Freshen up on remote access best practices for managing secure remote access and remote desktop solutions with tools like Connectwise ScreenConnect, Splashtop, TeamViewer, and RDP.
Easily one of the largest leaps in IT management came about through the advent of remote access technologies. There was a time when monitoring and maintaining an IT infrastructure — including all of the software, endpoints, servers, printers, and user accounts — meant time on-site, physical access, and a lot of driving around.
This has all changed thanks to remote access software, which allows even the most complicated of tasks to be quickly and efficiently handled from afar. IT companies and managed services providers (MSPs) rely on remote computer access to quickly diagnose and resolve end-user issues, deploy critical software updates, and track network assets and inventory. In-house IT teams and IT managers rely on remote access for maximizing their productivity, managing multiple locations, and allow them to work from home or while on the road.
Perhaps most importantly, the ability to monitor systems remotely means both MSPs and IT managers are able to support the IT needs of their stakeholders around the clock, rain or shine, every day.
Before we get ahead of ourselves, let’s put a definition on “remote access.”
What is remote access, and what is its role in IT support?
Remote access is a blanket term used to describe the ability to access a specific computer system from any location via a network connection. Many computer users have experienced this when they’ve called tech support to fix a problem and had the technician on the phone take control of their computer.
While remote access does serve a few purposes on the end-user side of things — facilitating document or file sharing within an organization, for instance — it plays a much more central role in IT support.
Along with remote monitoring and management (RMM) software, remote access is a big reason why even small teams of technicians can support large numbers of clients and end-users. It empowers them to perform system configurations, maintenance, troubleshooting, and patch management for far more people than they would be able to handle if they were still driving on-site.
Increased need for secure remote access options
With the explosion in the need for flexible, remote working environments, many organizations have found themselves with users, devices, and critical operations spread out all over their regions. Without remote monitoring and remote access capabilities, it would be nearly impossible to manage this new breed of workforce.
Many organizations who were forced to provide end-users with remote access options quickly may also have done so haphazardly and inadvertently introduced additional threat vectors for security breaches, lost data, and network interruptions that can cost their company time and money.
That’s why it’s extremely important to leverage both secure remote access tools AND providers who have experience deploying, configuring, and managing them securely.
Top 3 requirements and criteria for choosing a remote access solution
Remote access solutions are not all the same, even though their core purpose seems fairly simple. As with many types of software, certain options may fit your company’s needs better than others. Here are some of the most important criteria to consider when selecting a tool.
Security
When considering any remote access tool, security obviously cannot be understated. Software purposefully designed to provide remote access to devices is powerful and, in many cases, essential, but it also carries a substantial amount of risk.
Solutions should be vetted for their adherence to security and compliance standards, and there should be clear documentation and resources available to ensure you can deploy and configure it securely.
Features designed to provide clear access controls and logging are also a must.
Ease of use
What’s the #1 reason UI is important? If remote access is easy to use, it will get used. If it’s not, it won’t. And that opens up the possibility of end-users searching out and utilizing unsupported alternatives.
Reliability
Remote access is such an important part of modern IT management, you really don’t want to face a day without it. The reliability of your remote tools, remote access included, translates directly to the overall reliability and robustness of your IT infrastructure.
Remote access best practices: Features and benefits to utilize
When used with remote management best practices, the right remote access solution can solve a very direct and critical need for organizations. If used appropriately, it can also eliminate the need for extraneous tools and save companies money in the long run (i.e. no need to keep paying for LogMeIn subscriptions).
What features should you be leveraging to get the most out of remote access?
- Multi-monitor support allowing one technician to access multiple endpoints.
- Multiple sessions enabling each tech to open several sessions on the same endpoint.
- Connection security to provide enhanced defense against being tapped into by snoopers. This is important as most remote connections are carried over the public and unencrypted lines of the internet.
- Collaborative access functionality which allows multiple technicians to work on the same endpoint and communicate easily with each other as they work.
- Access privilege controls to establish access rights to supported devices and handle permissions as seamlessly as possible. Without this, technicians won’t be able to work on hardware which is unattended.
