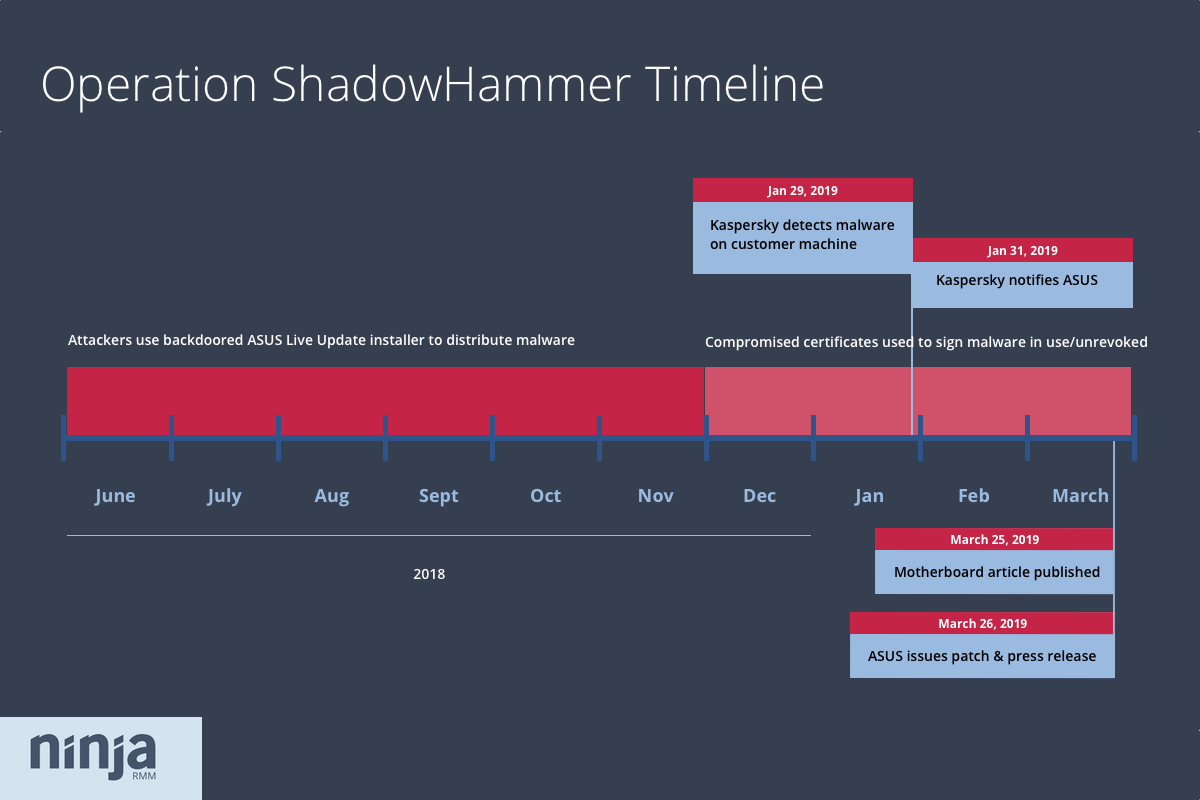
On Monday, Kim Zetter at Motherboard broke the news that attackers had hijacked the software update tool for ASUS, one of the largest computer makers in the world. Researchers estimate the tool was used to install backdoors on hundreds of thousands of machines between June and November 2018. Here’s what you and your clients need to know.
What happened? Quick facts:
- Attackers compromised the ASUS Live Update Utility, which comes pre-installed on ASUS notebooks and automatically installs firmware and software updates.
- They used compromised versions of Live Update to deliver malware to ASUS notebooks from June 2018 to November 2018. Versions of Live Update confirmed to be vulnerable include 3.5.9, 3.6.0, 3.6.2, and 3.6.5. During that time legitimate updates continued to be sent out, too, however, so not every user was infected.
- The malware masqueraded as an update to the update tool, and was signed with one of two legitimate ASUS certificates. As a result, the malware was able to evade detection by signaling to users and security programs it was a trusted file.
