the cyber kill chain. Attackers usually develop or modify cyber kill chain tools. This could be malware that targets any discovered vulnerabilities, exploits a known software vulnerability, or creates a phishing email with an infected attachment.
3. Delivery
The next stage of the cyber kill chain involves attackers ensuring their malware reaches their target. The cyber kill chain tool can be delivered through emails, malicious websites, USB drives, and other vectors. The goal is to get the target to activate the malware, often through social engineering techniques.
4. Exploitation
In this step of the Cyber Kill Chain, the malware exploits a vulnerability in the targeted IT environment to execute its plan. This could involve exploiting unpatched systems or weak passwords to gain initial access to the target’s environment.
5. Installation
In this stage, the malware installs itself on the targeted system and allows the attackers open access to the infiltrated system.
6. Command and Control
Known also as the C2 stage, this stage involves the malware establishing a command-and-control channel. This channel allows the attacker to remotely send instructions to the malware, allowing them to achieve their original objectives
7. Actions on Objectives
In the final phase of the cyber kill chain, attackers achieve their ultimate goals, whether it’s the theft of sensitive data, destruction, or encryption for ransom with ransomware. The specific objectives will vary based on the attacker’s intent, whether stealing intellectual property, disrupting services, or causing financial damage.
What is a cyber attack path?
An attack path is vital for helping IT and cybersecurity experts determine how to prioritize fixing vulnerabilities in cloud-native IT environments. An attack path is defined as a visual representation of the path attackers utilize to exploit vulnerabilities and infiltrate systems.
What is the difference between a cyber attack chain and a cyber kill chain?
The cyber attack chain is simply another name for the cyber kill chain. Lockheed and Martin developed this framework from a military model to help organizations better understand how cyber attacks occur and how to overcome them.
The MITRE ATT&CK framework aids IT professionals in understanding the steps of a cyberattack at a high level. It does not follow a specific, linear order like a cyber attack chain. Instead, it focuses on a more granular approach. The MITRE ATT&CK studies the techniques cybercriminals use for their attacks to help cybersecurity professionals detect and mitigate them.