Our reliance on technology has made system security essential. Today’s cyber threats are more advanced than ever, surpassing traditional defenses like firewalls and antivirus software. In 2023, over 90% of successful cyberattacks involved the exploitation of unpatched software vulnerabilities.
Patch management is a vital defense mechanism for these types of threats. However, ensuring every device in an organization is updated poses challenges, especially ones with intermittent connectivity, from ensuring compatibility to managing potential conflicts. The solution? A mix of strategies focusing on automation, rigorous testing, and ongoing monitoring. Executing patch management at scale can be a daunting task, but here is a comprehensive guide that will help you do it effectively.
10 steps to execute patch management at scale
- Asset discovery and visibility
Understanding your network’s full scope is crucial before patching. Asset discovery tools efficiently catalog all items within your digital infrastructure. This inventory isn’t just a list; it’s a security measure. Knowing every device and piece of software ensures you have a complete inventory of what may need patches, preventing vulnerabilities and oversights. - Standardize and segment
By categorizing devices, such as separating servers from workstations, patching becomes more streamlined and targeted. Standardizing OS builds and software versions further simplifies this process. Uniform configurations allow IT teams to confidently deploy patches, avoiding compatibility issues and ensuring seamless integration. - Regular monitoring & automated scanning
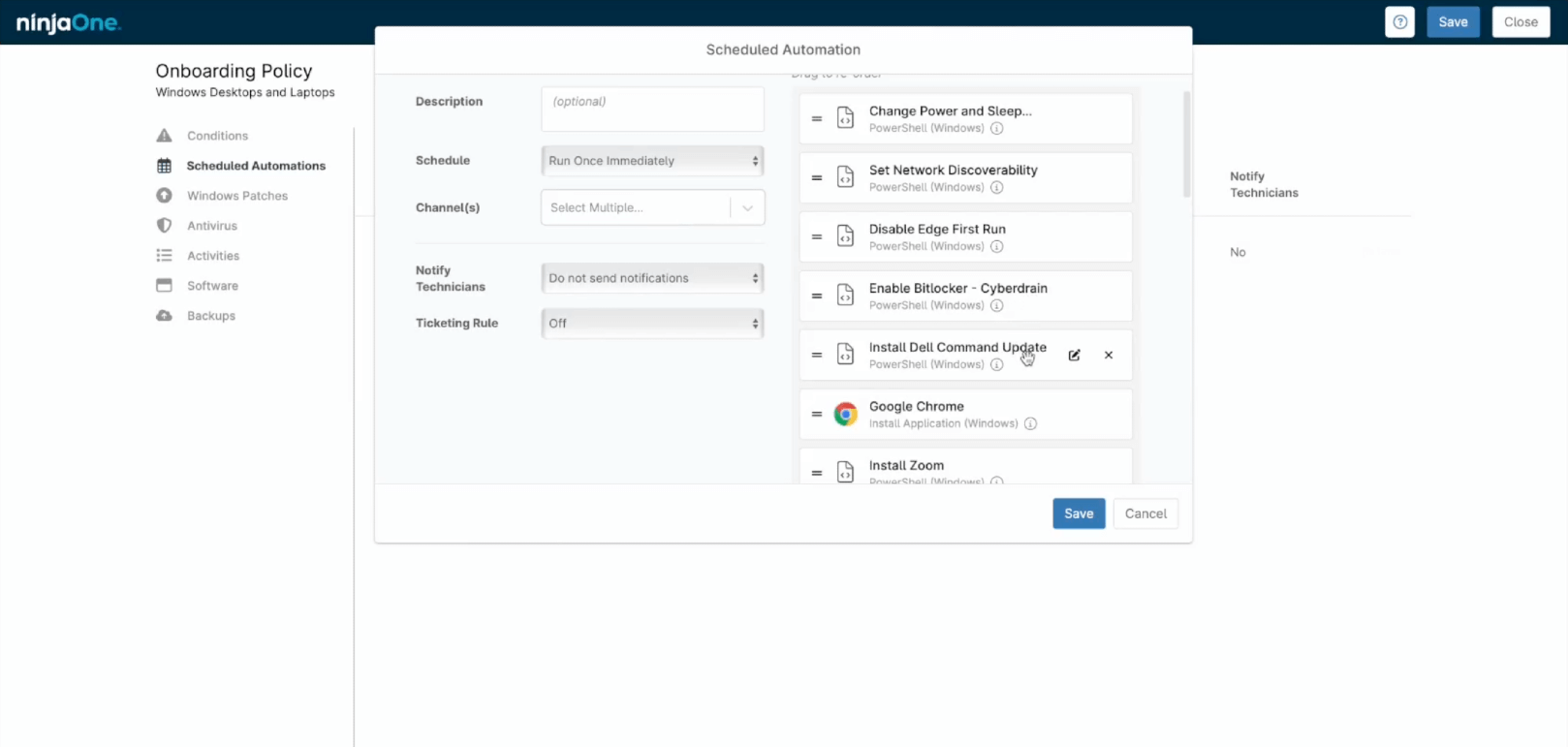
Regularly scanning for available patches is crucial in today’s digital landscape. Automated tools, like NinjaOne, eliminate the need for manual checks, which can be both tedious and fallible. Such tools continuously scan and identify necessary patches so teams can prioritize patching work based on the criticality of the update, ensuring systems are always updated with the latest security enhancements. By automating patch deployment, organizations strengthen their defenses against evolving cyber threats.Learn how healthcare companies like the Cancer & Hermatology Centers of Western Michigan stay HIPAA compliant and secure through automated patch management.
- Testing before deployment
Always test patches before full deployment. Patches can impact system stability and security, so it’s crucial to avoid hasty implementations. Deploying without testing can cause system issues or downtimes. By evaluating patches in a controlled environment first, IT teams can identify potential problems and ensure system integrity. This process confirms the patch’s effectiveness and prevents introducing new vulnerabilities.
- Scheduled rollouts
