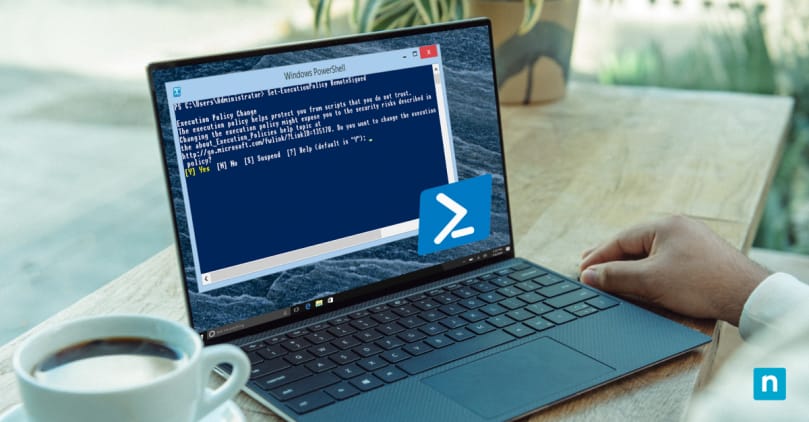
Developed by Microsoft, PowerShell has become a modern standard in Windows administration, scripting, and automation. Combining a command-line interface with a scripting language, PowerShell has transformed the Windows management landscape.
Based on the .NET framework, PowerShell integrates seamlessly with Microsoft technologies using concise commands, or cmdlets, to interact with system components, manipulate data, and automate administrative functions. This script-based approach enables users to streamline tasks, enhance efficiency, and automate common tasks. PowerShell also supports event handling, task scheduling, and remote management, offering a comprehensive solution for IT administrators, cybersecurity professionals, and scripting experts.
This guide focuses on PowerShell execution policies, explaining their importance, operation, management, impact on system security, and best practices. It seeks to provide an understanding of how these execution policies support effective script execution, and optimize system security in Windows environments.
What are PowerShell execution policies?
PowerShell execution policies function as a safeguard mechanism in Windows environments, determining the level of trust assigned to scripts before they are executed. These policies aim to strike a balance between enabling script execution for legitimate purposes and mitigating the potential security risks associated. By adhering to an execution policy, administrators can enforce a consistent and secure scripting environment, reducing the chances of malicious scripts compromising their systems.
The types of execution policies available are as follows:
- AllSigned: With this policy, all scripts, including those created locally, must be digitally signed by a trusted publisher to execute. This approach ensures that only authorized scripts are permitted to run, but does run the risk of running any malicious scripts that have been signed.
- Bypass: This policy permits the execution of any script without restriction. This policy should be used with extreme caution, if at all, as it can potentially expose systems to security risks by permitting the execution of unsigned and unverified scripts.
- Default: With this type of policy, the default execution is set. Default sets the execution policy as restricted for Windows clients, and RemoteSigned for Windows servers. Both types of execution policies are explained below.
- RemoteSigned: This policy requires that scripts downloaded from the internet be digitally signed for execution and be permitted. Locally created scripts can be executed without digital signature. This policy is considered by many to provide a pragmatic balance between usability and security.
- Restricted: This policy is the most secure available. It blocks the execution of all scripts, whether locally created or downloaded, and all script files. However, individual commands can be executed in the PowerShell environment.
- Undefined: This policy is used when no execution policy is explicitly set. It allows users to run scripts and offers flexibility, but it is best practice to select a specific policy to provide control and enhance security. If the policy is set as Undefined in all scopes, then it will automatically set the Default restrictions.
- Unrestricted: This policy grants unrestricted script execution, enabling both local and internet-sourced scripts to run without any restrictions. While convenient for development and testing, it should not be used in production environments owing to the significant security risks it represents.
Understanding these execution policies enables administrators and security professionals to adopt the approach that best fits the security requirements of their systems.
In the subsequent sections, we will explore the management, best practices, and implications of PowerShell execution policies.