- User communication channels that offer easy, integrated communication between the technician and the end user. (This is typically a text-based chat system or a voice communication channel.)
- File transfer utility which allows techs to easily copy files to and from the remote device.
- Live desktop viewer functionality is essential for Help Desk technicians in the cases where they need to see what the user can see in order to resolve the problem.
- End-monitor blackout mode for technicians who are fixing a problem via remote and need to remove the view of the Desktop from the user during the session.
- Access and process automation which allows technicians to script repetitive tasks and apply bulk fixes to numerous endpoints using automation.
- Access to and from mobile devices is more important than ever. Support technicians need to be able to work in any environment at any time, and likewise, they may often need to access mobile devices to resolve issues for remote workers.
- Session logging ensures that the actions performed by the technician on the remote computer are recorded for security and change logging.
- RMM integrations to save time and remove the need for technicians to have several different tools open at once. Systems that can automatically log session time help to automate billing procedures, and are generally more secure and reliable.
A quick note re: RDP (Remote Desktop Protocol)
Remote Desktop Protocol (RDP) has become very useful in this growing age of remote workplaces. RDP is a Windows protocol that allows remote employees to see and use the operating system on a device in another location. In other words, a user sitting at home can log in via an internet connection to their office desktop and use it just as though they’re sitting at their desk.
Remote Desktop allows workers to access specific device data from anywhere in the world, making them more productive and keeping the organization’s data more secure.
RDP is built into Windows but needs to be configured properly to be utilized securely. Organizations should be informed that unsecured RDP access is an extremely common attack vector, and a favorite of ransomware groups, in particular. Therefore, RDP should never be exposed to the Internet.
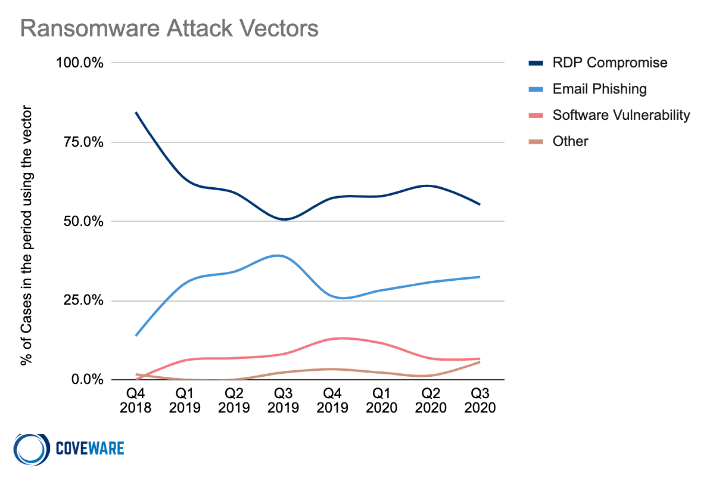
Source: Coveware’s Q3 Ransomware Trends Report
For more on secure RDP, see this post from UC Berkeley.
Remote access integrations from NinjaOne
NinjaOne offers several native integrations for remote access, empowering our partners with all of the above benefits of remote access while maintaining a secure, simple user experience.
Our Teamviewer integration is a single-pane of glass experience which enables Teamviewer best practices through secure remote access, end-user sharing, user chat, file transfers, session recording, and numerous other great features of the Teamviewer software.
Splashtop’s remote access solution was designed specifically for MSPs and IT professionals. The NinjaOne Splashtop integration enables Splashtop best practices through one-click remote access, file transfers, user chat, remote audio/video communication, and detailed connection reports.
NinjaOne’s Connectwise ScreenConnect integration allows partners to use one of the most popular remote access solutions directly within Ninja while maintaining full access to Control’s functionality, reporting, and interface.
NinjaOne also opens up a completely customizable user experience for RDP, giving you complete control over remote Windows access and following remote desktop best practices. Our secure RDP remote control solution includes automated provisioning of endpoints for RDP access, credential exchange integration for administrative privileges, dynamic graphics settings based on connection performance, and single- or multi-screen viewing.
Experience NinjaOne’s remote access options yourself by starting a free trial today.