- Once installed, the malware checked victim MAC addresses to see if it had landed on one of at least 600 specific targets. If confirmed, it called out to a site disguised as a legitimate ASUS site (asushotfix[dot]com) and downloaded a second-stage payload. Otherwise, all victims were left with the initial backdoor installed.
- Researchers at antivirus company Kaspersky believe the attack’s surgical targeting, along with other indicators, suggest it is the work of a sophisticated threat actor. They have officially dubbed the attack “Operation ShadowHammer,” and suggest it may be linked to previous supply chain attacks, including the 2017 CCleaner supply chain attack that infected 2.3 million users worldwide.
- After initially denying the compromise, ASUS has issued a statement confirming a “small number of devices have been implanted with malicious code.” The company says the latest version of Live Update (3.6.8) is secure, though there have been reports of difficulty updating to that version, and it does not appear to be currently available for manual download from the ASUS website (despite ASUS indicating the contrary). In addition, the certificate used to sign the malware has not yet been revoked.
Why is this a big deal?
1) Exposure to this malware was massive
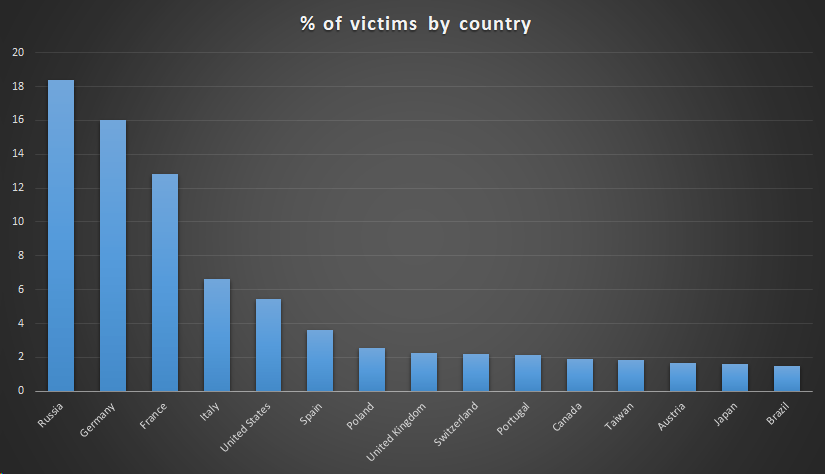
ASUS is the world’s fifth-largest PC vendor, accounting for six percent of the PC market. The reach of this supply chain attack — carried out for at least five months — was extensive. Kaspersky found the malicious updater installed on 5customer-count of its own customers, but researchers at the company estimate the total number of infected machines outside their customer base could potentially exceed one million.
Kaspersky customers infected by ShadowHammer, by country. Source: Kaspersky