Managing PowerShell execution policies
Setting and modifying PowerShell execution policies effectively is crucial to establishing a secure scripting environment. Administrators can use the Set-ExecutionPolicy cmdlet to configure these policies. By understanding the potential risks and benefits of different policy configurations, administrators can make informed decisions aligned with their security objectives.
The first consideration is execution policy scope, which offers the following options:
- MachinePolicy: This scope is set by Group Policy, and sees the execution policy applied to all users and processes on a machine, ensuring uniformity across the system. Local user policies can override this policy.
- UserPolicy: This scope is set by Group Policy, and enforces the execution policy for the users of a specific machine. It is particularly useful for maintaining a consistent scripting environment for all users.
- Process: At this scope, execution policies are defined for the current PowerShell session only. It allows for more granular control over script execution based on specific needs.
- CurrentUser: This scope enforces the execution policy for the current user’s session. It does not require any elevation of privileges.
- LocalMachine: This is the default scope, and allocating a policy to this scope impacts all users on a particular machine. If a user policy exists, it takes precedence over this scope.
Changes to execution policy have a direct impact on system security and script execution. A more restrictive policy, such as ‘Restricted’ or ‘AllSigned’ enhances security by reducing the risk of unauthorized or malicious scripts executing. This may, however, create a need for additional steps, such as signing scripts, which can introduce administrative overhead.
A more lenient policy, like ‘Unrestricted’ or ‘Bypass,’ streamlines script execution by removing barriers but comes at the cost of potentially exposing the system to security risks. Care should be taken when adopting such policies, and they should only be employed in controlled environments for time-limited periods, or during development and testing phases. Administrators must consider their organization’s security requirements and the specific needs of their users when selecting and modifying execution policies. Striking the right balance between security and functionality ensures that the PowerShell scripting environment remains secure.
In the following sections, we look at the best practices associated with PowerShell execution policies, common issues faced while managing them, and their alignment with organizational security guidelines. These insights will empower administrators and security professionals to make informed decisions in their pursuit of a secure and efficient scripting environment.
PowerShell execution policy best practices
When selecting a PowerShell execution policy for different environments, it is best practice to consider the nature of the scripts that will be executed, the level of security required, and the role of the users. For example:
- Production environment: In a production environment, it is prudent to adopt a more restrictive policy like ‘AllSigned’ or ‘RemoteSigned.’ This ensures that scripts are signed and authenticated before execution and reduces the risk of unauthorized or malicious code.
- Development environment: In a development environment, a more flexible policy like ‘Bypass’ or ‘Unrestricted’ may be used to facilitate testing and troubleshooting. However, these policies should not be carried over to production environments.
How to safely manage and change policies
As IT administrators, cybersecurity professionals, and individuals involved in Windows administration and PowerShell scripting, it is crucial to appreciate how to safely manage these policies.
Best practices for managing and altering PowerShell execution policies include:
- Document execution policies: Ensure that administrators and users understand the implications of different execution policies. Create clear documentation outlining which policies are appropriate for specific scenarios.
- Mandate script signing: For more restrictive policies like ‘AllSigned’ and ‘RemoteSigned,’ enforce the practice of signing scripts using digital signatures. This adds an extra layer of security by ensuring the authenticity of scripts.
- Select the least permissive scope: Determine the appropriate scope for setting execution policies. Be mindful of the impact on users and processes within different scopes, as well as the impact on system security and alignment with security policy. Selecting the policy that offers least privilege while providing the function required is best practice.
- Review policies: Regularly review and audit execution policies across the environment. Ensure that policies remain aligned with security requirements and organizational guidelines.
Common issues and solutions
Setting PowerShell execution policies can often lead to challenges impacting script and system operations. Some common issues include:
- Access Denied: Users might encounter “Access Denied” errors when trying to change execution policies due to lack of administrative privileges.
- Blocked scripts: More restrictive policies like ‘AllSigned’ can prevent the execution of unsigned or improperly signed scripts, causing frustration for users.