Schedule patch rollouts during off-peak hours to minimize disruptions. While most updates can coincide with regular maintenance windows, urgent security patches should be deployed automatically. By prioritizing updates via policy and optimizing deployment timing, you can maintain both system performance and security effectively. - Reboot management
Certain patches require system reboots to take full effect. It’s essential to have a well-structured strategy for managing these reboots, particularly when they involve mission-critical systems. By planning ahead and communicating potential downtimes, you can minimize disruptions and ensure smooth patch integrations.
- Continuous review and reporting
Consistently evaluate your patching procedures. Create detailed reports to confirm the successful application of patches and pinpoint any overlooked assets. This thorough review documentation not only ensures system security but also refines the overall patching strategy. - Stay informed
Stay ahead of threats by subscribing to vendor notifications and industry advisories. Receive real-time updates on vulnerabilities and patch solutions so you can proactively address potential risks. Instead of responding after issues arise, take swift, informed action to maintain system security. Being informed isn’t just about intake; it’s an active defense strategy for your digital assets. - Backup regularly
Before initiating any patch deployments, especially large-scale ones, it’s crucial to have updated backups of your systems. These backups serve as a safety net, protecting your data and configurations from unforeseen issues during patching. If complications arise, you can swiftly revert to a prior state, ensuring minimal downtime and consistent operations. Essentially, while patching enhances security, backups prevent unintentional disruptions or data loss. - Educate and train your team
By equipping your IT team with comprehensive patch management training and sharp patching tools, you ensure they have the knowledge and methodologies needed to handle various challenges. Through consistent training sessions, technicians remain updated with the latest best practices, not only enhancing efficiency but positioning your team at the forefront of industry innovations.
How NinjaOne can help
Effective patch management requires the right tools and processes, ensuring organizations adapt to new challenges and integrate feedback. Following the outlined steps, organizations improve their defense against security breaches, maintain system performance, and cope with evolving cyber threats. In the ever-evolving digital world, these actions bolster cybersecurity resilience and proactivity. Check out our webinar on all the tips and tricks for evaluating your organization’s patching readiness and how to assess potential solutions.