Security firm Symantec confirmed Kaspersky findings with Zetter, and reported at least 13,000 of its own customers had also been infected by the malware.
2) The malware was able to slip past defenses undetected
Supply chain attacks like this one are difficult to defend against. In this case, attackers were able to wrap their malware in several layers of legitimacy:
- The malware was installed via ASUS’s trusted update application
- Attackers constructed the malware by injecting malicious code into a legitimate ASUS update file from 2015
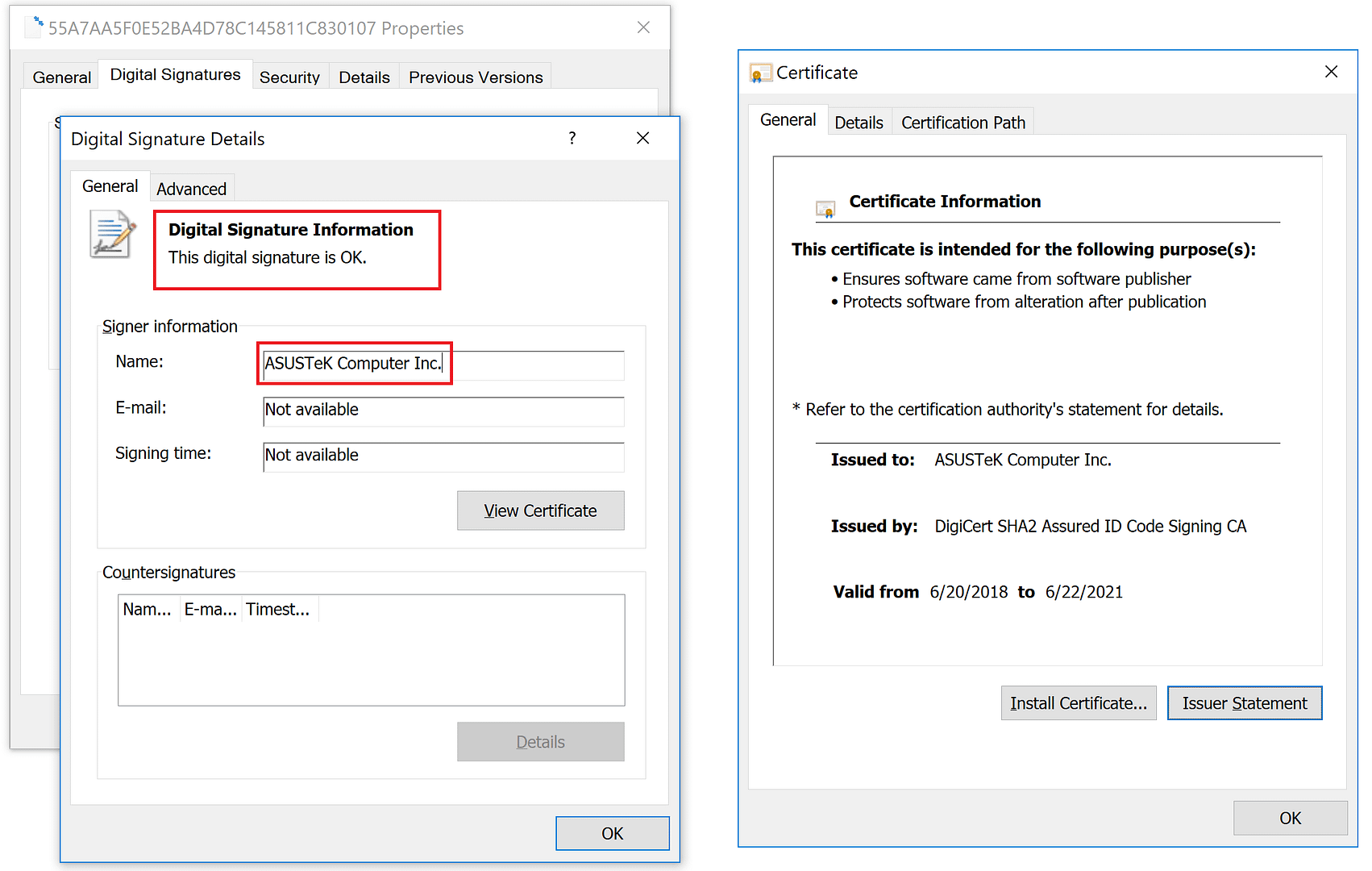
- The malware was digitally signed with a legitimate ASUS certificate (serial number 05e6a0be5ac359c7ff11f4b467ab20fc)
The ASUS certificate attackers used to sign malicious ASUS Live Update installer files. Source: Kaspersky
As a result, it was able to convincingly pass as an authentic update, tricking security programs and even users who were savvy enough to upload the files to VirusTotal, which reported them clean.
3) With backdoors installed, victims are vulnerable to a variety of threats
While only a small pre-determined list of MAC addresses were targeted to receive the second-stage payload, all of victims who received the malicious update installer between June and November 2018 still have malware on their systems.
The good news is the command-and-control server that delivered the second-stage payload was shut down in November, but until we know more about the malware’s capabilities victims have to assume there is some amount of risk even if they weren’t one of the ~600 targeted MAC addresses.
Researcher Vitali Kremez suggests that, in those cases, wiping machines may be overkill, but MSPs and admins should ensure ASUS Live Update has been updated to the latest version (3.6.8) and monitor affected machines more closely.
