Audit Logging for Tech Professionals: Strengthen IT Oversight
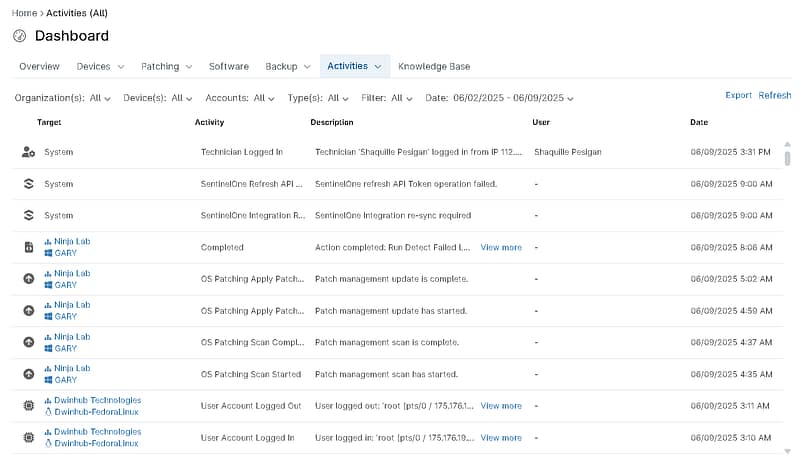
NinjaOne provides built-in audit logging features that give IT teams greater visibility and control over their environment. By tracking user activity, system changes, and device interactions, these comprehensive logs offer a clear and searchable audit trail to support security, compliance, and operational oversight.
Through NinjaOne’s intuitive web interface, IT professionals can view, filter, and analyze log data to investigate anomalies, monitor actions, and maintain transparency across endpoints and configurations.
Whether managing policy changes, addressing incidents, or supporting audits, NinjaOne’s integrated audit logging delivers the insights needed to respond confidently. With real-time access and detailed logging capabilities, NinjaOne enhances clarity and accountability within your IT operations.
NinjaOne’s Audit Logging: Enabling IT Professionals with Transparent, Accountable Oversight
End-to-End Activity Visibility
Secure and Intuitive Audit Web Interface
Compliance-Ready Logging
Real-Time Monitoring and Historical Insight
Scalable Oversight for Modern IT
Comprehensive IT Oversight with NinjaOne’s Audit Logging Capabilities
Detailed Audit Logs for Full Visibility
Intuitive Audit Web Interface
Real-Time and Historical Logging
Searchable and Filterable Audit Trails
Compliance-Ready Recordkeeping
Scalable Logging for Complex Environments
Enhancing IT Accountability and Security with NinjaOne’s Audit Logging Capabilities
Centralized Audit Trails for Security and Compliance
Real-Time Monitoring and Incident Response
Streamlining Internal Audits and Investigations
Improving Team Accountability and Policy Enforcement
By logging all administrative actions within the system, NinjaOne helps reinforce team accountability and policy adherence. Whether managing an internal IT department or an MSP environment, audit logging ensures that every configuration change, access event, or user action is traceable fostering a culture of responsibility and security best practices.
Gain complete visibility and control over your IT environment with NinjaOne’s powerful audit logging tools!
Track user actions, monitor system changes, and maintain compliance with ease—all through a secure, intuitive audit web interface. Whether you’re managing internal IT operations or supporting clients as an MSP, NinjaOne gives you the clarity and accountability you need to stay ahead of risks.
Use detailed audit trails to strengthen security, streamline investigations, and ensure full compliance with organizational and regulatory standards.
Audit Logging FAQs
What is audit logging?
Audit logging is the process of recording system or user activities to track what happened, who did it, when, and where. These logs help with security, compliance, troubleshooting, and forensic investigations. Common uses include detecting unauthorized access, meeting regulatory requirements, and analyzing system issues.
How audit logging works?
Audit logging records important system or user actions to track activity for security, compliance, and troubleshooting.
- Event Occurs: A user or system action happens (e.g., login, file access).
- Event Captured: Details like who, what, and when are recorded.
- Logged: The event is securely saved in an audit log file or database.
- Stored: Logs are kept locally or sent to a central server for protection and analysis.
- Monitored: Logs are reviewed to detect suspicious activity or troubleshoot issues.
- Alerted: Alerts notify admins of potential security threats.
Audit Logs vs. Regular System Logs, what is the difference?
Audit logs specifically track security-related events such as login attempts and file access, focusing on who performed what action, when, and where. They are primarily used for compliance, security monitoring, and forensic investigations and are typically enabled through specific audit policies. In contrast, regular system logs record general system events like system startups, errors, and hardware changes, focusing on overall system health and troubleshooting. These logs usually run by default and help diagnose system or application issues. While audit logs are structured to capture detailed user activity, regular system logs vary widely in format depending on their source.
Related Resources
MDM Audit Log Viewing
Easily track device activity with this guide to viewing MDM audit logs.
What Is A Compliance Audit?
Understand the essentials of a compliance audit and why it matters.
Patch Management Audit Checklist