- Untrusted scripts: Scripts from the internet might be blocked by policies like ‘RemoteSigned,’ even if they are safe and legitimate.
To address these issues and ensure successful script execution, follow these troubleshooting steps:
- Elevate privileges: Ensure that you have administrative privileges when changing execution policies. Run PowerShell with administrative rights by right-clicking and selecting “Run as Administrator.”
- Script signing: When using policies like ‘AllSigned,’ ensure that scripts are properly signed using valid digital signatures. This prevents false “Access Denied” errors.
- Trust publishers: For ‘AllSigned’ and ‘RemoteSigned’ policies, establish trust with publishers by importing their certificates into the Certificate store.
- Unblock files: If a script file was downloaded from the internet and is blocked, unblock it using the ‘Unblock-File’ cmdlet.
- Check for scope issues: Be mindful of the execution policy scope. If encountering issues, ensure that the policy is set at the appropriate scope level.
- Check for group policy restrictions: In domain environments, Group Policies may enforce specific execution policies. Verify the Group Policy settings that apply to the system, as well as its location.
- Use PowerShell remoting: In case of ‘Restricted’ or ‘AllSigned’ policies blocking local execution, utilize PowerShell remoting to execute scripts on remote systems.
- Check security software: Some security software may interfere with script execution. Temporarily disable or adjust settings to troubleshoot.
- Check for conflicts: Be aware of potential conflicts between local and Group Policy settings. Ensure consistency in execution policy enforcement.
As always, a process of elimination approach should reveal the root of an issue. If a failing script works with elevated rights, delve deeper into permissions. If it works with a policy bypass, check machine restrictions, and so on. By addressing these common problems and following the troubleshooting steps above, administrators and professionals can effectively manage PowerShell execution policies, preventing roadblocks in script execution and maintaining a secure scripting environment.
Aligning with organizational security guidelines
Aligning Windows PowerShell execution policies with organizational security guidelines is vital for maintaining a secure and controlled scripting environment. Organizations often have specific security requirements and policies that dictate how scripts should be executed. By aligning execution policies with these guidelines, organizations can ensure consistency, reduce risks, and enhance overall security posture.
The Importance of regular audits and policy review
Regular audits and policy reviews ensure that execution policies remain effective and up to date. As organizational needs evolve and security threats change, execution policies may need adjustments.
Conducting periodic reviews allows organizations to:
- Adapt to a changing threat landscape: The cybersecurity landscape is dynamic. Regular policy reviews help organizations stay ahead of emerging threats and adjust policies accordingly.
- Evaluate policy effectiveness: Organizations can assess whether the current execution policies are effectively mitigating risks or if adjustments are necessary.
- Ensure compliance: Compliance requirements may change over time. Regular reviews help ensure that execution policies align with current compliance standards.
- Identify policy conflicts: In complex environments, policy conflicts or unintended side effects can occur. Regular audits help identify and resolve such issues.
- Maintain consistency: Over time, new scripts and users might be introduced. Audits help ensure that execution policies are consistently applied across the organization.
- Mitigate unauthorized scripts: Regular reviews can help identify and address unauthorized or malicious scripts that may exist in production undetected.
With a well-defined and consistently enforced execution policy strategy, organizations can harness the power of PowerShell scripting while maintaining a robust security posture.
PowerShell execution policies: A fundamental pillar of system security
Considered use of PowerShell execution policies is a fundamental pillar of system security, and effective Windows administration. These policies serve as gatekeepers for script execution, acting as the safeguards that ensure only authorized and trusted scripts run within an environment. By establishing boundaries on script execution, organizations can limit the potential for malicious or inadvertent code to compromise their systems. The range of execution policies available, each designed for a specific security use case, demonstrates the granular control administrators possess over script execution behavior.
PowerShell execution policies go beyond configuration rules and settings; they represent a commitment to consistent and secure IT operations. By adhering to the PowerShell execution policy best practices we’ve introduced, you are well on your way to a secure, efficient, and resilient Windows environment.