NinjaOne Network Restrictions for Secure and Controlled Connectivity
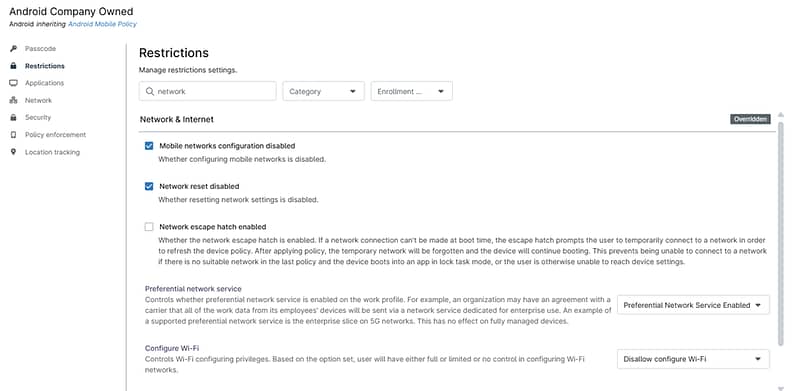
Managing network access is essential for maintaining security, optimizing performance, and preventing unauthorized changes to device configurations. Without proper controls, users may alter critical settings, connect to untrusted networks, or bypass security measures, increasing the risk of data breaches.
NinjaOne simplifies network administration by allowing IT teams to restrict network settings based on business policies, ensuring devices remain compliant and protected.
NinjaOne simplifies network administration by allowing IT teams to restrict network settings based on business policies, ensuring devices remain compliant and protected.