Seamless Ransomware Recovery with NinjaOne
Experience tranquility with NinjaOne’s Ransomware Recovery solution. This solution is engineered to counteract data disruption and extortion.
It achieves this by leveraging easily restorable backups, which allow for a swift resumption of operations. This minimizes downtime and strengthens your defenses against ransomware threats
Rest assured, your data is in safe hands with NinjaOne.
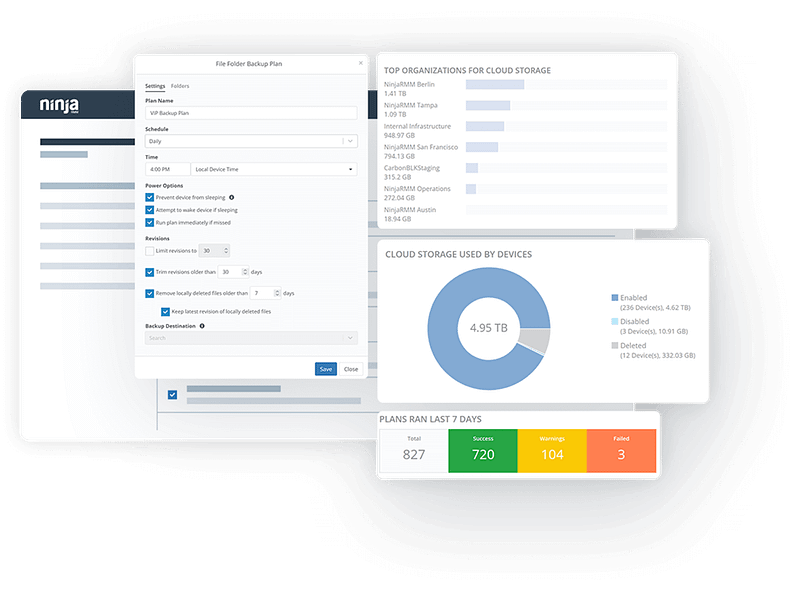
Ensure data resilience with NinjaOne's Ransomware Recovery Benefits
Adaptable Backup Solutions
NinjaOne offers cloud-based, hybrid, and customizable backup plans that are designed to fit any business need. It also provides the ability to store your data locally or offsite in the cloud and can backup both Windows and Mac endpoints.
Robust Data Security Measures
NinjaOne safeguards your data with backups that are encrypted in transit and at rest in the cloud and locally. It requires re-authentication and confirmation to delete previous backup files, ensuring your backups are resistant to ransomware.
Swift and Efficient Recovery
NinjaOne enables businesses to perform a full system restore to the same device, bare metal restores to new hardware, or manual file/image restoration to another device. This significantly reduces Recovery Time Objectives (RTO) and ensures business continuity.
NinjaOne’s ransomware recovery solution is packed with features designed to provide enhanced cyber threat protection
Automated Backup Scheduling
NinjaOne allows for automatic backups at regular intervals, ensuring data is consistently backed up without manual intervention, enhancing data protection.
Proactive Alerting
Advanced alerting capabilities promptly notify users of any irregularities, enabling proactive responses to potential threats.
Flexible Backup Plan
NinjaOne offers cloud-based, hybrid, and customizable backup plans tailored to fit diverse business needs, ensuring data protection and seamless recovery.
Secure Backups
Encrypted backups at rest and in transit, multi-factor authentication, and revokable authorization keys protect data from ransomware attacks, enhancing security.
Effortless Restore Options
NinjaOne provides various restore options like web-based file restores, bare metal restores, and active-endpoint image restores for swift data recovery.
System Restore Capabilities
NinjaOne’s system restore features enable rapid disaster recovery, offering full system restores, bare-metal restores, and manual file/image restoration to ensure business continuity and minimize Recovery Time Objectives (RTO)
NinjaOne’s ransomware recovery solution is versatile and can be used in a variety of scenarios
Supporting a Distributed Workforce
In the era of remote work, businesses are dealing with a distributed workforce operating from various locations. NinjaOne’s ransomware backup and recovery solution, a key component of disaster recovery ransomware strategies, is designed to cater to this new work model.
It offers cloud-based, hybrid, and customizable backup plans that ensure data protection across all endpoints, regardless of their geographical location.
This means that no matter where your employees are working from, their data is always protected.
Recovering from Ransomware Attacks
Ransomware incidents are on the rise, posing severe threats to business continuity. NinjaOne offers a robust ransomware backup and recovery system, strategically crafted to aid businesses in bouncing back from such assaults.
The solution fortifies data integrity through encrypted backups, coupled with a stringent re-authentication protocol and confirmation mechanism for the deletion of prior backup files.
These measures significantly enhance resilience against ransomware, enabling prompt restoration of data to mitigate operational disruptions. This functionality proves invaluable amidst ransomware attacks, empowering businesses to swiftly retrieve critical data and resume operations.
Ensuring Business Continuity
Business continuity is crucial for any organization. Any disruption in operations can lead to significant financial losses and damage to the company’s reputation.
NinjaOne’s ransomware backup and recovery solution is an essential tool for ensuring business continuity. It offers several secure restore options, including web-based file restores, bare metal restores, and active endpoint image restores.