The residual risk is low but present; I highly recommend checking the MAC addresses on https://t.co/P4j0jKwsx3 against the list of ~600 targeted MAC addresses & updating the Live Update. Enhanced monitoring of the ASUS machine is recommended for the time rather than full wipeout.
— Vitali Kremez (@VK_Intel) March 27, 2019
How can you determine if you or your clients are affected?
In short
- Rule out the possibility machines were targeted to receive the second-stage payload by using Kaspsersky’s tool here
- Check for the presence of the IOC hashes here
- Check for presence of the file “.idx.ini”
More details
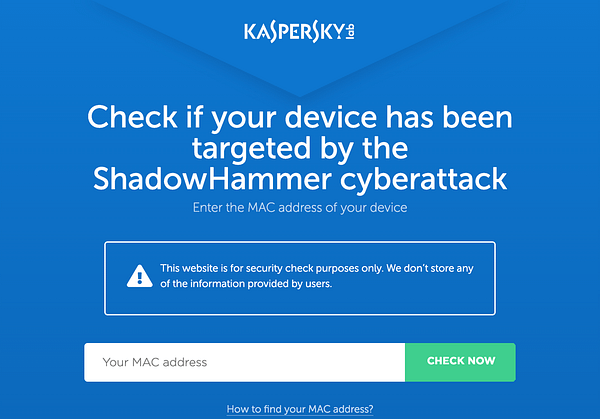
Kaspersky has an online tool you can use to determine if your MAC address is one of the 600 that the attackers were targeting for second-stage payload delivery.
Note: If your MAC address does show up as a match it’s not reason to panic just yet. Researchers point out a small number of the MACs may be providing false alarms.
Apparently, one of the MACs targeted by #ShadowHammer is used on thousands of hosts: it is VMware VMNet8 adapter with default MAC 00:50:56:C0:00:08. If you got one of those – don’t freak out. You were probably just a collateral target. Check if you ran ASUS Live Updater in 2018.
— Vitaly Kamluk (@vkamluk) March 26, 2019
Unfortunately, what the Kaspersky tool doesn’t tell you is whether you had a backdoored version of Live Update installed. Although they do provide a small number of hashes and other indicators of compromise (IOCs) here.
ASUS has also made a “security diagnostic tool” available, but it is unclear whether it simply checks your MAC address or helps you identify the other signs of infection. If you’re feeling brave enough to download the program (ASUS did just suffer a supply chain attack, after all), you may have difficulties running it, however.
So if you try to download the diagnostic tool from @ASUS https://t.co/nlquvdvKbY
… Ok maybe i’ll run it another time. pic.twitter.com/W1cnFP4oBX— Giuseppe `N3mes1s` (@gN3mes1s) March 26, 2019
Womp. womp.
UPDATE 3/27/19: Thanks to analysis from researcher Vitali Kremez, we now have an additional IOC. If the victim’s MAC address does NOT match with an address on the hardcoded list then the malware creates a file called .idx.ini in the user directory. The purpose of the file is unclear, but its presence is an indication that the machine was in fact infected with a backdoored version of ASUS Live Update, but no second-stage payload was delivered.
What else can you do now to protect yourself and your clients?
- If you have ASUS notebooks in your environments, make sure the latest version of Live Update (3.6.8) is installed. Warning: If you go to the ASUS support site to download the update directly take note that ASUS is still pointing to older versions of Live Update.
ASUS is still providing old versions of ASUS Live Update on their support pages which are below their recommended version to resolve security concerns. https://t.co/LKkrPwQO3L
– IT Departments: beware of these downloads
– Researchers: these might be useful #ShadowHammer samples pic.twitter.com/RRcUD1zLDU— Kyle Hanslovan (@KyleHanslovan) March 26, 2019
- Monitor for / block the hash IOCs provided by Kaspersky and Florian Roth.
- Monitor any potentially affected machines more closely in general using your RMM software.
- Make sure you’re backing up your systems, your security software is up-to-date, and you’re taking practical steps to harden your systems and reduce your attack surface (we’ve got a new checklist that can help).
We’ll be following this story closely. For updates on it and other security issues affecting MSPs and clients subscribe to our blog.
In the meantime, you can download our 2019 MSP Cybersecurity Checklist here.