This ensures a quick recovery and continuation of business operations post-attack. This feature is particularly useful for businesses that need to ensure continuity even in the face of cyber threats.
Protect your business from the devastating effects of ransomware attacks!
With NinjaOne Ransomware Recovery, you can safeguard your data, minimize downtime, and ensure business continuity. Don’t wait until it’s too late — secure your peace of mind today.
Ransomware Recovery FAQs
What is ransomware recovery?
Ransomware recovery refers to the procedures undertaken to restore operations after a cyber incident where a payment is demanded to decrypt data. This process includes implementing various strategies to recover essential systems and data from backups or alternative sources post ransomware attack.
Now, let’s delve into how ransomware data recovery works. The process usually initiates prior to an attack occurring. Companies adhering to the 3-2-1 backup rule are well-prepared for recovery. This rule entails having three data copies, stored on at least two diverse media types, with one copy located offsite or offline.
During a ransomware attack, recovery involves executing an incident response plan with immediate steps and long-term actions to prevent further attacks. This includes data collection, stakeholder communication, legal compliance, business continuity, and attack remediation. Despite not paying the ransom, downtime costs can be devastating due to lost revenue and reputation damage. Hence, quick recovery is crucial, and a robust disaster recovery plan and data backups are key to successful recovery.
How to recover from a ransomware attack?
Recovering from a ransomware attack involves a multifaceted process primarily centered on how to recover files from ransomware attack.
- Begin by isolating and containing the attack: disconnect infected devices and halt shared drive or cloud connections.
- Identify the ransomware variant to explore decryption tools or enlist cybersecurity experts if needed. Promptly report the incident to your IT or cybersecurity team for coordinated response.
- Restore systems and data from clean backups taken before the attack, prioritizing critical assets. Strengthen security postures by patching vulnerabilities, updating security software, and reinforcing employee training. Implement advanced security measures like endpoint protection, intrusion detection, and network segmentation to thwart future attacks.
- Regularly educate staff on cybersecurity and monitor for signs of reinfection. Test backup and recovery processes routinely to ensure reliability.
Following these steps fortifies defenses and facilitates recovery from ransomware attacks.
What is a ransomware recovery plan?
A ransomware recovery plan is a comprehensive strategy developed by organizations to effectively respond to and recover from a ransomware attack.
This plan typically outlines a series of steps and procedures to follow in the event of an attack, including isolating infected systems, identifying the ransomware variant, assessing the impact on data and systems, restoring from backups, and implementing security measures to prevent future incidents.
The plan may also include protocols for communication with internal stakeholders, law enforcement, and cybersecurity experts, as well as guidelines for employee training and awareness.
The primary goal of a ransomware recovery plan is to minimize the impact of an attack, restore operations as quickly as possible, and strengthen defenses against future threats.
How long does it take to recover from a ransomware attack?
The duration of recovery from a ransomware incident differs based on various factors such as the severity of the attack, extent of damage, availability of backups, and the effectiveness of response strategies. While some entities might swiftly recover within days, others could face extended periods of restoration, potentially lasting weeks or even months, particularly if vital systems are compromised or backup options are limited. It highlights the importance of having a robust and tested recovery plan in place to expedite restoration efforts and mitigate the impact of ransomware attacks.
What are the best practices for ransomware attack recovery?
To mitigate the damage from ransomware incidents and expedite the restoration process, organizations should adopt a dual approach of preemptive actions and effective response plans.
It is critical to regularly create backups of vital data, ensuring they are kept in a secure environment and are subject to periodic validation to confirm their reliability for use in recovery scenarios. Organizations are also advised to fortify their digital infrastructure with comprehensive cybersecurity protocols, including the deployment of firewalls, antivirus programs, and systems for detecting intrusions, to thwart the initial penetration of ransomware.
Should an attack occur, immediate steps must be taken to quarantine the impacted systems to halt the ransomware’s propagation. Organizations must then conduct a detailed evaluation to ascertain the extent and gravity of the breach, pinpointing the affected systems and data. This evaluation is instrumental in setting the priorities for the recovery process and selecting the most fitting course of action. Depending on the circumstances, options may include restoring data from backups, employing decryption solutions when accessible, or consulting with cybersecurity specialists to navigate more intricate recovery operations.
Effective communication with all relevant parties, such as staff, clientele, and business associates, is vital throughout the recovery phase to align expectations and preserve confidence. After the successful reinstatement of systems, it is imperative for organizations to perform an exhaustive post-incident analysis to extract valuable insights and apply enhanced protective measures to safeguard against subsequent attacks. Adherence to these recommended practices enables organizations to not only rebound from ransomware attacks but also to bolster their overall security posture against looming threats.
Related Resources
Hard Drive Data Recovery: How to Recover Data From a Dead Hard Drive
Discover how hard drives recover data, provide ample storage capacity, portability, high performance, and convenient data access.
Ransomware Backup: How to Prevent Disaster
Learn how ransomware backup ensures quick and simple data recovery, and enables your organization to swiftly resume operations.
Must-Know Ransomware Statistics, Trends and Facts
Delve into today’s ransomware statistics and learn strategies to enhance your business’s protection.


